The ESXiArgs ransomware attack that started infecting servers of VMware ESXi hypervisors from February 2, 2023, is the latest of a long list of malicious campaigns exploiting ESXi vulnerabilities.
Threat intelligence firm Recorded Future has tracked ESXi-focused ransomware since 2020. In a threat analysis report published on February 13, 2023, the company said it believes virtual machines (VM) orchestration tools such as ESXi will increasingly be used by malicious actors in the future “as organizations continue virtualizing their critical infrastructure and business systems.”
VMware’s hypervisors, however, are increasingly appealing to threat actors, with the report noting “an approximately three-fold increase in ransomware targeting ESXi between 2021 and 2022, with offerings available from many groups including ALPHV, LockBit, and BlackBasta.”
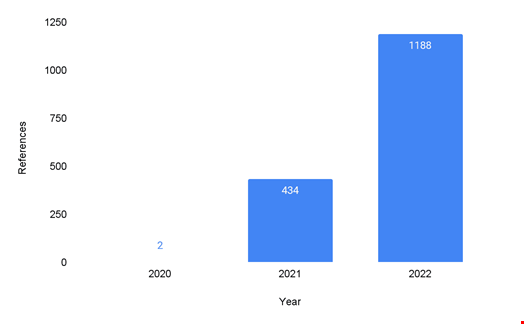
ESXi exploits were almost non-existent in 2020, notes the report, explaining that during this time “threat actors primarily targeted Windows-based networks due to the availability of initial access presented by the pandemic and multiple critical vulnerabilities.”
Cyber-attacks exploiting ESXi jumped to 434 in 2021 and Recorded Future found that an even more significant surge occurred in 2022, with ESXi-focused cyber-attacks reaching at least 1188.
Gaining Initial Access
In most cases, threat actors utilize ESXi vulnerabilities to gain initial access, “specifically via remote code execution (RCE) or authentication bypass,” researchers noted.
Several organizations, like US Cybersecurity and Infrastructure Security Agency (CISA) and France’s CERT-FR, believe that the ESXiArgs ransomware campaign exploited a 2021 vulnerability (CVE-2021-21974).
Recorded Future also found that threat actors attacking ESXi typically try to get administrator credentials, enable SSH on the ESXi servers, and then escalate to root privileges for unrestricted access.
“This type of access using legitimate credentials is difficult to detect due to its ability to blend into normal system administrator activities [by] abusing native commands to perform their actions,” the report reads.
The immaturity of antivirus and EDR solutions that cover ESXi also lowers the technical barrier for threat actors deploying malware on ESXi compared with those targeting Windows.
Backdoors, Ransomware and SharpSphere
Once they have gained privileged access to the ESXi servers, attackers usually use it for three purposes:
- Installing backdoors;
- Deploying ransomware;
- Using a post-exploitation toolkit such as SharpSphere, a C# implementation of vSphere’s Web Services API, to deploy credential dumping attacks, for instance.
A Multi-Faceted Mitigation Approach Needed
The report notes that mitigating those attacks is no easy task “due to the complex nature of hypervisors.” It requires a multi-faceted, multi-layered approach.
First, “traditional defenses, strong password policies, and minimizing the attack surface can provide a great deal of deterrence to threat actors,” reads the report. But it will not prevent more sophisticated attacks.
For better protection, Recorded Future recommends implementing the following:
- Enable multi-factor authentication (MFA) and enforce it on high-privileged accounts;
- Create alerts on account modifications, enabling of services, and authentication patterns;
- Refrain from implementing Active Directory authentication for administrators;
- Disable SSH and Shell access to ESXi. However, if they must be enabled, consider setting timeouts and enabling key-only authentication;
- Implement network segmentation for the ESXi management network;
- Minimize the number of open ESXi firewall ports, and use vSphere Client, ESXCLI, or PowerCLI commands to check and manage the status of ports;
- Ensure that software, drivers, and other components of ESXi are legitimate and enable Secure Boot on ESXi to perform validation of the components at boot time;
- Install and configure Trusted Platform Module 2.0 chips, as this offers the most effective VMware-supported method of ensuring the integrity of software components on the system;
- Prohibit code execution inside ESXi with VMkernel.Boot.execInstalledOnly.
While “ransomware targeting ESXi will continue to be a threat to organizations, putting them at risk of operational downtime, competitive disadvantage, and damage to their brand, […] organizations should continue to deploy virtualized infrastructure, but it is critical to implement security best practices and similar precautions as used in existing infrastructure,” the report concludes.