A new piece of research from academics at ETH Zurich has identified a number of critical security issues in the MEGA cloud storage service that could be leveraged to break the confidentiality and integrity of user data.
In a paper titled “MEGA: Malleable Encryption Goes Awry,” the researchers point out how MEGA’s system does not protect its users against a malicious server, thereby enabling a rogue actor to fully compromise the privacy of the uploaded files.
“Additionally, the integrity of user data is damaged to the extent that an attacker can insert malicious files of their choice which pass all authenticity checks of the client,” ETH Zurich’s Matilda Backendal, Miro Haller, and Kenneth G. Paterson said in an analysis of the service’s cryptographic architecture.
MEGA, which advertises itself as the “privacy company” and claims to provide user-controlled end-to-end encrypted cloud storage, has more than 10 million daily active users, with over 122 billion files uploaded to the platform to date.
Chief among the weaknesses is an RSA Key Recovery Attack that makes it possible for MEGA (itself acting maliciously) or a resourceful nation-state adversary in control of its API infrastructure to recover a user’s RSA private key by tampering with 512 login attempts and decrypt the stored content.
“Once a targeted account had made enough successful logins, incoming shared folders, MEGAdrop files and chats could have been decryptable,” Mathias Ortmann, MEGA’s chief architect, said in response to the findings. “Files in the cloud drive could have been successively decrypted during subsequent logins.”
The recovered RSA key can then be extended to make way for four other attacks –
- Plaintext Recovery Attack, which allows MEGA to decrypt node keys — an encryption key associated with every uploaded file and are encrypted with a user’s master key — and use them to decrypt all user communication and files.
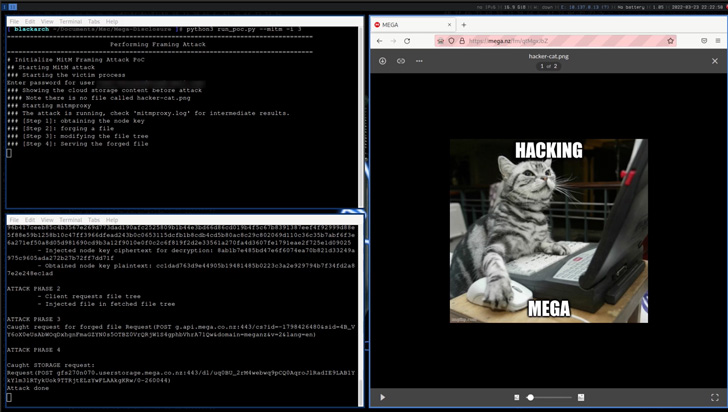
- Framing Attack, wherein MEGA can insert arbitrary files into the user’s file storage that are indistinguishable from genuinely uploaded ones.
- Integrity Attack, a less stealthy variant of the Framing Attack that can be exploited to forge a file in the name of the victim and place it in the target’s cloud storage, and
“Each user has a public RSA key used by other users or MEGA to encrypt data for the owner, and a private key used by the user themselves to decrypt data shared with them,” the researchers explained. “With this [GaP Bleichenbacher attack], MEGA can decrypt these RSA ciphertexts, albeit requiring an impractical number of login attempts.”
In a nutshell, the attacks could be weaponized by MEGA or any entity controlling its core infrastructure to upload lookalike files and decrypt all files and folders owned by or shared with the victim as well as the chat messages exchanged.
The shortcomings are severe as they undermine MEGA’s supposed security guarantees, prompting the company to issue updates to address the first three of the five issues. The fourth vulnerability related to the breach of integrity is expected to be addressed in an upcoming release.
As for the Bleichenbacher-style attack against MEGA’s RSA encryption mechanism, the company noted the attack is “challenging to perform in practice as it would require approximately 122,000 client interactions on average” and that it would remove the legacy code from all of its clients.
MEGA further emphasized that it’s not aware of any user accounts that may have been compromised by the aforementioned attack methods.
“The reported vulnerabilities would have required MEGA to become a bad actor against certain of its users, or otherwise could only be exploited if another party compromised MEGA’s API servers or TLS connections without being noticed,” Ortmann pointed out.
“The attacks […] arise from unexpected interactions between seemingly independent components of MEGA’s cryptographic architecture,” the researchers elaborated. “They hint at the difficulty of maintaining large-scale systems employing cryptography, especially when the system has an evolving set of features and is deployed across multiple platforms.”
“The attacks presented here show that it is possible for a motivated party to find and exploit vulnerabilities in real world cryptographic architectures, with devastating results for security. It is conceivable that systems in this category attract adversaries who are willing to invest significant resources to compromise the service itself, increasing the plausibility of high-complexity attacks.”