Details have emerged about a recently patched critical remote code execution vulnerability in the V8 JavaScript and WebAssembly engine used in Google Chrome and Chromium-based browsers.
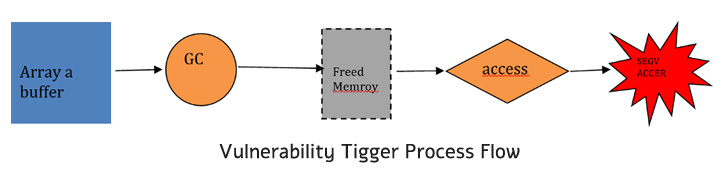
The issue relates to a case of use-after-free in the instruction optimization component, successful exploitation of which could “allow an attacker to execute arbitrary code in the context of the browser.”
The flaw, which was identified in the Dev channel version of Chrome 101, was reported to Google by Weibo Wang, a security researcher at Singapore cybersecurity company Numen Cyber Technology and has since been quietly fixed by the company.
“This vulnerability occurs in the instruction selection stage, where the wrong instruction has been selected and resulting in memory access exception,” Wang said.
Use-after-free flaws occur when previous-freed memory is accessed, inducing undefined behavior and causing a program to crash, use corrupted data, or even achieve execution of arbitrary code.
What is more concerning is that the flaw can be exploited remotely via a specially designed website to bypass security restrictions and run arbitrary code to compromise the targeted systems.
“This vulnerability can be further exploited using heap spraying techniques, and then leads to ‘type confusion’ vulnerability,” Wang explained. “The vulnerability allows an attacker to control the function pointers or write code into arbitrary locations in memory, and ultimately lead to code execution.”
The company has not yet disclosed the vulnerability via the Chromium bug tracker portal to give as many users as possible to install the patched version first. Also, Google does not assign CVE IDs for vulnerabilities found in non-stable Chrome channels.
Chrome users, especially developers who use the Dev edition of Chrome for testing to ensure that their applications are compatible with the latest Chrome features and API changes, should update to the latest available version of the software.
 |
| TurboFan assembly instructions after vulnerability patched |
This is not the first time use-after-free vulnerabilities have been discovered in V8. Google in 2021 addressed seven such bugs in Chrome that have been exploited in real-world attacks. This year, it also fixed an actively exploited use-after-free vulnerability in the Animation component.