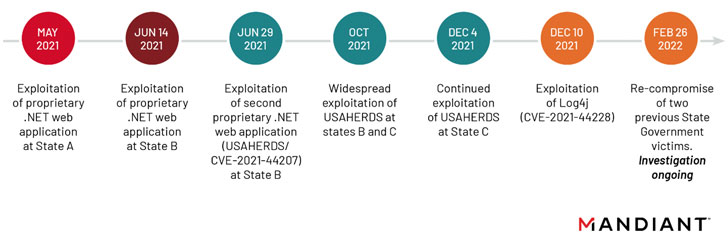
APT41, the state-sponsored threat actor affiliated with China, breached at least six U.S. state government networks between May 2021 and February 2022 by retooling its attack vectors to take advantage of vulnerable internet-facing web applications.
The exploited vulnerabilities included “a zero-day vulnerability in the USAHERDS application (CVE-2021-44207) as well as the now infamous zero-day in Log4j (CVE-2021-44228),” researchers from Mandiant said in a report published Tuesday, calling it a “deliberate campaign.”
Besides web compromises, the persistent attacks also involved the weaponization of exploiting deserialization, SQL injection, and directory traversal vulnerabilities, the cybersecurity and incident response firm noted.
The prolific advanced persistent threat, also known by the monikers Barium and Winnti, has a track record of targeting organizations in both the public and private sectors to orchestrate espionage activity in parallel with financially motivated operations.
In early 2020, the group was linked to a global intrusion campaign that leveraged a variety of exploits involving Citrix NetScaler/ADC, Cisco routers, and Zoho ManageEngine Desktop Central to strike dozens of entities in 20 countries with malicious payloads.
The latest disclosure continues the trend of APT41 quickly co-opting newly disclosed vulnerabilities such as Log4Shell to gain initial access into target networks of two U.S. state governments alongside insurance and telecom firms within hours of it becoming public knowledge.
The intrusions continued well into February 2022 when the hacking crew re-compromised two U.S. state government victims that were infiltrated for the first time in May and June 2021, “demonstrating their unceasing desire to access state government networks,” the researchers said.
What’s more, the foothold established after the exploitation of Log4Shell resulted in the deployment of a new variant of a modular C++ backdoor called KEYPLUG on Linux systems, but not before performing extensive reconnaissance and credential harvesting of the target environments.
Also observed during the attacks were an in-memory dropper called DUSTPAN (aka StealthVector) that’s orchestrated to execute the next-stage payload, alongside advanced post-compromise tools like DEADEYE, a malware loader that’s responsible for launching the LOWKEY implant.
Chief among the variety of techniques, evasion methods, and capabilities used by APT41 involved the “substantially increased” usage of Cloudflare services for command-and-control (C2) communications and data exfiltration, the researchers said.
Though Mandiant noted it found evidence of the adversaries exfiltrating personally identifiable information that’s typically in line with an espionage operation, the ultimate goal of the campaign is currently unclear.
The findings also mark the second time a Chinese nation-state group has abused security flaws in the ubiquitous Apache Log4j library to penetrate targets.
In January 2022, Microsoft detailed an attack campaign mounted by Hafnium – the threat actor behind the widespread exploitation of Exchange Server flaws a year ago – that utilized the vulnerability to “attack virtualization infrastructure to extend their typical targeting.”
If anything, the latest activities are yet another sign of a constantly adapting adversary that’s capable of shifting its goalposts as well as refine its malware arsenal to strike entities around the world that are of strategic interest.
APT41’s cyber operations against healthcare, high-tech, and telecommunications sectors over the years have since caught the attention of the U.S. Justice Department, which issued charges against five members of the group in 2020, landing the hackers a place on the FBI’s cyber most wanted list.
“APT41 can quickly adapt their initial access techniques by re-compromising an environment through a different vector, or by rapidly operationalizing a fresh vulnerability,” the researchers said. “The group also demonstrates a willingness to retool and deploy capabilities through new attack vectors as opposed to holding onto them for future use.”
In a related development, Google’s Threat Analysis Group said it took steps to block a phishing campaign staged by another Chinese state-backed group tracked as APT31 (aka Zirconium) last month that was aimed at “high profile Gmail users affiliated with the U.S. government.”