A new phishing campaign codenamed MULTI#STORM has set its sights on India and the U.S. by leveraging JavaScript files to deliver remote access trojans on compromised systems.
“The attack chain ends with the victim machine infected with multiple unique RAT (remote access trojan) malware instances, such as Warzone RAT and Quasar RAT,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said.
“Both are used for command-and-control during different stages of the infection chain.”
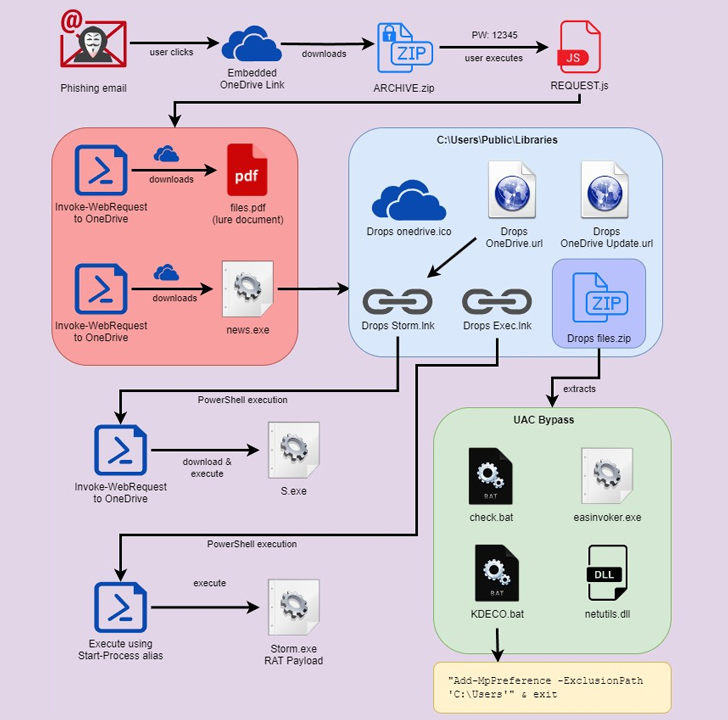
The multi-stage attack chain commences when an email recipient clicks the embedded link pointing to a password-protected ZIP file (“REQUEST.zip”) hosted on Microsoft OneDrive with the password “12345.”
Extracting the archive file reveals a heavily obfuscated JavaScript file (“REQUEST.js”) that, when double clicked, activates the infection by executing two PowerShell commands that are responsible for retrieving two separate payloads from OneDrive and executing them.
The first of the two files is a decoy PDF document that’s displayed to the victim while the second file, a Python-based executable, is stealthily run in the background.
The binary acts as a dropper to extract and run the main payload packed inside it in the form of Base64-encoded strings (“Storm.exe”), but not before setting up persistence via Windows Registry modification.
Also decoded by the binary is a second ZIP file (“files.zip”) that contains four different files, each of which is designed to bypass User Account Control (UAC) and escalate privileges by creating mock trusted directories.
Among the files is a batch file (“check.bat”) that Securonix said shares several commonalities with another loader called DBatLoader despite the difference in the programming language used.
A second file named “KDECO.bat” executes a PowerShell command to instruct Microsoft Defender to add an antivirus exclusion rule to skip the “C:Users” directory.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
The attack culminates with the deployment of Warzone RAT (aka Ave Maria), an off-the-shelf malware that’s available for sale for $38 per month and comes with an exhaustive list of features to harvest sensitive data and download additional malware such as Quasar RAT.
“It’s important to remain extra vigilant when it comes to phishing emails, especially when a sense of urgency is stressed,” the researchers said.
“This particular lure was generally unremarkable as it would require the user to execute a JavaScript file directly. Shortcut files, or files using double extensions would likely have a higher success rate.”