Scams
Your phone number is more than just a way to contact you – scammers can use it to target you with malicious messages and even exploit it to gain access to your bank account or steal corporate data
13 Aug 2024
•
,
5 min. read

Last month, we looked at how scammers can gain access to your phone number and how data breaches and phishing campaigns could make obtaining it easy. In this blogpost, we’ll focus more on why phone numbers are valuable targets and discuss the risks associated with their compromise.
The $cam industry
Online scammers continue to rake in staggering profits from a wide variety of fraudulent schemes. In recent years, many such schemes have been orchestrated by criminal syndicates that run scam compounds in Southeast Asia, where trafficked individuals are coerced into executing elaborate ploys, such as pig butchering.
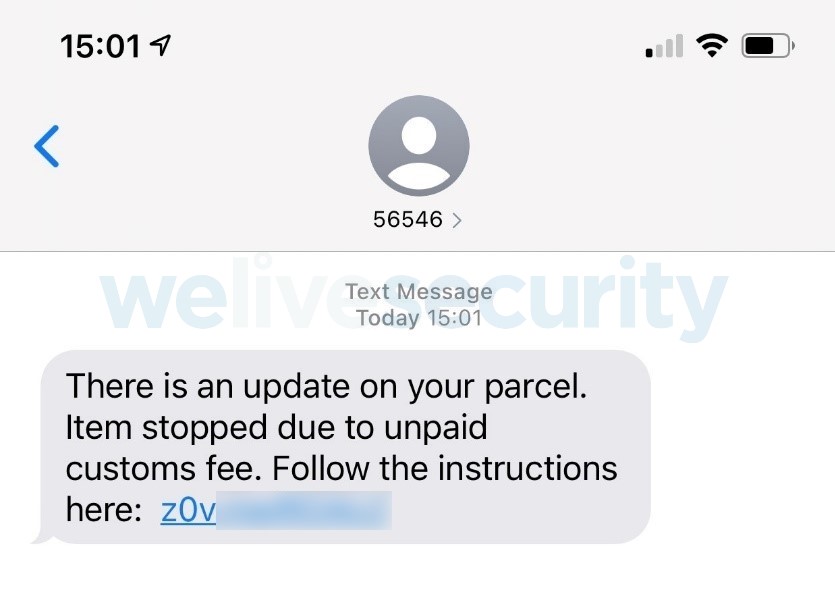
Apart from building fake online relationships, the tactics of many online fraudsters often involve creating scenarios that demand urgent action or rely on other ruses, including purported bank or PayPal account takeovers, devices compromised with malware, failed package deliveries, and even kidnapped relatives and other schemes leveraging artificial intelligence (AI).
At the heart of many online fraud schemes is phishing and other social engineering attacks. Their success lies largely in their low-cost/high-reward nature, scalability, ability to exploit human weaknesses, as well as the challenges of cross-border law enforcement. To top it off, it may take one successful “phish” to pay off the entire operation.
Throw me some numbers
Let’s now look at how phone numbers fit into this, why they are, together with account login credentials, so valuable to scammers, and how they can be leveraged for malicious ends.
Smishing and hacking
For starters, threat actors could target you with malware disguised as benign links or attachments that will, however, install spyware or other malware on your device or exfiltrate your personal data from it. Alternatively, they can send you messages that aim to trick you into surrendering your login credentials or other personal information on phishing websites.
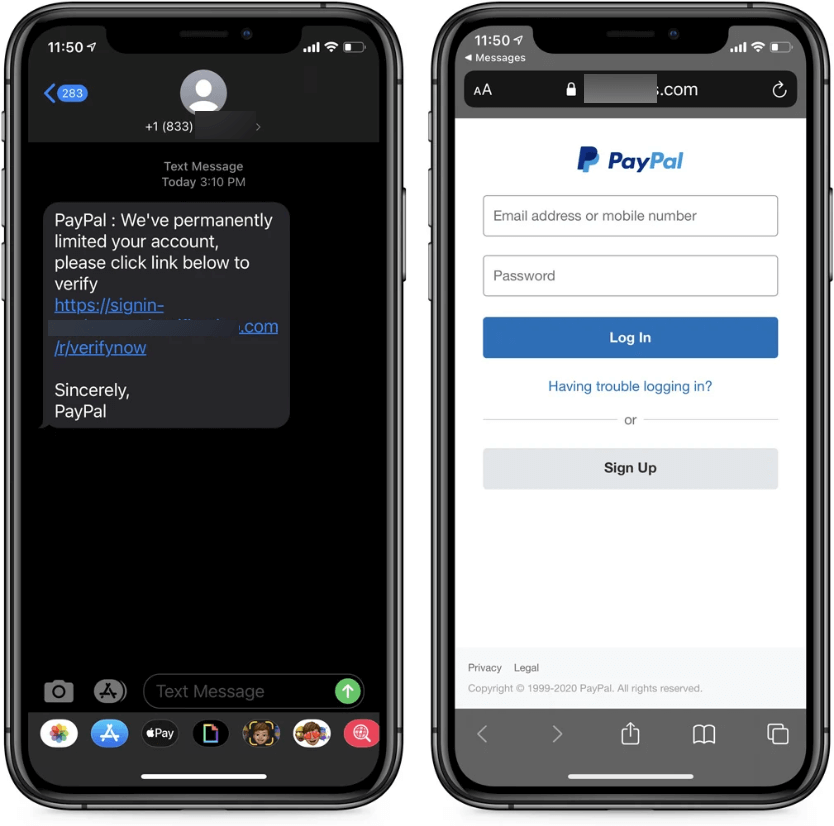
For example, ESET Threat Report H1 2024 highlighted the proliferation of GoldPickaxe malware that in its iOS iteration employs a multistage social engineering scheme that persuades victims to install a Mobile Device Management profile, giving threat actors complete control over the victim’s phone.
Call forwarding, SIM swaps and Caller ID spoofing
Despite the rise of digital communication, phone calls and messages remain a trusted method for exchanging confidential information.
- In call forwarding schemes, scammers contact you or your service provider and ultimately have phone calls forwarded from your phone number to a number under their control. While the provider might ask for verification, the scammer could already have access to more of your personal details (from data leaks or public sources), making this scam easy to perform.
- Similarly, SIM swapping fraudsters can trick your mobile carrier into activating their SIM card under your name/old number, effectively porting your number to their SIM card. This scam is “louder” than call forwarding chiefly because you lose access to your phone network as a result. While also requiring some research into the victim’s life for the verification process, SIM swapping has been a serious threat for years.
- Scammers can spoof their Caller ID by impersonating your number, using Voice over Internet Protocol (VoIP) or spoofing services, and other methods. As a result, attackers could mask their identity while committing financial scams and other crimes and pretending to be you or your trusted contact.
Why are all these scams such a threat? These days, many online services rely on phone numbers for authentication and account recovery. Compromising a phone number can, therefore, be tantamount to bypassing your security safeguards, including two-factor authentication (2FA). Additionally, scammers may impersonate you to defraud your contacts – or your employer.
Phishing for corporate data
These days, many employees use personal or company phones to check their corporate emails or messages. This creates a notable vector for attacks, as computers are no longer the sole access points for attempted compromise. Scammers could impersonate business executives or accounting departments to request money transfers for “business” purposes.
Indeed, the ultimate goal for many scammers is to gain access to corporate systems and funds. The human element plays a crucial role in these schemes, too. We often don’t verify the legitimacy of requests before complying with them, making it easy for phishing attacks to succeed and ultimately resulting in substantial financial damage to businesses.
CEO fraud
For instance, imagine being an accountant at a large financial company. You’re playing around with Excel when you receive a phone call, seemingly from your boss, asking you to wire over money for a business deal whose success hinges on your prompt action. Such scams are quite real. Since the call appears to come from your boss’s number, you may not question its legitimacy – and you wouldn’t be alone.
The news runs red with mentions of this “CEO fraud”, a subset of business email compromise (BEC) fraud. Today, such scams are supercharged by AI, with threat actors using voice cloning to better impersonate someone (in case caller ID spoofing wasn’t enough).
So, what to do in such dangerous times?
Raising the safety net
Thankfully, there are a few ways people and businesses can stay free of phone scams:
- Validate: Never answer or interact with unknown callers/senders, and whenever you receive a request for personal data from a “trusted” entity, call them first and ask whether the request you received was genuine.
- Reach out to your service provider: To prevent forwarding or SIM swaps, ask your service provider to secure your account against unwanted changes with additional security factors like SIM locks to prevent swapping or more comprehensive verification checks.
- Mind what you share: To prevent scams from gathering more data on you, mind what you share about yourself online. Impersonation relies on presenting oneself as someone you know, so try to limit your public exposure.
- Forget SMS: To prevent fraud, protect your accounts with app-based two-factor authentication instead of SMS-based one. The latter can be easily intercepted and let crooks to compromise your accounts with ease.
- Use mobile security: Phishing, either through messages or calls, can be detected by strong mobile security software. For businesses, mobile threat defense and secure authentication can help overcome such threats.
To conclude, since a phone number can be a doorway for threat actors and lead to large-scale business compromise and millions in damage. It should be kept as private as possible – just like any other unique identifier, after all.
As phishing remains a major threat, stay vigilant and remember: validation and authentication are your keys to staying secure!
In the meantime, why not test your phish-spotting prowess in our quick quiz?
