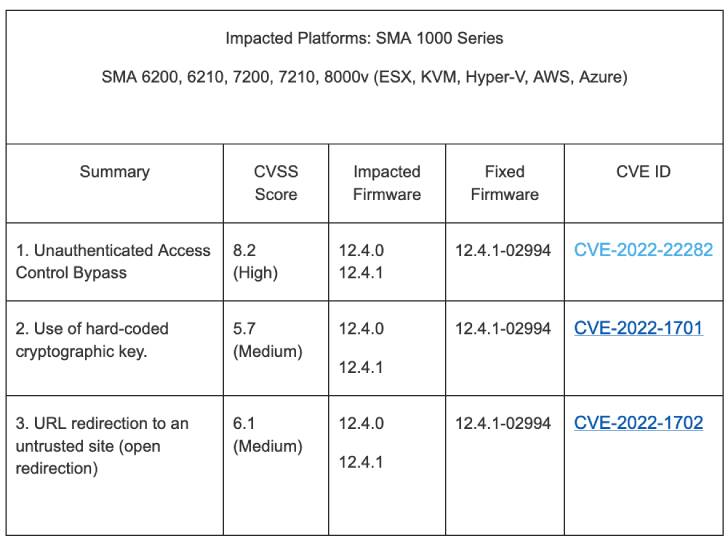
SonicWall has published an advisory warning of a trio of security flaws in its Secure Mobile Access (SMA) 1000 appliances, including a high-severity authentication bypass vulnerability.
The weaknesses in question impact SMA 6200, 6210, 7200, 7210, 8000v running firmware versions 12.4.0 and 12.4.1. The list of vulnerabilities is below –
- CVE-2022-22282 (CVSS score: 8.2) – Unauthenticated Access Control Bypass
- CVE-2022-1702 (CVSS score: 6.1) – URL redirection to an untrusted site (open redirection)
- CVE-2022-1701 (CVSS score: 5.7) – Use of a shared and hard-coded cryptographic key
Successful exploitation of the aforementioned bugs could allow an attacker to unauthorized access to internal resources and even redirect potential victims to malicious websites.
Tom Wyatt of the Mimecast Offensive Security Team has been credited with discovering and reporting the vulnerabilities.
SonicWall noted that the flaws do not affect SMA 1000 series running versions earlier than 12.4.0, SMA 100 series, Central Management Servers (CMS), and remote access clients.
Although there is no evidence that these vulnerabilities are being exploited in the wild, it’s recommended that users apply the fixes in the light of the fact that SonicWall appliances have presented an attractive bullseye in the past for ransomware attacks.
“There are no temporary mitigations,” the network security company said. “SonicWall urges impacted customers to implement applicable patches as soon as possible.”