In the past few months, the Telegram clicker game Hamster Kombat has taken the world of cryptocurrency game enthusiasts by storm. Even though the gameplay, which mostly entails repeatedly tapping the screen of one’s mobile device, might be rather simple, players are after something more: the possibility of earning big once Hamster Kombat’s creators unveil the promised new cryptocoin tied to the game.
Due to its success, the game has already attracted countless copycats that replicate its name and icon, and have similar gameplay. Luckily, all the early examples we found were not malicious, but nevertheless aim to make money from in-app advertisements.
Unfortunately, ESET researchers discovered that cybercriminals have also started to capitalize on Hamster Kombat’s popularity. Exposing the risks of trying to obtain games and related software from unofficial sources, we found several threats abusing Hamster Kombat’s fame in such places as remotely controlled Android malware distributed through an unofficial Hamster Kombat Telegram channel, fake app stores that deliver unwanted advertisements, and GitHub repositories distributing Lumma Stealer for Windows devices while claiming to offer automation tools for the game.
Key points of the blogpost:
- Hamster Kombat’s success has attracted malicious actors trying to abuse interest in the game for monetary gain.
- ESET researchers discovered Android spyware named Ratel pretending to be Hamster Kombat, distributed via an unofficial Telegram channel.
- Android users are also targeted by fake app stores claiming to offer the game but delivering unwanted advertisements instead.
- Windows users can encounter GitHub repositories offering farm bots and auto clickers that actually contain Lumma Stealer cryptors.
What is Hamster Kombat?
Hamster Kombat is an in-app Telegram clicker game where the players earn fictional currency by completing simple tasks, with incentives to log into the game at least daily. As in other mobile clicker games, the basic gameplay of Hamster Kombat involves tapping the screen repeatedly to score more in-game points. A screenshot illustrating the game’s interface can be seen in Figure 1.
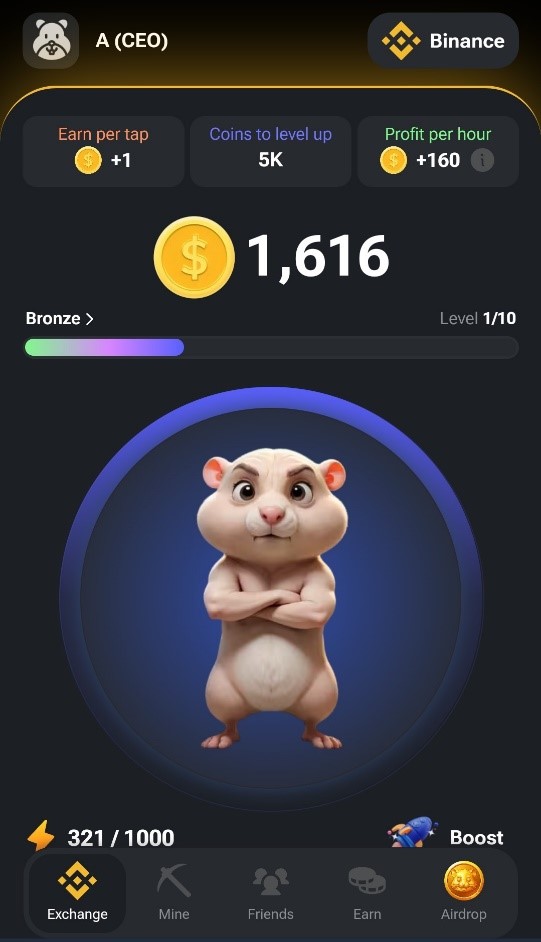
Launched in March 2024, Hamster Kombat seems to be gaining in popularity quite quickly. In June 2024, the developers claimed that their game had already managed to reach 150 million active users. Seeing as this would put Hamster Kombat – a game aimed just at the cryptocurrency enthusiast subset of mobile gamers, and available only through Telegram – in the top 20 most-played mobile games of all time, the claim should be taken with a grain of salt. Nevertheless, the game is undoubtedly popular: the official Hamster Kombat account on X has more than 10 million followers, and the Hamster Kombat Announcement channel has more than 50 million subscribers as of the publication of this blogpost.
Unsurprisingly, the main reason behind the rapidly rising interest in Hamster Kombat is the players’ desire to earn money by playing the game: Hamster Kombat’s development roadmap includes plans for launching a new cryptocoin token tied to the game. The token should subsequently be distributed to the players based on meeting certain criteria, a technique also known as an airdrop.
The team behind Hamster Kombat seems to be trying to replicate the success of another Telegram-based game called Notcoin, which in May 2024 introduced the NOT token on Telegram’s blockchain platform The Open Network (TON) and airdropped it to the players based on their in-game scores. NOT token’s launch was very successful, with some claiming it was the biggest crypto-gaming-token launch of 2024 so far.
The Hamster Kombat token drop is also supposed to use the TON network. As opposed to Notcoin, however, the number of tokens received will not depend on total score but on other factors, such as profit-per-hour.
Threat analysis
As was to be expected, the success of Hamster Kombat has also brought out cybercriminals, who have already started to deploy malware targeting the players of the game. ESET Research has uncovered threats going after both Android and Windows users. Android users are targeted by spyware and fake app stores full of unwanted advertisements, while Windows users can encounter GitHub repositories with Lumma Stealer cryptors.
As any project promising earnings for little effort, the game itself is also on the radar of cybersecurity experts and government officials, who are warning of potential financial risks involved in playing. So far, ESET has not seen any malicious activity from the original app.
Android threats
We identified and analyzed two types of threats targeting Android users: a malicious app that contains the Android spyware Ratel and fake websites that impersonate app store interfaces claiming to have Hamster Kombat available for download.
Ratel spyware
ESET researchers found a Telegram channel (https://t[.]me/hamster_easy) distributing Android spyware, named Ratel, disguised as Hamster Kombat; see Figure 2.
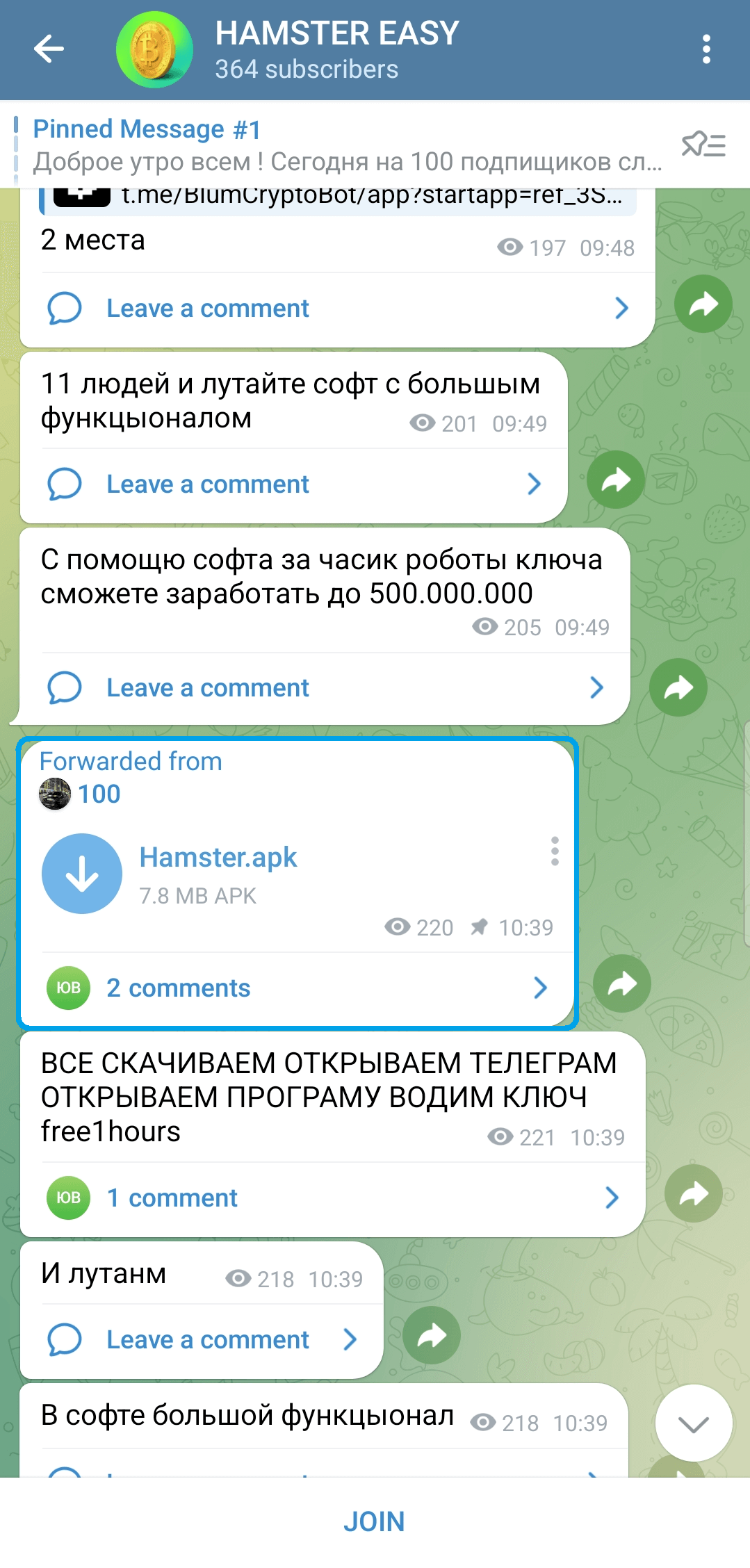
This malware is capable of stealing notifications and sending SMS messages. The malware operators use this functionality to pay for subscriptions and services with the victim’s funds without the victim noticing.
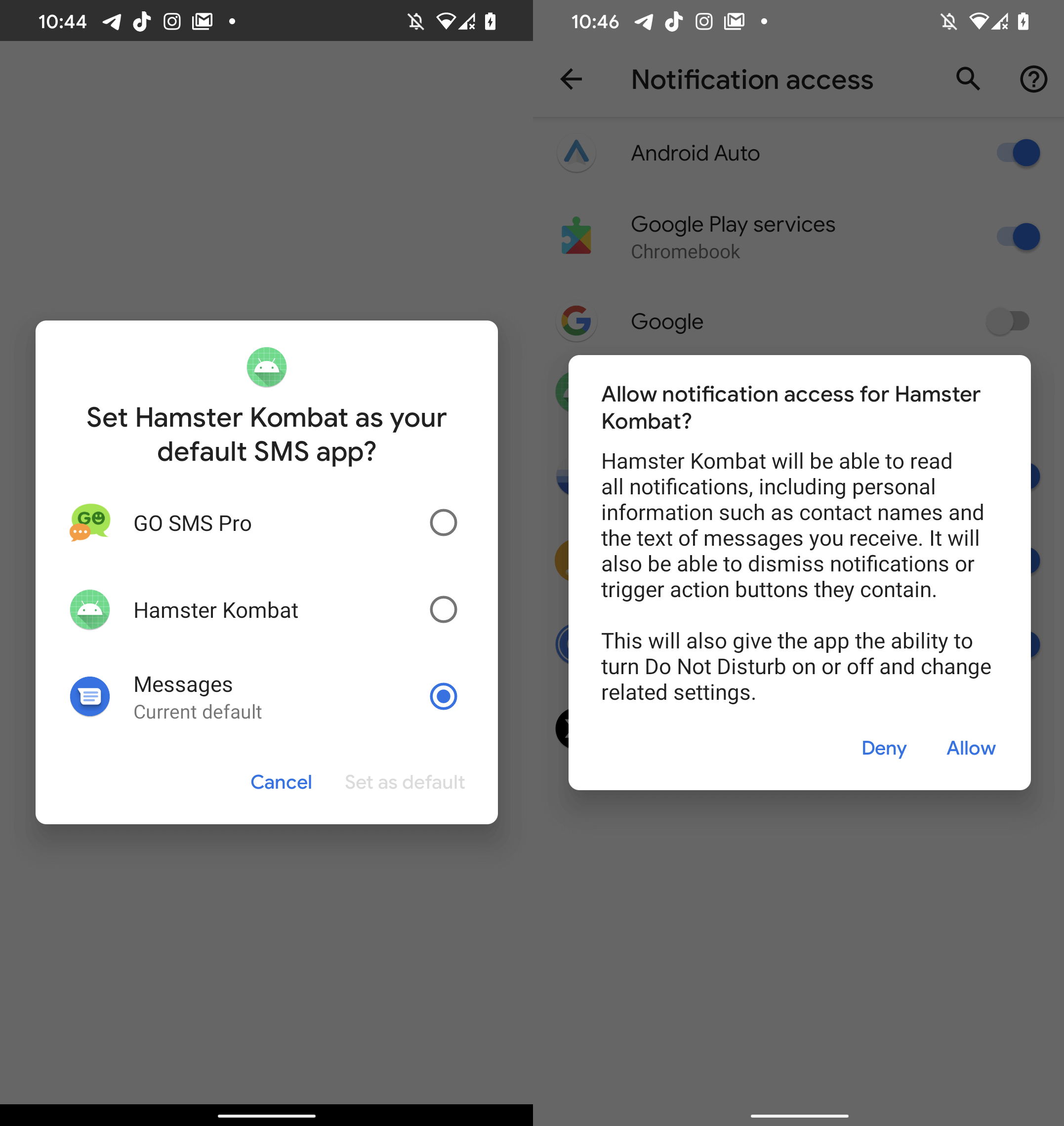
While the malicious app misuses the name Hamster Kombat to attract potential victims, it contains no functionality found within the game and even lacks a user interface altogether. As displayed in Figure 3, upon startup, the app requests notification access permission, and asks to be set as the default SMS application. Once these permissions are granted, the malware gets access to all SMS messages and is able to intercept all displayed notifications.
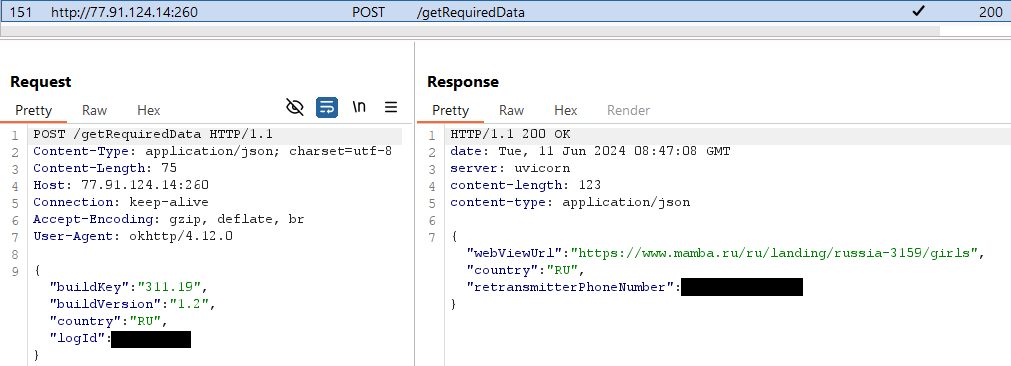
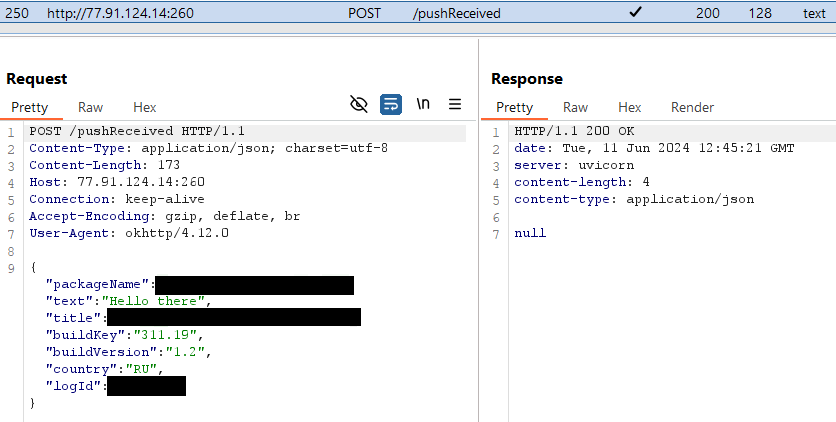
Ratel then initiates communication with its C&C server (http://77.91.124[.]14:260), and as a response, receives a phone number: see Figure 4. Afterwards, it sends an SMS message with the text Привет! Набери мне: logID (translation: Hello! Call me) to the that phone number, which most likely belongs to the malware operators.
The threat actors then become capable of controlling the compromised device via SMS: the operator message can contain a text to be sent to a specified number, or even instruct the device to call the number. The malware is also able to check the victim’s current banking account balance for Sberbank Russia by sending a message with the text баланс (translation: balance) to the number 900. This is most probably done in order to decide whether the operators should pursue further attack scenarios to access the victim’s funds.
Ratel also abuses notification access permissions to hide notifications from over 200 apps based on a hardcoded list (see the Appendix for the complete list). The list contains apps such as Telegram, WhatsApp, and several SMS messaging apps. If the affected device receives a notification from an app on the list, the victim will not be able to see it. Hiding is the only action the malware does with these notifications; they are not forwarded to the C&C server. Most likely, the purpose of intercepting the notifications is to prevent the victim from discovering confirmation messages sent by subscription services.
As shown in Figure 5, in case there is a notification from an app not included in the list, Ratel lets the user see it, while also forwarding it to the C&C server. We think this might be done so that the operators can check whether a new app needs to be added to the list.
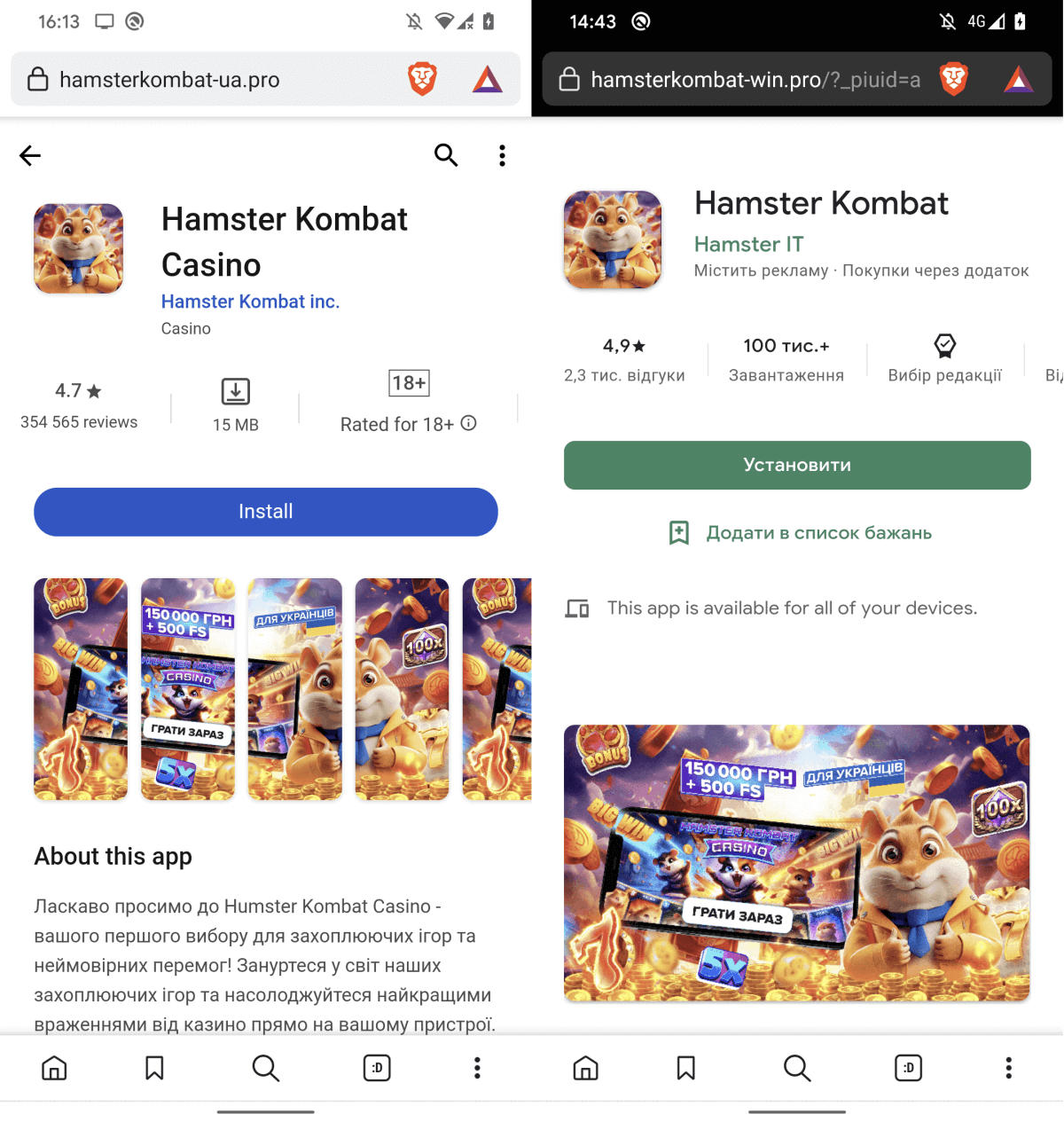
Fake websites
Besides the app with the Ratel spyware, we also discovered fake application storefronts claiming to offer Hamster Kombat for download. However, tapping the Install or Open buttons only leads the user to unwanted advertisements. Examples of the fake websites can be found in Figure 6.
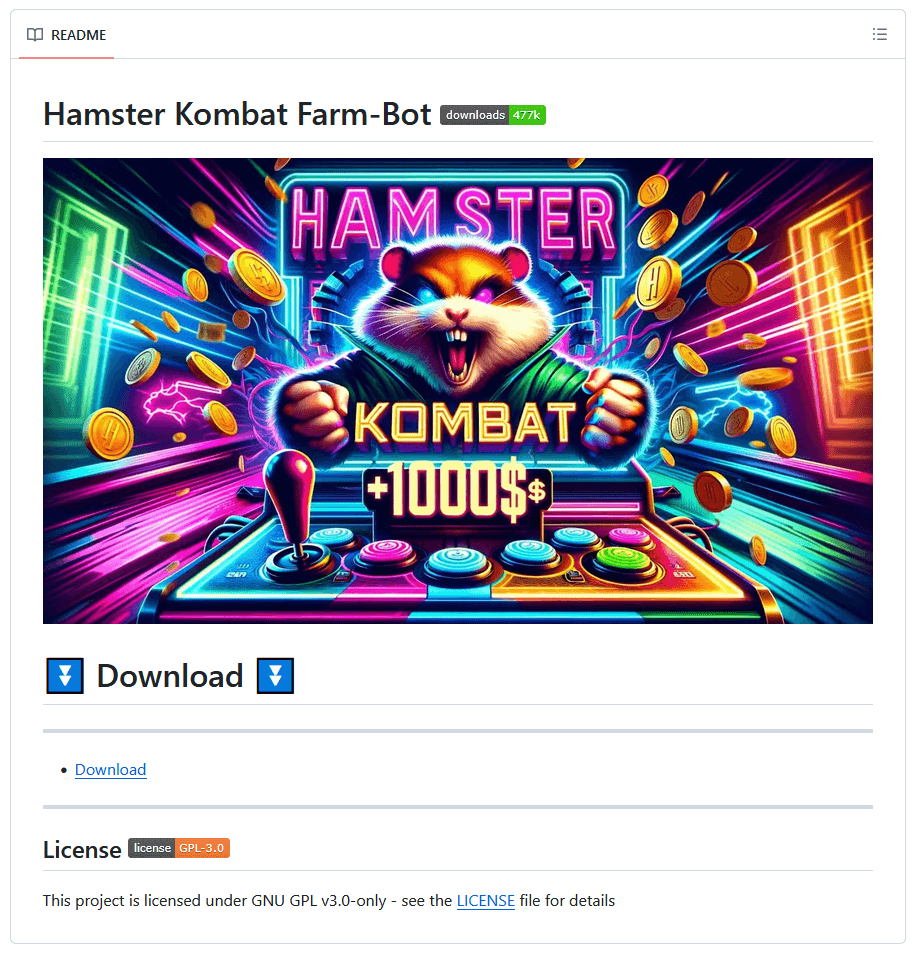
Windows threats
Even though Hamster Kombat is a mobile game, we also found malware abusing the game’s name to spread on Windows. Cybercriminals try to entice Windows users with auxiliary tools that claim to make maximizing in-game profits easier for the players. Our research revealed GitHub repositories (see Figure 7) offering Hamster Kombat farm bots and autoclickers, which are tools that automate clicks in a game. These repositories actually turned out to conceal cryptors from the infamous Lumma Stealer malware.
Lumma Stealer is an infostealer offered as malware-as-a-service, available for purchase on the dark web and on Telegram. First observed in 2022, this malware is commonly distributed via pirated software and spam, and targets cryptocurrency wallets, user credentials, two-factor authentication browser extensions, and other sensitive information. Note that Lumma Stealer’s capabilities are not covered by the MITRE ATT&CK matrix in this blogpost, since the focus is on the cryptors that deliver this infostealer, not on the infostealer itself.
The GitHub repositories we found either had the malware available directly in the release files, or contained links to download it from external file-sharing services. We identified three different versions of Lumma Stealer cryptors lurking within the repositories: C++ applications, Go applications, and Python applications. Of the three, only the Python applications have a graphical user interface (GUI).
C++ applications
In the case of the C++ applications, Lumma Stealer is encrypted via the RC4 cipher and embedded in the executable the victim downloads. Once executed, the application injects Lumma Stealer into the newly created process C:WindowsMicrosoft.NETFrameworkv4.0.30319RegAsm.exe.
Go applications
For the Go applications, Lumma Stealer is also embedded in the executable, but this time, it is encrypted using AES-GCM. The cryptor uses copied and obfuscated code from go_libpeconv, a Go library for loading PE files, to do process hollowing on the first file found with the .exe extension under the C:Windows directory.
Python applications
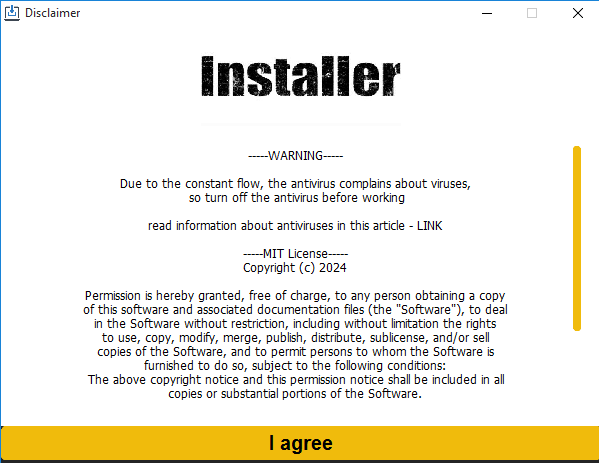
The Python applications were either bundled with PyInstaller or compiled with Nuitka. When the victim runs the file downloaded from the GitHub repository, a fake installer window with an I agree button appears, as can be seen in Figure 8. Upon clicking the button, the program connects to an FTP server and downloads a password-protected ZIP archive (password: crypto123) containing the cryptor with Lumma Stealer embedded. We found C++ and Go cryptors on the FTP server, which leads us to the conclusion that these applications are probably different versions of the same malware family.
Once the window is closed, the cryptor sends the C&C server the timestamps of when the victim clicked on the I agree button and when the malware was run. This data is sent only once and there is no further C&C communication involving the cryptor. As shown in Figure 9, we found a comment report to telegramm [sic] in the Python source code of the malware, meaning that probably the data is sent from the C&C to the operators’ Telegram account or channel at some point.

Conclusion
Hamster Kombat’s popularity makes it ripe for abuse, which means that it is highly likely that the game will attract more malicious actors in the future. While many copycat Hamster Kombat apps appear to be malware-free, we discovered a remotely controlled trojan distributed via Telegram disguised as the game. The malware is capable of sending SMS messages, making calls, and concealing its actions by hiding notifications that might suggest the device is compromised. Apart from the Android trojan, we also found fake app stores claiming to offer Hamster Kombat for download; the links, however, often lead to unwanted advertisements. Finally, on the Windows platform, we uncovered GitHub repositories that lure gamers in with the promise of Hamster Kombat farm bots and autoclickers but that, in reality, serve the victims with cryptors containing Lumma Stealer.
Thanks to Anton Cherepanov for his contributions.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.comESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
A comprehensive list of Indicators of Compromise (IoCs) and samples can be found in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
ACD260356E3337F775E1 |
Hamster.apk |
Android/Spy.Ratel.A |
Android malware impersonating Hamster Kombat. |
|
C51266A3F60984897645 |
Setup.exe |
Win32/Kryptik.HWZI |
Windows malware targeting Hamster Kombat players. |
|
7BE8D85301C9CCE39455 |
Hamster-Kombat.exe |
Win32/Kryptik.HXDB |
Windows malware targeting Hamster Kombat players. |
|
91351285CB1448D22C88 |
update.exe |
WinGo/TrojanDropper. |
Windows malware targeting Hamster Kombat players. |
|
46A83FBCF1AA068C8F6C |
Setup_v1.1.2.exe |
WinGo/TrojanDropper. |
Windows malware targeting Hamster Kombat players. |
|
2B17E3A93A59E4F9350F |
update.exe |
Win32/Kryptik.HXIB |
Windows malware targeting Hamster Kombat players. |
|
9DEB6D5E9209A9EC2B8D |
update.exe |
Win32/Kryptik.HXIB |
Windows malware targeting Hamster Kombat players. |
|
16B815C14941ECFE164B |
update.exe |
Win32/Kryptik.HXIB |
Windows malware targeting Hamster Kombat players. |
|
2E257D5ABB0E76AB57A0 |
Open.exe |
WinGo/Agent.VY |
Windows malware targeting Hamster Kombat players. |
|
78F1B8C6087348EC83B7 |
update.exe |
Win32/Kryptik.HXIB |
Windows malware targeting Hamster Kombat players. |
|
6F14278BC5DEA7803C9D |
AUTOCLICKER.exe |
Win32/GenKryptik.GXGC |
Windows malware targeting Hamster Kombat players. |
|
812799738C18ACB88D5C |
HAMSTER KOMBAT BALANCE HACK.exe |
Win32/Kryptik.HXDV |
Windows malware targeting Hamster Kombat players. |
|
B11B1CD89EA5F0D562D1 |
Hamster-Kombat-NEW.exe |
Win32/Kryptik.HXCA |
Windows malware targeting Hamster Kombat players. |
|
FE51C824245FFE8CB509 |
update.exe |
Win32/Kryptik.HXIB |
Windows malware targeting Hamster Kombat players. |
|
592215355FB25521FD76 |
update.exe |
Win32/Kryptik.HXDB |
Windows malware targeting Hamster Kombat players. |
|
92B028A302FAA31BDB78 |
update.exe |
Win32/Kryptik.HXDB |
Windows malware targeting Hamster Kombat players. |
|
12B0BD4B2F1EB173B782 |
Run.exe |
Python/TrojanDownloader. |
Windows malware targeting Hamster Kombat players. |
|
3021E974D78544E62F43 |
Install.exe |
Python/TrojanDownloader. |
Windows malware targeting Hamster Kombat players. |
|
F79C575D0D887427B7B3 |
Run.exe |
Python/TrojanDownloader. |
Windows malware targeting Hamster Kombat players. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
77.91.124[.]14 |
N/A |
Daniil Yevchenko |
2024‑05‑11 |
Android/Spy.Ratel.A C&C server. |
|
76.76.21[.]164 |
www.hamsterkombat‑ua |
Amazon.com, Inc. |
2024‑06‑08 |
Fake website. |
|
172.67.159[.]114 |
hamsterkombat‑win |
Cloudflare, Inc. |
2024‑06‑13 |
Fake website. |
|
N/A |
www.hamster‑ua[.]pro |
N/A |
2024‑06‑10 |
Fake website. |
|
N/A |
www.ua‑hamster‑kombat |
N/A |
2024‑06‑04 |
Fake website. |
|
N/A |
www.hamster‑kombat‑ua |
N/A |
2024‑06‑04 |
Fake website. |
|
N/A |
www.hamstercasino‑ua‑on |
N/A |
2024‑06‑16 |
Fake website. |
|
104.21.86[.]106 |
incredibleextedwj |
Cloudflare, Inc. |
2024‑04‑13 |
Lumma Stealer C&C server. |
|
104.21.11[.]250 |
productivelookewr |
Cloudflare, Inc. |
2024‑04‑14 |
Lumma Stealer C&C server. |
|
104.21.89[.]202 |
tolerateilusidjukl |
Cloudflare, Inc. |
2024‑04‑13 |
Lumma Stealer C&C server. |
|
104.21.95[.]19 |
shatterbreathepsw |
Cloudflare, Inc. |
2024‑04‑13 |
Lumma Stealer C&C server. |
|
104.21.76[.]102 |
detailbaconroollyws |
Cloudflare, Inc. |
2024‑05‑26 |
Lumma Stealer C&C server. |
|
104.21.74[.]118 |
horsedwollfedrwos |
Cloudflare, Inc. |
2024‑05‑26 |
Lumma Stealer C&C server. |
|
104.21.55[.]248 |
patternapplauderw |
Cloudflare, Inc. |
2024‑05‑26 |
Lumma Stealer C&C server. |
|
104.21.22[.]94 |
understanndtytonyguw |
Cloudflare, Inc. |
2024‑05‑26 |
Lumma Stealer C&C server. |
|
104.21.63[.]189 |
liabiliytshareodlkv |
Cloudflare, Inc. |
2024‑06‑07 |
Lumma Stealer C&C server. |
|
104.21.74[.]169 |
notoriousdcellkw |
Cloudflare, Inc. |
2024‑06‑07 |
Lumma Stealer C&C server. |
|
104.21.59[.]152 |
conferencefreckewl |
Cloudflare, Inc. |
2024‑06‑07 |
Lumma Stealer C&C server. |
|
104.21.76[.]157 |
flourhishdiscovrw |
Cloudflare, Inc. |
2024‑06‑07 |
Lumma Stealer C&C server. |
|
104.21.71[.]242 |
meltedpleasandtws |
Cloudflare, Inc. |
2024‑05‑30 |
Lumma Stealer C&C server. |
|
104.21.53[.]89 |
varianntyfeecterd |
Cloudflare, Inc. |
2024‑05‑25 |
Lumma Stealer C&C server. |
|
104.21.16[.]251 |
snaillymarriaggew |
Cloudflare, Inc. |
2024‑06‑12 |
Lumma Stealer C&C server. |
|
104.21.62[.]244 |
thidrsorebahsufll |
Cloudflare, Inc. |
2024‑05‑29 |
Lumma Stealer C&C server. |
|
104.21.75[.]100 |
distincttangyflippan |
Cloudflare, Inc. |
2024‑05‑30 |
Lumma Stealer C&C server. |
|
104.21.30[.]167 |
greentastellesqwm |
Cloudflare, Inc. |
2024‑05‑29 |
Lumma Stealer C&C server. |
|
104.21.28[.]32 |
considerrycurrentyws |
Cloudflare, Inc. |
2024‑05‑26 |
Lumma Stealer C&C server. |
|
104.21.92[.]10 |
corruptioncrackywosp |
Cloudflare, Inc. |
2024‑05‑17 |
Lumma Stealer C&C server. |
|
104.21.52[.]185 |
negotitatiojdsuktoos |
Cloudflare, Inc. |
2024‑05‑18 |
Lumma Stealer C&C server. |
|
104.21.32[.]80 |
museumtespaceorsp |
Cloudflare, Inc. |
2024‑05‑18 |
Lumma Stealer C&C server. |
|
104.21.76[.]185 |
stickyyummyskiwffe |
Cloudflare, Inc. |
2024‑05‑29 |
Lumma Stealer C&C server. |
|
104.21.26[.]6 |
vivaciousdqugilew |
Cloudflare, Inc. |
2024‑05‑29 |
Lumma Stealer C&C server. |
|
146.19.207[.]14 |
N/A |
Cloud Hosting Solutions, Limited. |
N/A |
Windows malware targeting Hamster Kombat players C&C server. |
Code-signing certificates
|
Serial number |
0997C56CAA59055394D9A9CDB8BEEB56 |
|
Thumbprint |
15F760D82C79D22446CC7D4806540BF632B1E104 |
|
Subject CN |
NVIDIA Corporation |
|
Subject O |
NVIDIA Corporation |
|
Subject L |
Santa Clara |
|
Subject S |
N/A |
|
Subject C |
US |
|
Valid from |
2023-01-13 00:00:00 |
|
Valid to |
2026-01-16 23:59:59 |
MITRE ATT&CK techniques
This table was built using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Phishing |
Android spyware Ratel has been distributed using an unofficial Telegram channel. |
|
|
Persistence |
Event Triggered Execution: Broadcast Receivers |
Android spyware Ratel registers to receive the SMS_RECEIVED, SMS_DELIVER, PACKAGE_REMOVED, PACKAGE_REPLACED, PACKAGE_ADDED, and PACKAGE_CHANGE broadcast intents to activate itself. |
|
|
Collection |
Access Notifications |
Android spyware Ratel can collect messages from various apps. |
|
|
Command and Control |
Out of Band Data |
Android spyware Ratel can use SMS to receive commands to execute. |
|
|
Exfiltration |
Exfiltration Over C2 Channel |
Android spyware Ratel exfiltrates data using HTTP. |
|
|
Impact |
Call Control |
Android spyware Ratel can make phone calls. |
|
|
SMS Control |
Android spyware Ratel can send and receive SMS messages. |
This table was built using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Defense Evasion |
Obfuscated Files or Information: Embedded Payloads |
Lumma Stealer uses C++ and Go binaries to embed its payload. |
|
|
Process Injection: Process Hollowing |
Lumma Stealer uses process hollowing. |
||
|
Command and Control |
Application Layer Protocol: Web Protocols |
Lumma Stealer communicates with the C&C server via HTTP |
|
|
Application Layer Protocol: File Transfer Protocols |
Lumma Stealer downloader uses FTP to download the payload. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
Lumma Stealer exfiltrates the victim’s data to the C&C server. |
Appendix
Following is the list of applications from which the Ratel malware hides notifications:
|
com.android.incallui com.texter.voxuedigital com.zeopoxa.fitness.cycling.bike com.coloros.gallery3d com.whatsapp applock.lockapps.fingerprint.password.lockit com.playrix.township ru.yandex.taximeter notification com.google.android.apps.wellbeing com.rstgames.durak com.duolingo com.blinkmap limehd.ru.ctv com.google.android.packageinstaller com.dreamy.screen.plot cn.baos.watch.w100 com.sec.android.gallery3d pedometer.stepcounter.calorieburner. com.facebook.lite com.transsnet.store ru.auto.ara weata.taxi com.samsung.android.game.gamehome com.mazegame.notpopsong.popmaze ru.mail.cloud com.sec.android.app.shealth in.sweatco.app ru.yandex.yandexnavi com.yandex.searchapp.beta ru.mail.mailapp com.facebook.katana com.samsung.android.scloud uz.kundalik.mobile com.relaxplayer.android com.sh.smart.caller ru.aalab.androidapp.uamp. com.mediatek.simprocessor com.allstarunion.myths com.google.android.setupwizard com.mediatek.callrecorder com.android.updater nevada.dos.governor com.uznewmax.theflash com.app.champion.pro dev.ragnarok.fenrir_public com.desktop.genius.spote com.snaptube.premium com.android.providers.downloads com.sec.android.app.sbrowser com.mytube.floatviewer2 com.google.android.dialer com.samsung.android.game.gametools com.google.android.googlequicksearchbox com.google.android.apps.messaging com.google.android.youtube com.xiaomi.hm.health com.accurate.weather.forecast.live yo.app.free ma.safe.bn com.huawei.mediacontroller org.telegram.plus com.devexpert.weather ru.bristol.bristol_app com.sec.android.app.samsungapps org.telegram.messenger com.gamegou.football com.dating.mylove re.sova.five com.namaztime com.allgoritm.youla com.vtosters.lite com.mixerbox.tomodoko com.google.android.apps.maps com.taxsee.taxsee drug.vokrug com.coloros.alarmclock com.launcher.brgame com.mxtech.videoplayer.ad com.yandex.browser com.tencent.ig com.huawei.contacts ru.yandex.uber com.grif.vmp us.ultrasurf.mobile.ultrasurf com.waplog.social com.huawei.health com.miui.gallery org.findmykids.child ru.rt.smarthome sg.bigo.live com.onlyspark com.boombitgames.DrivingSchoolParking app.nicegram cn.xiaofengkj.fitpro ru.euphoria.moozza.new com.cuttosave.tobehero.ropepuzzle com.sec.android.daemonapp com.google.android.apps.photos com.kiloo.subwaysurf free.zaycev.net com.hmdglobal.app.camera com.samsung.android.dynamiclock ru.vk.store com.dywx.larkplayer com.pinterest com.vk.love com.osp.app.signin com.samsung.android.app.smartcapture |
net.hubalek.android.reborn.beta ru.farpost.dromfilter ru.dublgis.dgismobile ru.stoloto.mobile com.nemo.vidmate com.babilonm.app com.samsung.android.lool com.android.dialer com.internet.speed.meter.lite com.twitter.android free.tube.premium.advanced.tuber com.avito.android com.android.providers.contacts ru.fotostrana.sweetmeet ru.cardsmobile.mw3 com.soundcloud.android com.android.ztescreenshot com.heytap.browser ir.ilmili.telegraph com.android.messaging com.gbox.com.instagram.android ru.gdemoideti.child com.truecaller cc.coolline.client.pro com.samsung.android.oneconnect com.chess com.ihappydate com.huawei.systemmanager com.instagram.android com.dts.freefireth com.android.settings com.viber.voip com.livescore ru.ok.android com.snapchat.android com.huami.watch.hmwatchmanager com.word.grid.challenge com.whatsapp.w4b com.iMe.android com.evermatch com.android.vending com.discord com.eapoker.durak.international com.vkontakte.android com.google.android.gm com.gbox.com.google.android.youtube com.xiaomi.discover ru.cian.main pedometer.steptracker. steptracker.healthandfitness. com.beermoneygames.demolition3 org.thunderdog.challegram com.google.android.apps.nbu.files com.android.systemui com.transsion.batterylab org.telegram.mdgram com.vk.im com.android.chrome org.telegram.messenger.web com.instagram.lite tv.twitch.android.app android com.axlebolt.standoff2 ru.yandex.searchplugin friends.denied.bend com.shaiban.audioplayer.mplayer ru.yandex.yandexmaps com.toto.pwapp marshall.threesome.vibrator video.like ru.yandex.weatherplugin belarus.topless.income com.ss.android.ugc.trill mood.cove.humidity ru.tander.magnit com.tblenovo.lewea com.rockbite.zombieoutpost com.isharing.isharing com.google.android.apps.magazines com.heytap.market org.vidogram.lite videoeditor.videorecorder.screenrecorder com.samsung.android.incallui com.yingsheng.hayloufun com.nektome.chatruletka.voice com.oplus.games ru.tsk.ftc.bender.qpay com.miui.securitycenter com.coloros.gamespaceui tech.jm com.yandex.searchapp app.source.getcontact com.sec.android.app.camera com.facebook.orca com.devuni.flashlight provide.dairy.measurements com.android.contacts com.xiaomi.mi_connect_service com.taxsee.driver com.coinmarketcap.android com.vkmp3mod.android mans.auto.phone.cooling.master ru.dnevnik.app com.google.android.gms com.miui.player com.lenovo.anyshare.gps com.samsung.android.app.tips org.aka.messenger com.sec.android.app.myfiles |

