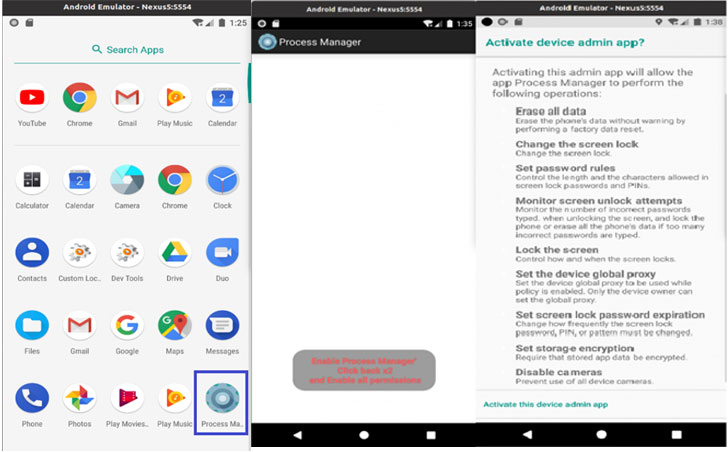
An Android spyware application has been spotted masquerading as a “Process Manager” service to stealthily siphon sensitive information stored in the infected devices.
Interestingly, the app — that has the package name “com.remote.app” — establishes contact with a remote command-and-control server, 82.146.35[.]240, which has been previously identified as infrastructure belonging to the Russia-based hacking group known as Turla.
“When the application is run, a warning appears about the permissions granted to the application,” Lab52 researchers said. “These include screen unlock attempts, lock the screen, set the device global proxy, set screen lock password expiration, set storage encryption and disable cameras.”
Once the app is “activated,” the malware removes its gear-shaped icon from the home screen and runs in the background, abusing its wide permissions to access the device’s contacts and call logs, track its location, send and read messages, access external storage, snap pictures, and record audio.
The gathered information is captured in a JSON format and subsequently transmitted to the aforementioned remote server. Despite the overlap in the C2 server used, Lab52 said it doesn’t have enough evidence to attribute the malware to the Turla group.
Also unknown at this stage is the exact initial access vector employed for distributing the spyware and intended targets of the campaign.
That said, the rogue Android app also attempts to download a legitimate application called Roz Dhan (meaning “Daily Wealth” in Hindi) that has over 10 million installations and allows users to earn cash rewards for completing surveys and questionnaires.
“The application, [which] is on Google Play and is used to earn money, has a referral system that is abused by the malware,” the researchers said. “The attacker installs it on the device and makes a profit.”