Cybersecurity researchers have disclosed an unpatched security vulnerability in the protocol used by Microsoft Azure Active Directory that potential adversaries could abuse to stage undetected brute-force attacks.
“This flaw allows threat actors to perform single-factor brute-force attacks against Azure Active Directory (Azure AD) without generating sign-in events in the targeted organization’s tenant,” researchers from Secureworks Counter Threat Unit (CTU) said in a report published on Wednesday.
Azure Active Directory is Microsoft’s enterprise cloud-based identity and access management (IAM) solution designed for single sign-on (SSO) and multi-factor authentication. It’s also a core component of Microsoft 365 (formerly Office 365), with capabilities to provide authentication to other applications via OAuth.
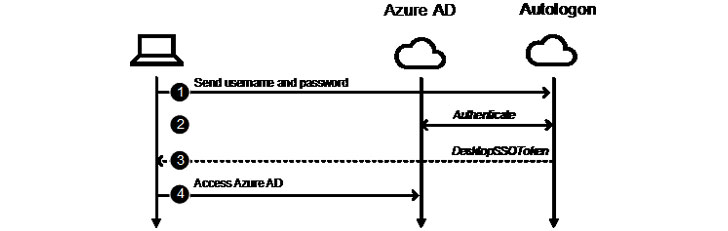
The weakness resides in the Seamless Single Sign-On feature that allows employees to automatically sign when using their corporate devices that are connected to enterprise networks without having to enter any passwords. Seamless SSO is also an “opportunistic feature” in that if the process fails, the login falls back to the default behavior, wherein the user needs to enter their password on the sign-in page.
To achieve this, the mechanism relies on the Kerberos protocol to look up the corresponding user object in Azure AD and issue a ticket-granting ticket (TGT), permitting the user to access the resource in question. But for users of Exchange Online with Office clients older than the Office 2013 May 2015 update, the authentication is carried through a password-based endpoint called “UserNameMixed” that either generates an access token or an error code depending on whether the credentials are valid.
It’s these error codes where the flaw stems from. While successful authentication events create sign-ins logs upon sending the access tokens, “Autologon‘s authentication to Azure AD is not logged,” allowing the omission to be leveraged for undetected brute-force attacks through the UserNameMixed endpoint.
Secureworks said it notified Microsoft of the issue on June 29, only for Microsoft to acknowledge the behavior on July 21 as “by design.” We have reached out to the company for further comment, and we will update the story if we hear back.