Cybersecurity researchers have shed light on an actively maintained remote access trojan called DCRat (aka DarkCrystal RAT) that’s offered on sale for “dirt cheap” prices, making it accessible to professional cybercriminal groups and novice actors alike.
“Unlike the well-funded, massive Russian threat groups crafting custom malware […], this remote access Trojan (RAT) appears to be the work of a lone actor, offering a surprisingly effective homemade tool for opening backdoors on a budget,” BlackBerry researchers said in a report shared with The Hacker News.
“In fact, this threat actor’s commercial RAT sells at a fraction of the standard price such tools command on Russian underground forums.”
Written in .NET by an individual codenamed “boldenis44” and “crystalcoder,” DCRat is a full-featured backdoor whose functionalities can be further augmented by third-party plugins developed by affiliates using a dedicated integrated development environment (IDE) called DCRat Studio.
It was first released in 2018, with version 3.0 shipping on May 30, 2020, and version 4.0 launching nearly a year later on March 18, 2021.
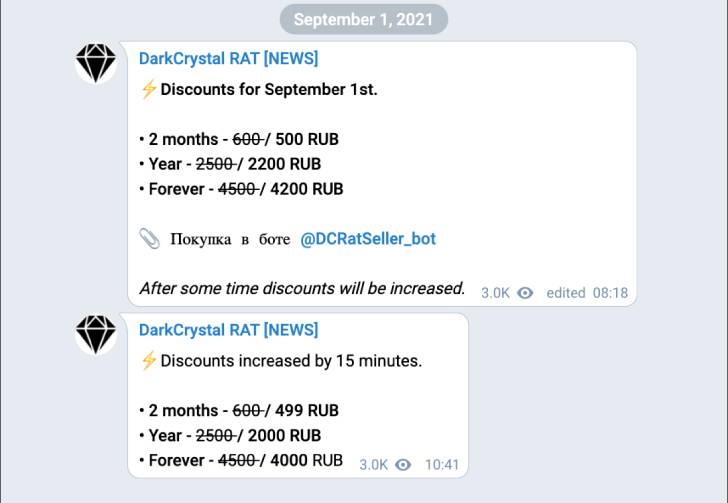
Prices for the trojan start at 500 RUB ($5) for a two-month license, 2,200 RUB ($21) for a year, and 4,200 RUB ($40) for a lifetime subscription, figures which are further reduced during special promotions.
While a previous analysis by Mandiant in May 2020 traced the RAT’s infrastructure to files.dcrat[.]ru, the malware bundle is currently hosted on a different domain named crystalfiles[.]ru, indicating a shift in response to public disclosure.
“All DCRat marketing and sales operations are done through the popular Russian hacking forum lolz[.]guru, which also handles some of the DCRat pre-sales queries,” the researchers said.
Also actively used for communications and sharing information about software and plugin updates is a Telegram channel which has about 2,847 subscribers as of writing.
Messages posted on the channel in recent weeks cover updates to CryptoStealer, TelegramNotifier, and WindowsDefenderExcluder plugins, as well as “cosmetic changes/fixes” to the panel.
“Some Fun features have been moved to the standard plugin,” a translated message shared on April 16 reads. “The weight of the build has slightly decreased. There should be no detects that go specifically to these functions.”
Besides its modular architecture and bespoke plugin framework, DCRat also encompasses an administrator component that’s engineered to stealthily trigger a kill switch, which allows the threat actor to remotely render the tool unusable.
The admin utility, for its part, enables subscribers to sign in to an active command-and-control server, issue commands to infected endpoints, and submit bug reports, among others.
Distribution vectors employed to infect hosts with DCRat include Cobalt Strike Beacons and a traffic direction system (TDS) called Prometheus, a subscription-based crimeware-as-a-service (CaaS) solution used to deliver a variety of payloads.
The implant, in addition to gathering system metadata, supports surveillance, reconnaissance, information theft, and DDoS attack capabilities. It can also capture screenshots, record keystrokes, and steal content from clipboard, Telegram, and web browsers.
“New plugins and minor updates are announced almost every day,” the researchers said. “If the threat is being developed and sustained by just one person, it appears that it’s a project they are working on full-time.”