A proof-of-concept (PoC) code demonstrating a newly disclosed digital signature bypass vulnerability in Java has been shared online.
The high-severity flaw in question, CVE-2022-21449 (CVSS score: 7.5), impacts the following version of Java SE and Oracle GraalVM Enterprise Edition –
- Oracle Java SE: 7u331, 8u321, 11.0.14, 17.0.2, 18
- Oracle GraalVM Enterprise Edition: 20.3.5, 21.3.1, 22.0.0.2
The issue resides in Java’s implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA), a cryptographic mechanism to digitally sign messages and data for verifying the authenticity and the integrity of the contents.
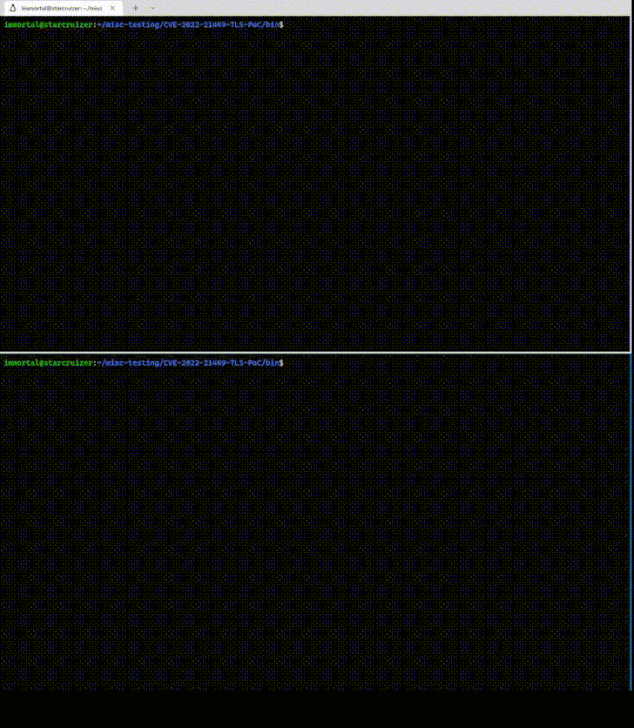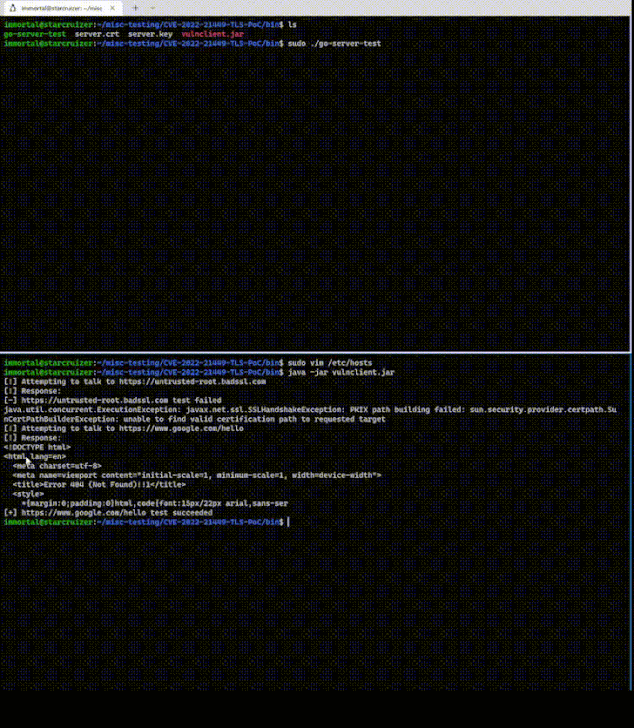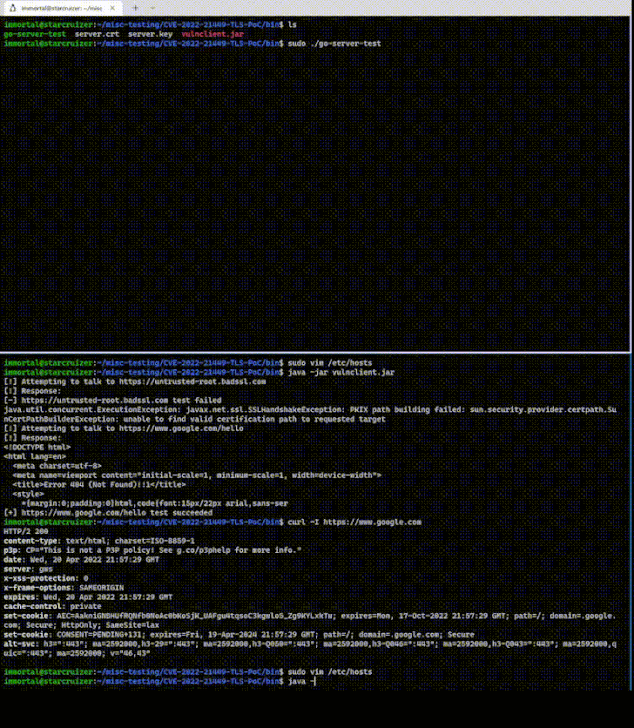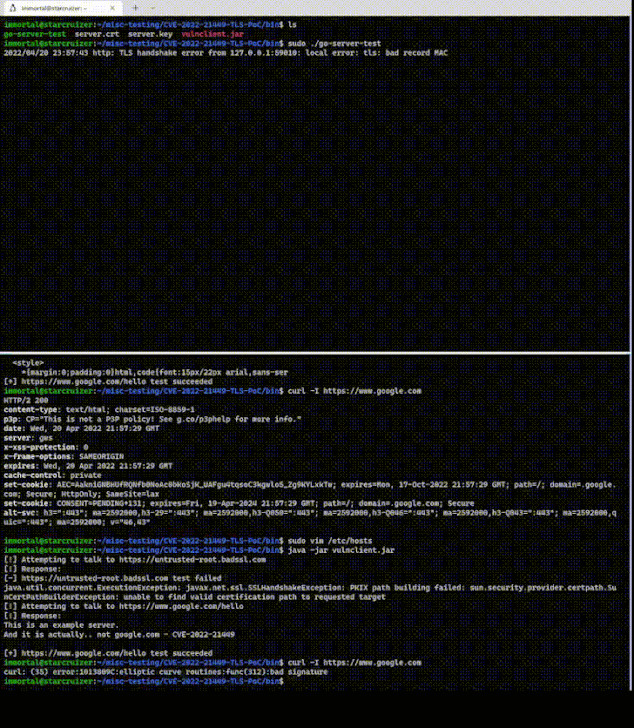
In a nutshell, the cryptographic blunder — dubbed Psychic Signatures in Java — makes it possible to present a totally blank signature, which would still be perceived as valid by the vulnerable implementation.
Successful exploitation of the flaw could permit an attacker to forge signatures and bypass authentication measures put in place.
The PoC, published by security researcher, Khaled Nassar involves a vulnerable client and a malicious TLS server, the former of which accepts an invalid signature from the server, effectively allowing the TLS handshake to continue unimpeded.
“It’s hard to overstate the severity of this bug,” ForgeRock researcher Neil Madden, who discovered and reported the flaw on November 11, 2021, said.
“If you are using ECDSA signatures for any of these security mechanisms, then an attacker can trivially and completely bypass them if your server is running any Java 15, 16, 17, or 18 version.”
The issue has since been addressed by Oracle as part of its quarterly April 2022 Critical Patch Update (CPU) released on April 19, 2022.
In light of the release of the PoC, organizations that use Java 15, Java 16, Java 17, or Java 18 in their environments are recommended to prioritize the patches to mitigate active exploitation.