A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple’s on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection.
“AdLoad,” as the malware is known, is one of several widespread adware and bundleware loaders targeting macOS since at least 2017 that’s capable of backdooring an affected system to download and install adware or potentially unwanted programs (PUPs), as well as amass and transmit information about victim machines.
The new iteration “continues to impact Mac users who rely solely on Apple’s built-in security control XProtect for malware detection,” SentinelOne threat researcher Phil Stokes said in an analysis published last week. “As of today, however, XProtect arguably has around 11 different signatures for AdLoad [but] the variant used in this new campaign is undetected by any of those rules.”
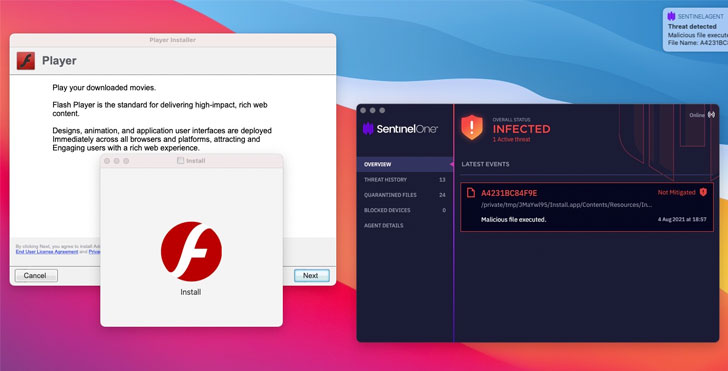
The 2021 version of AdLoad latches on to persistence and executable names that use a different file extension pattern (.system or .service), enabling the malware to get around additional security protections incorporated by Apple, ultimately resulting in the installation of a persistence agent, which, in turn, triggers an attack chain to deploy malicious droppers that masquerade as a fake Player.app to install malware.
What’s more, the droppers are signed with a valid signature using developer certificates, prompting Apple to revoke the certificates “within a matter of days (sometimes hours) of samples being observed on VirusTotal, offering some belated and temporary protection against further infections by those particular signed samples by means of Gatekeeper and OCSP signature checks,” Stokes noted.
SentinelOne said it detected new samples signed with fresh certificates in a couple of hours and days, calling it a “game of whack-a-mole.” First samples of AdLoad are said to have appeared as early as November 2020, with regular further occurrences across the first half of 2021, followed by a sharp uptick throughout July and, in particular, the early weeks of August 2021.
AdLoad is among the malware families, alongside Shlayer, that’s been known to bypass XProtect and infect Macs with other malicious payloads. In April 2021, Apple addressed an actively exploited zero-day flaw in its Gatekeeper service (CVE-2021-30657) that was abused by the Shlayer operators to deploy unapproved software on Macs.
“Malware on macOS is a problem that the device manufacturer is struggling to cope with,” Stokes said. “The fact that hundreds of unique samples of a well-known adware variant have been circulating for at least 10 months and yet still remain undetected by Apple’s built-in malware scanner demonstrates the necessity of adding further endpoint security controls to Mac devices.”