Scams
Your humble phone number is more valuable than you may think. Here’s how it could fall into the wrong hands – and how you can help keep it out of the reach of fraudsters.
15 Jul 2024
•
,
7 min. read

What might be one of the easiest ways to scam someone out of their money – anonymously, of course?
Would it involve stealing their credit card data, perhaps using digital skimming or after hacking into a database of sensitive personal information? While effective, these methods may be resource-intensive and require some technical prowess.
What about stealing payment info via fake websites? This may indeed fit the bill, but spoofing legitimate websites (and email addresses to “spread the word”) may not be for everybody, either. The odds are also high that such ploys will be spotted in time by the security-savvy among us or thwarted by security controls.
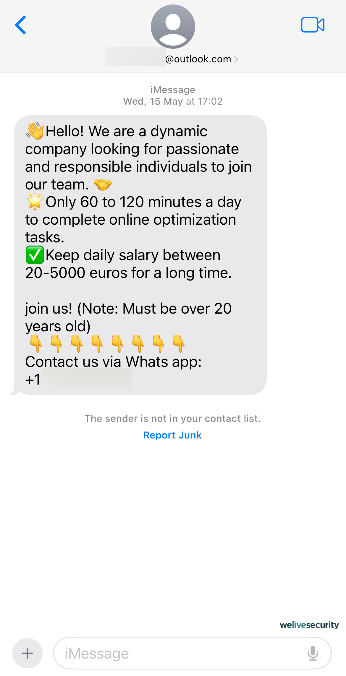
Instead, bad actors are turning to highly scalable operations that rely on sophisticated social engineering tactics and costs little to operate. Using voice phishing (also called vishing) and message scams (smishing), these operations have been developed into a scam call-center industry worth billions of dollars.
For starters, these ploys may not require much in the way of specialized or technical skills. Also, a single person (often a victim of human trafficking) can, at a time, ensnare multiple unwitting victims in various flavors of fraud. These often involve pig butchering, cryptocurrency schemes, romance scams, and tech support fraud, each of which spins a compelling yarn and preys on some of what actually makes us human.
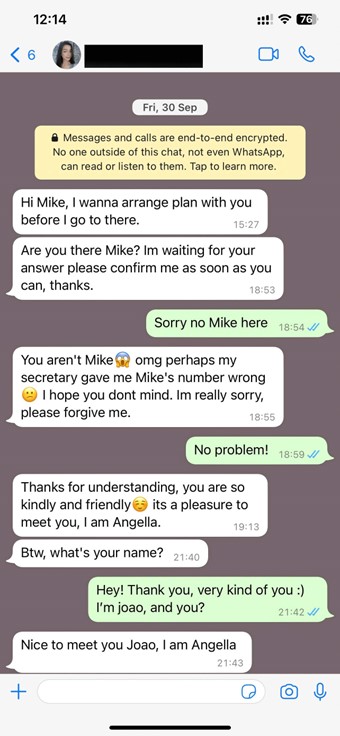
Hello? Is this thing on?
Imagine receiving a call from your bank to inform you that your account has been breached and in order to keep your money safe, you need to share your sensitive details with them. The urgency in the voice of the bank’s “employee” may indeed be enough to prompt you to share your sensitive information. The problem is, this person might not be from your bank – or they may not even exist at all. It could be just a fabricated voice, but still sound completely natural.
This isn’t at all uncommon and cautionary tales from recent years abound. Back in 2019, a CEO was scammed out of almost US$250,000 by a convincing voice deepfake of their parent company’s chief. Similarly, a finance worker was tricked via a deepfake video call in 2024, costing their firm US$25 million.
AI, the enabler
With modern AI voice cloning and translation capabilities, vishing and smishing have become easier than ever. Indeed, ESET Global Cybersecurity Advisor Jake Moore demonstrated the ease with which anybody can create a convincing deepfake version of someone else – including someone you know well. Seeing and hearing are no longer believing.
AI is lowering the barrier of entry for new adversaries, serving as a multipronged tool to gather data, automate tedious tasks, and globalize their reach. Consequently, phishing using AI-generated voices and text will probably become more commonplace.
On this note, a recent report by Enea noted a 1,265% rise in phishing scams since the launch of ChatGPT in November 2022 and spotlighted the potential of large language models to help fuel such malicious operations.
What’s your name, what’s your number?
As evidenced by Consumer Reports research from 2022, people are becoming more privacy-conscious than before. Some 75% of the survey’s respondents were at least somewhat concerned about the privacy of their data collected online, which may include phone numbers, as they are a valuable resource for both identification and advertising.
But now that we’re well past the age of the Yellow Pages, how does this connection between phone numbers and advertising work?
Consider this illustrative example: a baseball fan placed tickets in a dedicated app’s checkout but didn’t complete the purchase. And yet, shortly after closing the app, he received a phone call offering a discount on the tickets. Naturally, he was baffled since he didn’t remember providing his phone number to the app. How did it get his number, then?
The answer is – via tracking. Some trackers can collect specific information from a webpage, so after you’ve filled in their phone number in a form, a tracker could detect and store it to create what is often called personalized content and experience. There is an entire business model known as “data brokering”, and the bad news is that it doesn’t take a breach for the data to become public.
Tracking, data brokers, and leaks
Data brokers vacuum up your personal information from publicly available sources (government licenses/registrations), commercial sources (business partners like credit card providers or stores) as well as by tracking your online activities (activities on social media, ad clicks, etc.), before selling your information to others.
Still, the question on your lips may be: how can scammers obtain other people’s phone numbers?
Naturally, the more companies, sites, and apps you share your personal information with, the more detailed your personal “marketing profile” is. This also increases your exposure to data leaks, since data brokers themselves can experience security incidents. A data broker could also sell your information to others, possibly including bad actors.
But data brokers, or breaches affecting them, aren’t the only source of phone numbers for scammers. Here are some other ways in which criminals can get ahold of your phone number:
- Public sources: Social media sites or online job markets might show your phone number as a means to make a connection. In case your privacy settings are not dialed in correctly or you are not aware of the consequences of revealing your phone number in your social media profile, your number might be available to anyone, even an AI web scraper.
- Stolen accounts: Various online services require your phone number, be it to confirm your identity, to place an order, or to serve as an authentication factor. When your accounts get brute-forced due to weak passwords or one of your online providers suffers a data breach your number could easily leak as well.
- Autodialers: Autodialers call random numbers, and as soon as you answer the call, you may be targeted by a scam. Sometimes these autodialers call just to confirm that the number is in use so that it can be added to a list of targets.
- Mail: Check any of your recent deliveries – these usually have your address visible on the letter/box, but in some cases, they can also have your email or phone number printed on them. What if someone stole one of your deliveries or rummaged through your recycling pile? Considering that data leaks usually contain the same information, this can be very dangerous and grounds for further exploitation.
As an example of a wide-scale breach affecting phone numbers, AT&T recently revealed that millions of customers’ call and text message records from mid-to-late 2022 were exposed in a massive data leak. Nearly all of the company’s customers and people using the cell network have had their numbers, call durations, and number of call interactions exposed. While call and text contents are allegedly not among the breached data, customer names and numbers can still be easily linked, as reported by CNN.
Reportedly, the blame can be put on a third-party cloud platform, which a malicious actor had accessed. Coincidentally, the same platform has had several cases of massive leaks linked to it in recent years.
How to protect your phone number
So, how can you protect yourself and your number? Here are a few tips:
- Be aware of phishing. Never answer unsolicited messages/calls from foreign numbers, don’t click on random links in your emails/messages, and remember to keep cool and think before you react to a seemingly urgent situation, because that’s how they get you.
- Ask your service provider about their SIM security measures. They might have an option for card locks to protect against SIM swapping, for example, or additional account security layers to prevent scams like call forwarding.
- Protect your accounts with two-factor authentication, ideally using dedicated security keys, apps, or biometrics instead of SMS-based verification. The latter can be intercepted by bad actors with relative ease. Do the same for service provider accounts as well.
- Think twice before providing your phone number to a website. While having it as an additional recovery option for your various apps might be useful, other methods like secondary emails/authenticators could offer a more secure alternative.
- For online purchases, consider using a pre-paid SIM card or a VoIP service instead of your regular phone number.
- Use a mobile security solution with call filtering, as well as make sure that third-party cookies in your web browser are blocked, and explore other privacy-enhancing tools and technologies.
In a world that increasingly relies on online record keeping, there is a low chance that your number won’t be preserved by a third party somewhere. And as the AT&T incident suggests, relying on your own carrier’s security is also rather problematic. This doesn’t mean that you should remain in a state of constant paranoia, though.
On the other hand, it highlights the importance of committing to proper cyber hygiene and being aware of your data online. Vigilance is also still key, especially when considering the implications of this new, AI-powered (under)world.
