Cybersecurity researchers on Tuesday disclosed 16 new high-severity vulnerabilities in various implementations of Unified Extensible Firmware Interface (UEFI) firmware impacting multiple HP enterprise devices.
The shortcomings, which have CVSS scores ranging from 7.5 to 8.8, have been uncovered in HP’s UEFI firmware. The variety of devices affected includes HP’s laptops, desktops, point-of-sale (PoS) systems, and edge computing nodes.
“By exploiting the vulnerabilities disclosed, attackers can leverage them to perform privileged code execution in firmware, below the operating system, and potentially deliver persistent malicious code that survives operating system re-installations and allows the bypass of endpoint security solutions (EDR/AV), Secure Boot and Virtualization-Based Security isolation,” American firmware security company Binarly said in a report shared with The Hacker News.
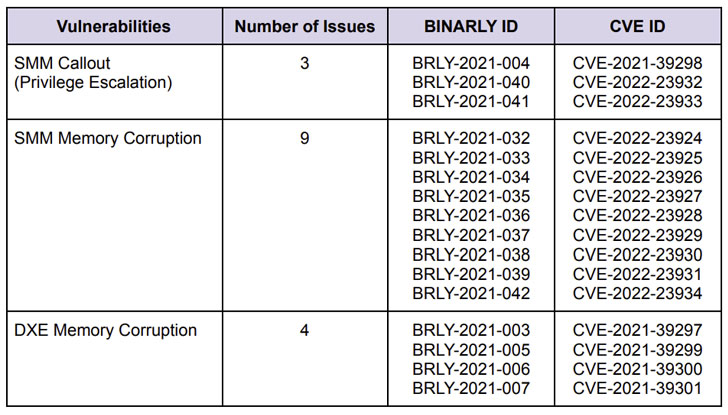
The most severe of the flaws concern a number of memory corruption vulnerabilities in the System Management Mode (SMM) of the firmware, thereby enabling the execution of arbitrary code with the highest privileges.
Following a coordinated disclosure process with HP and CERT Coordination Center (CERT/CC), the issues were addressed as part of a series of security updates shipped on February 2 and March 8, 2022.
“Unfortunately, most of the issues […] are repeatable failures, some of which are due to the complexity of the codebase or legacy components that get less security attention, but are still widely used in the field,” the researchers pointed out.
The disclosure arrives a little over a month after Binarly publicized the discovery of 23 high-impact vulnerabilities in Insyde Software’s InsydeH2O UEFI firmware that could be weaponized to deploy persistent malware that’s capable of evading security systems.
The latest findings are also significant in light of the fact that firmware has emerged as an ever-expanding attack surface for threat actors to launch highly-targeted devastating attacks. At least five different firmware malware strains have been detected in the wild to date since 2018.
“Securing the firmware layer is often overlooked, but it is a single point of failure in devices and is one of the stealthiest methods in which an attacker can compromise devices at scale,” the U.S. Commerce and Homeland Security departments highlighted in a report published last month.