LinkedIn has become by far the most impersonated brand for phishing attacks, according to new research by Check Point Research (CPR).
The cybersecurity vendor’s 2022 Q1 Brand Phishing Report revealed that phishing attacks impersonating the professional social networking site made up over half (52%) of all attempts globally in the first quarter of 2022. This represents a 44% increase compared to the previous quarter, Q4 2021, when LinkedIn was the fifth most impersonated brand.
CPR said the findings reflected an emerging trend of social engineering scams shifting away from shipping companies and tech giants toward social media networks. In Q1 2022, social networks were the most targeted category, followed by shipping.
Following LinkedIn, the most frequently impersonated brands in phishing attacks were DHL (14%), Google (7%), Microsoft (6%), FedEx (6%), WhatsApp (4%), Amazon (2%), Maersk (1%), AliExpress (0.8%) and Apple (0.8%).
Omer Dembinsky, data research group manager at Check Point Software, commented: “These phishing attempts are attacks of opportunity, plain and simple. Criminal groups orchestrate these phishing attempts on a grand scale, with a view to getting as many people to part with their personal data as possible. Some attacks will attempt to gain leverage over individuals or steal their information, such as those we’re seeing with LinkedIn. Others will be attempts to deploy malware on company networks, such as the fake emails containing spoof carrier documents that we’re seeing with the likes of Maersk.
“If there was ever any doubt that social media would become one of the most heavily targeted sectors by criminal groups, Q1 has laid those doubts to rest. While Facebook has dropped out of the top 10 rankings, LinkedIn has soared to number one and has accounted for more than half of all phishing attempts so far this year. The best defense against phishing threats, as ever, is knowledge. Employees, in particular, should be trained to spot suspicious anomalies such as misspelled domains, typos, incorrect dates and other details that can expose a malicious email or text message. LinkedIn users, in particular, should be extra vigilant over the course of the next few months.”
CPR also provided examples of phishing attacks it observed during Q1. In one of these, a malicious email was designed to steal the victim’s LinkedIn credentials by enticing them to click on a malicious link that redirects the user to a fraudulent LinkedIn login page.
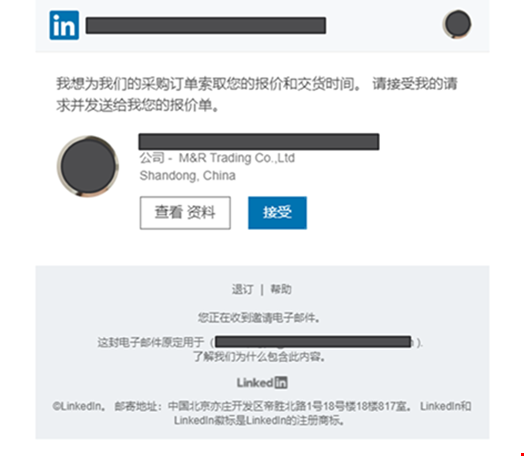
The new findings tie in with research conducted by Egress earlier this year, which found that email phishing attacks impersonating LinkedIn surged by 232% amid the ‘Great Resignation.’ In response, a LinkedIn spokesperson highlighted measures the firm has put in place to protect its members from such impersonation attacks: “Our internal teams work to take action against those who attempt to harm LinkedIn members through phishing. We encourage members to report suspicious messages and help them learn more about what they can do to protect themselves, including turning on two-step verification. To learn more about how members can identify phishing messages, see our Help Center here.”
