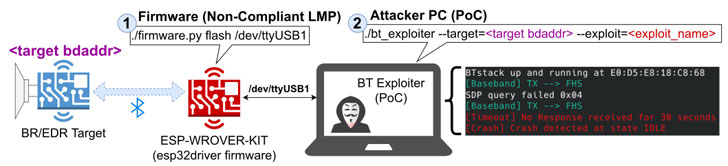
A set of new security vulnerabilities has been disclosed in commercial Bluetooth stacks that could enable an adversary to execute arbitrary code and, worse, crash the devices via denial-of-service (DoS) attacks.
Collectively dubbed “BrakTooth” (referring to the Norwegian word “Brak” which translates to “crash”), the 16 security weaknesses span across 13 Bluetooth chipsets from 11 vendors such as Intel, Qualcomm, Zhuhai Jieli Technology, and Texas Instruments, covering an estimated 1,400 or more commercial products, including laptops, smartphones, programmable logic controllers, and IoT devices.
The flaws were disclosed by researchers from the ASSET (Automated Systems SEcuriTy) Research Group at the Singapore University of Technology and Design (SUTD).
“All the vulnerabilities […] can be triggered without any previous pairing or authentication,” the researchers noted. “The impact of our discovered vulnerabilities is categorized into (I) crashes and (II) deadlocks. Crashes generally trigger a fatal assertion, segmentation faults due to a buffer or heap overflow within the SoC firmware. Deadlocks, in contrast, lead the target device to a condition in which no further BT communication is possible.”
The most severe of the 16 bugs is CVE-2021-28139, which affects the ESP32 SoC used in many Bluetooth-based appliances ranging from consumer electronics to industrial equipment. Arising due to a lack of an out-of-bounds check in the library, the flaw enables an attacker to inject arbitrary code on vulnerable devices, including erasing its NVRAM data.
Other vulnerabilities could result in the Bluetooth functionality getting entirely disabled via arbitrary code execution, or cause a denial-of-service condition in laptops and smartphones employing Intel AX200 SoCs. “This vulnerability allows an attacker to forcibly disconnect slave BT devices currently connected to AX200 under Windows or Linux Laptops,” the researchers said. “Similarly, Android phones such as Pocophone F1 and Oppo Reno 5G experience BT disruptions.”
A last collection of flaws discovered in Bluetooth speakers, headphones, and audio modules could be abused to freeze and even completely shut down the devices, requiring the users to manually turn them back on. Troublingly, all the aforementioned BrakTooth attacks could be carried out with a readily available Bluetooth packet sniffer that costs less than $15.
While Espressif, Infineon (Cypress), and Bluetrum Technology have released firmware patches to rectify the identified vulnerabilities, Intel, Qualcomm, and Zhuhai Jieli Technology are said to be investigating the flaws or in the process of readying security updates. Texas Instruments, however, doesn’t intend to release a fix unless “demanded by customers.”
The ASSET group has also made available a proof-of-concept (PoC) tool that can be used by vendors producing Bluetooth SoCs, modules, and products to replicate the vulnerabilities and validate against BrakTooth attacks.