Cybercrime
You may not always stop your personal information from ending up in the internet’s dark recesses, but you can take steps to protect yourself from criminals looking to exploit it
29 Oct 2024
•
,
6 min. read

How did 44% members of the European Parliament (MEPs) and 68% of British MPs let their personal details end up circulating on the dark web? The answer is simpler and possibly more alarming than you may think: many will have signed up to online accounts using their official email address, and entered additional personally identifiable information (PII). They will then have been helpless as that third-party provider was breached by cybercriminals, who subsequently shared or sold the data to other threat actors on the dark web.
Unfortunately, this is not something confined to politicians or others in the public eye and it’s not the only way one’s data can end up in the internet’s seedy underbelly. It could happen to anyone – possibly even when they do everything correctly. And frequently, it does happen. That’s why it pays to keep a closer eye on your digital footprint and the data that matters most to you.
The dark web is thriving
First things first: Contrary to popular assumption, the dark web is not illegal and it’s not populated solely by cybercriminals. It merely refers to parts of the internet that aren’t indexed by traditional search engines: a place where users can roam anonymously using Tor Browser.
However, it’s also true to say that today’s cybercrime economy has been built on a thriving dark web, with many of the dedicated forums and marketplaces visited by cybercriminals in their droves while being hidden from law enforcement. (That said, some of the nefarious activities have increasingly been spilling onto well-known social media platforms in recent years.)
As an enabler for a criminal economy worth trillions, the dark web sites allow threat actors to buy and sell stolen data, hacking tools, DIY guides, service-based offerings and much more – with impunity. Despite periodic crackdowns by law enforcement, these sites continue to adapt, with new platforms emerging to fill the gaps left as previous incumbents are dismantled by the authorities.
When Proton and Constella Intelligence researchers went looking, they found that a staggering two-fifths (40%) of British, European and French parliamentarians’ email addresses were exposed on the dark web. That’s nearly 1,000 out of a possible 2,280 emails. Even worse, 700 of these emails had passwords associated with them stored in plain text and exposed on dark web sites. When combined with other exposed information including dates of birth, home addresses, and social media account handles, they provide a treasure trove of identity data that can be used in follow-on phishing attacks and identity fraud.
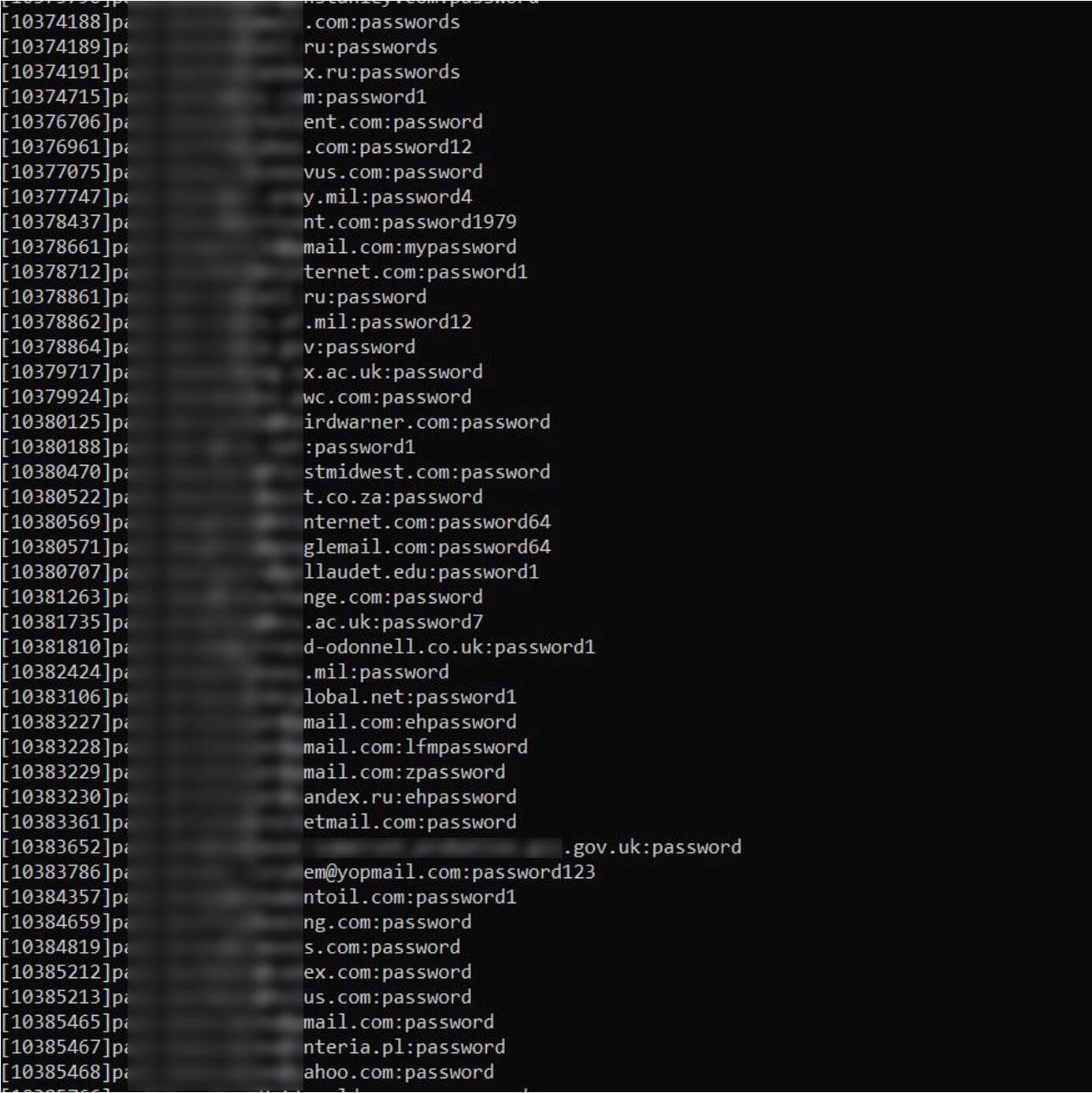
How does my data end up on the dark web?
There are various ways your own data could end up in a dark web forum or site. Some may be the result of negligence while many others are not. Consider the following:
- Data breaches at third-party organizations: Your data is stolen from an organization you have done business with, and which has collected your data, in the past. In the US, 2023 was a record year for data compromises of this type: More than 3,200 incidents at organizations led to the compromise of data belonging to over 353 million customers.
- Phishing attacks: One of your online accounts (e.g., email, bank, social media) is compromised via a phishing attack. A legitimate-looking email, direct message, text or WhatsApp contains a link which may install info-stealing malware or trick you into entering your personal and/or log-in details (i.e., a spoofed login page for Microsoft 365).
- Credential stuffing: An online account is compromised via a brute-force attack. (credential stuffing, dictionary attack, etc.) where hackers guess your password or use previously breached logins across other sites. Once inside your account, they steal more personal information stored in there to sell or use.
- Info-stealing malware: Your personal data is stolen via information-stealing malware that could be hidden in legitimate-looking apps and files for download (such as pirated movies/games), phishing attachments, malicious ads, websites etc.
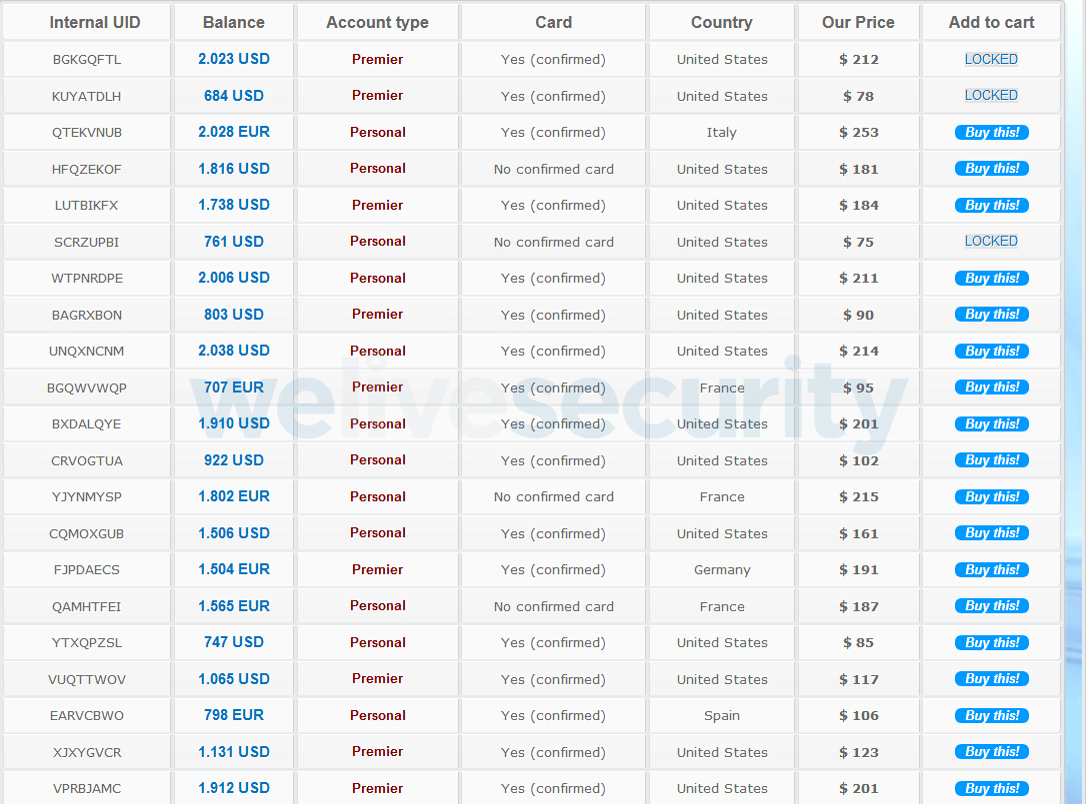
 However the bad guys get hold of your data, once it’s shared on a dark web cybercrime site it could then be given away or sold to the highest bidder. Depending on the type of data, whomever gets hold of it will likely use those logins and PII to:
However the bad guys get hold of your data, once it’s shared on a dark web cybercrime site it could then be given away or sold to the highest bidder. Depending on the type of data, whomever gets hold of it will likely use those logins and PII to:
- Hijack your bank accounts to steal more information including bank/card details.
- Design more convincing phishing messages which share some of the stolen PII in a bid to persuade you to hand over more.
- Steal your email or social media accounts to spam friends and address book contacts with malicious links.
- Commit identity fraud; e.g., taking out new lines of credit in your name, generating false tax returns in order to receive a refund, or illegally receiving medical services.
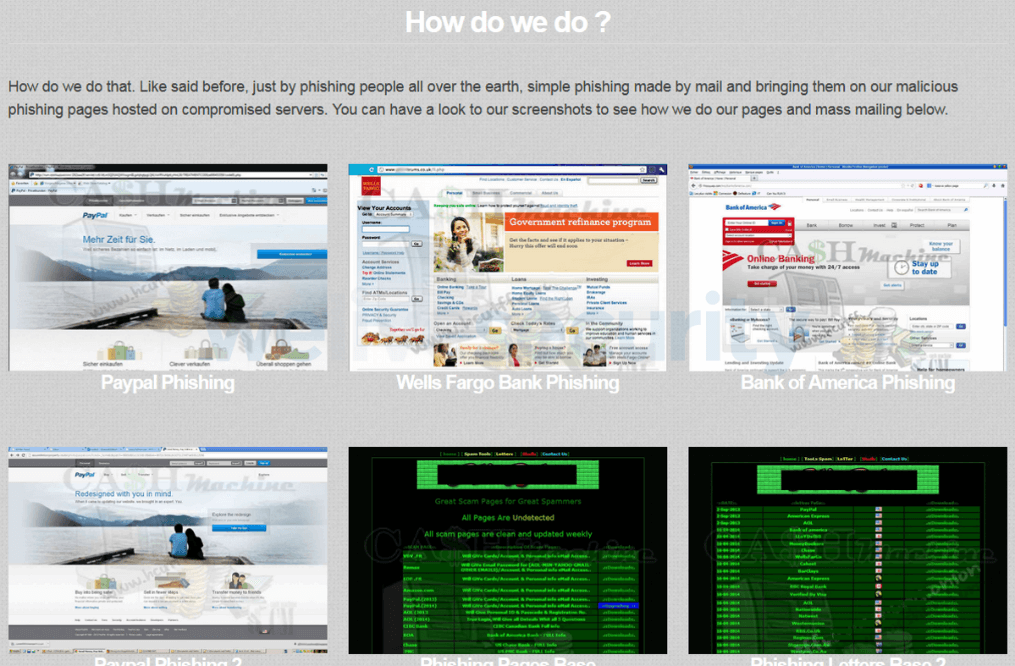
How do I check?
If you’re signed up to an identity protection or dark web monitoring service, it should flag any PII or other data it finds on the dark web. Tech companies, including Google and Mozilla, will also alert you when a saved password has been found in a data breach, or may require updating to a more secure, harder-to-guess version.
Importantly, dark web monitoring is often also part of a range of services provided by security vendors, whose products obviously come with many other benefits and are a critical component of your personal security stack.
Alternatively, you could proactively visit a site like HaveIBeenPwned, which has compiled large lists of breached email addresses and passwords that can be securely queried.
What do I do if my data has been stolen?
If the worst happens and, like a British politician, you find your data has been exposed and is being traded on the dark web, what happens next? In the short term, consider taking emergency steps such as:
- Change all your passwords, especially the affected ones, to strong, unique credentials
- Use a password manager to store and recall your saved passwords and passphrases
- Switch on two-factor authentication (2FA) on all accounts that offer it
- Notify the relevant authorities (law enforcement, social media platform, etc.)
- Ensure all of your computers and devices have security software installed from a reputable vendor.
- Freeze your bank accounts (if relevant) and ask for new cards. Monitor them for any unusual purchases.
- Look out for other unusual activity on accounts such as being unable to login, changes to security settings, messages/updates from accounts you don’t recognize or logins from strange locations and strange times.
Staying safe in the long-term
To avoid being hit in the future, consider:
- Being more wary of oversharing information online.
- Revisiting the security/privacy settings of your social media accounts.
- Turning on ‘stealth mode’; i.e., when appropriate, use options such as disposable email addresses so you don’t always have to give away your personal details.
- Never replying to unsolicited emails, messages or calls – especially those that try to hurry you into taking action without thinking clearly first.
- Use strong and unique passwords on all accounts that offer it and enable a strong form of 2FA for added protection.
- Investing in a dark web monitoring service that will alert you to newly-found personal details in the internet’s seedy underbelly and potentially enable you to take action before cybercriminals can monetize the data.
It’s not much fun having your personal information and/or identity stolen. It can be a traumatic, stressful experience which may last weeks or months before a resolution. See what’s lurking out there on the dark web right now and it may never get to that stage.
