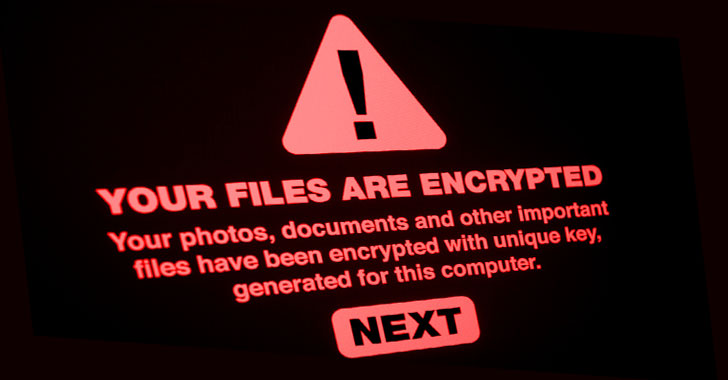
Ransomware operators such as Magniber and Vice Society are actively exploiting vulnerabilities in Windows Print Spooler to compromise victims and spread laterally across a victim’s network to deploy file-encrypting payloads on targeted systems.
“Multiple, distinct threat actors view this vulnerability as attractive to use during their attacks and may indicate that this vulnerability will continue to see more widespread adoption and incorporation by various adversaries moving forward,” Cisco Talos said in a report published Thursday, corroborating an independent analysis from CrowdStrike, which observed instances of Magniber ransomware infections targeting entities in South Korea.
While Magniber ransomware was first spotted in late 2017 singling out victims in South Korea through malvertising campaigns, Vice Society is a new entrant that emerged on the ransomware landscape in mid-2021, primarily targeting public school districts and other educational institutions. The attacks are said to have taken place since at least July 13.
Since June, a series of “PrintNightmare” issues affecting the Windows print spooler service has come to light that could enable remote code execution when the component performs privileged file operations –
- CVE-2021-1675 – Windows Print Spooler Remote Code Execution Vulnerability (Patched on June 8)
- CVE-2021-34527 – Windows Print Spooler Remote Code Execution Vulnerability (Patched on July 6-7)
- CVE-2021-34481 – Windows Print Spooler Remote Code Execution Vulnerability (Patched on August 10)
- CVE-2021-36936 – Windows Print Spooler Remote Code Execution Vulnerability (Patched on August 10)
- CVE-2021-36947 – Windows Print Spooler Remote Code Execution Vulnerability (Patched on August 10)
- CVE-2021-34483 – Windows Print Spooler Elevation of Privilege Vulnerability (Patched on August 10)
- CVE-2021-36958 – Windows Print Spooler Remote Code Execution Vulnerability (Unpatched)
CrowdStrike noted it was able to successfully prevent attempts made by the Magniber ransomware gang at exploiting the PrintNightmare vulnerability.
Vice Society, on the other hand, leveraged a variety of techniques to conduct post-compromise discovery and reconnaissance prior to bypassing native Windows protections for credential theft and privilege escalation.
Specifically, the attacker is believed to have used a malicious library associated with the PrintNightmare flaw (CVE-2021-34527) to pivot to multiple systems across the environment and extract credentials from the victim.
“Adversaries are constantly refining their approach to the ransomware attack lifecycle as they strive to operate more effectively, efficiently, and evasively,” the researchers said. “The use of the vulnerability known as PrintNightmare shows that adversaries are paying close attention and will quickly incorporate new tools that they find useful for various purposes during their attacks.”