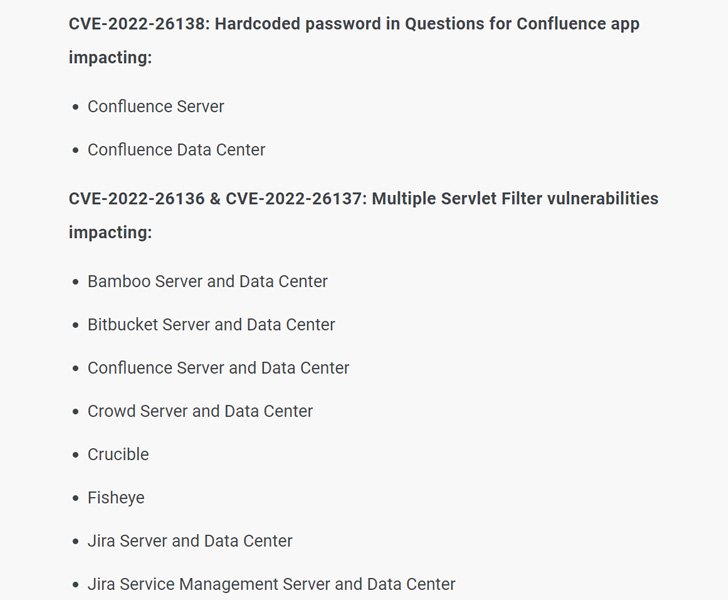
A week after Atlassian rolled out patches to contain a critical flaw in its Questions For Confluence app for Confluence Server and Confluence Data Center, the shortcoming has now come under active exploitation in the wild.
The bug in question is CVE-2022-26138, which concerns the use of a hard-coded password in the app that could be exploited by a remote, unauthenticated attacker to gain unrestricted access to all pages in Confluence.
The real-world exploitation follows the release of the hard-coded credentials on Twitter, prompting the Australian software company to prioritize patches to mitigate potential threats targeting the flaw.
“Unsurprisingly, it didn’t take long […] to observe exploitation once the hard-coded credentials were released, given the high value of Confluence for attackers who often jump on Confluence vulnerabilities to execute ransomware attacks,” Rapid7 security researcher Glenn Thorpe said.
It’s worth noting that the bug only exists when the Questions for Confluence app is enabled. That said, uninstalling the Questions for Confluence app does not remediate the flaw, as the created account does not get automatically removed after the app has been uninstalled.
Users of the affected product are advised to update their on-premise instances to the latest versions (2.7.38 and 3.0.5) as soon as possible, or take steps to disable/delete the account.
The development also arrives as Palo Alto Networks, in its 2022 Unit 42 Incident Response Report, found that threat actors are scanning for vulnerable endpoints within 15 minutes of public disclosure of a new security flaw.