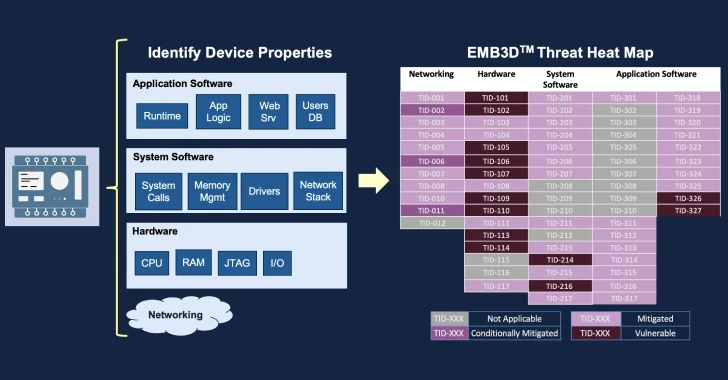
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments.
“The model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with the security mechanisms required to mitigate them,” the non-profit said in a post announcing the move.
A draft version of the model, which has been conceived in collaboration with Niyo ‘Little Thunder’ Pearson, Red Balloon Security, and Narf Industries, was previously released on December 13, 2023.
EMB3D, like the ATT&CK framework, is expected to be a “living framework,” with new and mitigations added and updated over time as new actors, vulnerabilities, and attack vectors emerge, but with a specific focus on embedded devices.
The ultimate goal is to provide device vendors with a unified picture of different vulnerabilities in their technologies that are prone to attacks and the security mechanisms for mitigating those shortcomings.
Analogous to how ATT&CK offers a uniform mechanism for tracking and communicating threats, EMB3D aims to offer a central knowledge base of threats targeting embedded devices.
“The EMB3D model will provide a means for ICS device manufacturers to understand the evolving threat landscape and potential available mitigations earlier in the design cycle, resulting in more inherently secure devices,” Pearson noted at the time.
“This will eliminate or reduce the need to ‘bolt on’ security after the fact, resulting in more secure infrastructure and reduced security costs.”
In releasing the framework, the idea is to embrace a secure-by-design approach, thereby allowing companies to release products that have a reduced number of exploitable flaws out of the box and have secure configurations enabled by default.
Research that operational technology (OT) cybersecurity company Nozomi Networks released last year revealed that threat actors have opportunistically targeted industrial environments by exploiting vulnerabilities, abusing credentials, and phishing for initial access, DDoS attempts, and trojan execution.
Adversaries, the company said, have particularly ramped up attacks targeting flaws discovered in OT and IoT devices used across food and agriculture, chemical, water treatment, manufacturing, and energy sectors.
“EMB3D provides a cultivated knowledge base of cyber threats to devices, including those observed in the field environment or demonstrated through proofs-of-concept and/or theoretic research,” the non-profit said.
“These threats are mapped to device properties to help users develop and tailor accurate threat models for specific embedded devices. For each threat, suggested mitigations are exclusively focused on technical mechanisms that device vendors should implement to protect against the given threat, with the goal of building security into the device.”