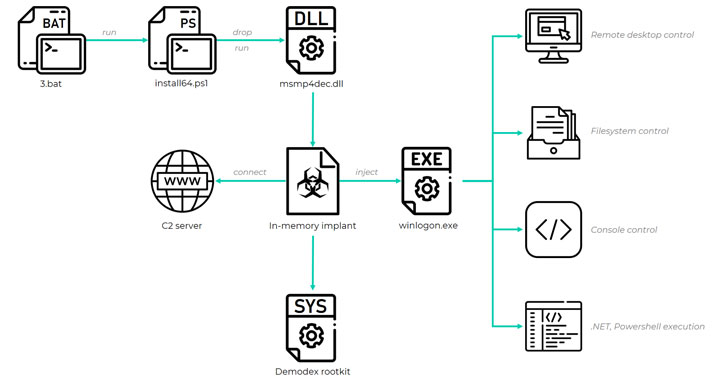
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems.
Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a “sophisticated multi-stage malware framework” that allows for providing persistence and remote control over the targeted hosts.
The Russian cybersecurity firm called the rootkit Demodex, with infections reported across several high-profile entities in Malaysia, Thailand, Vietnam, and Indonesia, in addition to outliers located in Egypt, Ethiopia, and Afghanistan.
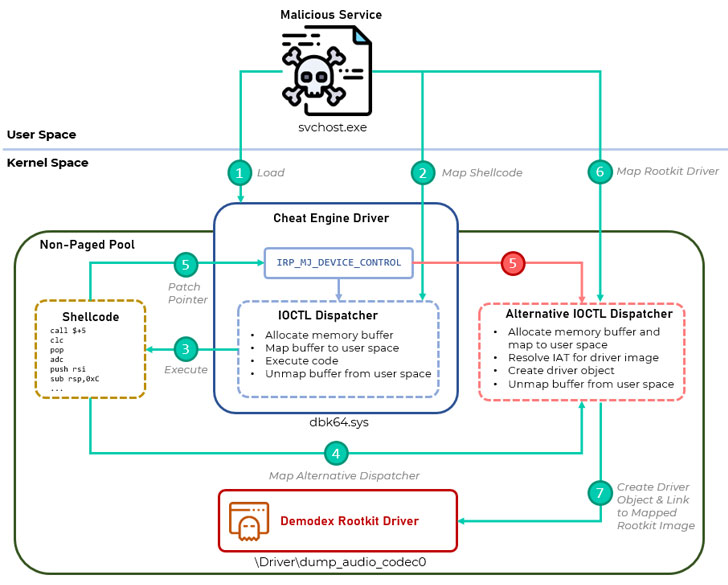
“[Demodex] is used to hide the user mode malware’s artefacts from investigators and security solutions, while demonstrating an interesting undocumented loading scheme involving the kernel mode component of an open-source project named Cheat Engine to bypass the Windows Driver Signature Enforcement mechanism,” Kaspersky researchers said.
GhostEmperor infections have been found to leverage multiple intrusion routes that culminate in the execution of malware in memory, chief among them being exploiting known vulnerabilities in public-facing servers such as Apache, Window IIS, Oracle, and Microsoft Exchange — including the ProxyLogon exploits that came to light in March 2021 — to gain an initial foothold and laterally pivot to other parts of the victim’s network, even on machines running recent versions of the Windows 10 operating system.
Following a successful breach, select infection chains that resulted in the deployment of the rootkit were carried out remotely via another system in the same network using legitimate software such as WMI or PsExec, leading to the execution of an in-memory implant capable of installing additional payloads during run time.
Notwithstanding its reliance on obfuscation and other detection-evasion methods to elude discovery and analysis, Demodex gets around Microsoft’s Driver Signature Enforcement mechanism to permit the execution of unsigned, arbitrary code in kernel space by leveraging a legitimate and open-source signed driver named (“dbk64.sys”) that’s shipped alongside Cheat Engine, an application used to introduce cheats into video games.
“With a long-standing operation, high profile victims, [and] advanced toolset […] the underlying actor is highly skilled and accomplished in their craft, both of which are evident through the use of a broad set of unusual and sophisticated anti-forensic and anti-analysis techniques,” the researchers said.
The disclosure comes as a China-linked threat actor codenamed TAG-28 has been discovered as being behind intrusions against Indian media and government agencies such as The Times Group, the Unique Identification Authority of India (UIDAI), and the police department of the state of Madhya Pradesh.
Recorded Future, earlier this week, also unearthed malicious activity targeting a mail server of Roshan, one of Afghanistan’s largest telecommunications providers, that it attributed to four distinct Chinese state-sponsored actors — RedFoxtrot, Calypso APT, as well as two separate clusters using backdoors associated with the Winnti and PlugX groups.