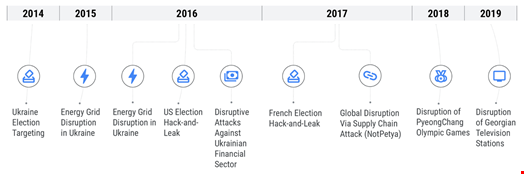
The Russian-backed threat actor known as Sandworm has become such a prominent ally of the Kremlin in the Ukraine war that Mandiant has decided to graduate the group into a named Advanced Persistent Threat (APT) group, APT44.
In a new report, the Google-owned cybersecurity firm revealed that Sandworm has been responsible for almost all the disruptive and destructive operations against Ukraine over the past decade.
Since the outbreak of the war in Ukraine, Sandworm has operated as an umbrella organization for a spectrum of different cyber operations targeting Ukraine and its allies, from influence operations and so-called hacktivist-led disruptive attacks to destructive attacks.
Mandiant also assessed with high confidence that Sandworm’s operations were closely coordinated with the Kremlin to help the Russian military gain a wartime advantage.
A Nebulous Group with Close Ties to the Kremlin
Sandworm is a nebulous Russian-backed cyber threat group whose malicious activity was first detected in 2014 but could date from the 2000s.
The group, which has been given several names over the years, such as Voodoo Bear, Iridium, Seashell Blizzard, Iron Viking, Telebots, and now APT44, is believed to be run by Military Unit 74455, a cyber warfare unit of the Russian military intelligence service (GRU).
This highly skilled cyber-malicious group is allegedly responsible for wide-scale cyber-attacks like the December 2015 Ukraine power grid hack and the 2017 cyberattacks on Ukraine using the NotPetya malware.
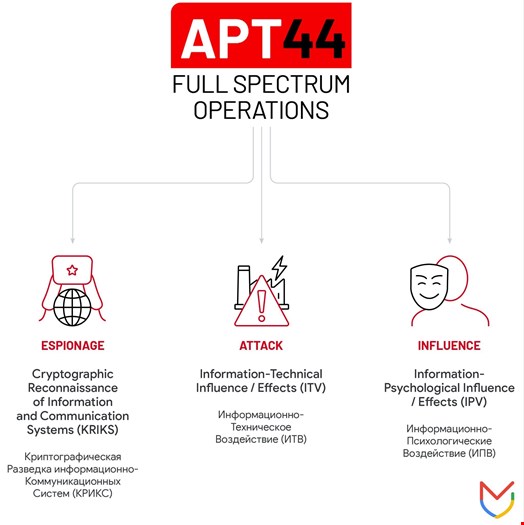
Unlike most state-sponsored cyber-malicious groups, Sandworm does not specialize in one specific mission (e.g. intelligence collection, sabotage), but rather engages in the full spectrum of espionage, attack, and influence operations.
In its report, Mandiant argued that Sandworm’s multipronged approach makes it the most central cyber ally to the Kremlin.
“APT44 stands apart in how it has honed each of these capabilities and sought to integrate them into a unified playbook over time,” the report noted.
“Each of these respective components, and APT44’s efforts to blend them for combined effect, are foundational to Russia’s guiding ‘information confrontation’ concept for cyber warfare.”
War in Ukraine: Sandworm’s Shift Towards Cyber Espionage
Sandworm’s diverse cyber capabilities have significantly benefited the Russian government since the beginning of the war in Ukraine.
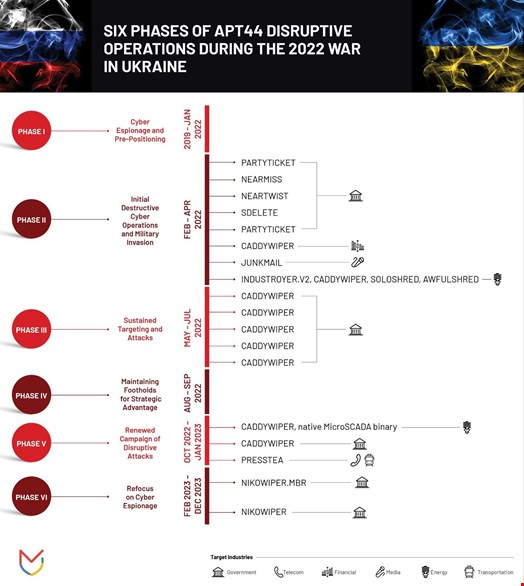
“Throughout Russia’s war, APT44 has waged a high-intensity campaign of cyber sabotage inside Ukraine. Through the use of disruptive cyber tools, such as wiper malware designed to disrupt systems, APT44 has sought to impact a wide range of critical infrastructure sectors,” reads the report.
Mandiant also assessed that some of Sandworm’s cyber campaigns targeting Ukraine have been directly coordinated with the Kremlin and aligned with conventional military activity.
“For example, in October 2022, APT44 disrupted IT and operational technology (OT) systems at a power distribution entity in the midst of Russia’s winter campaign of military and drone strikes targeting Ukraine’s energy grid,” Mandiant researchers wrote.
Over time, Sandworm’s focus on Ukraine has transitioned away from disruption to intelligence collection.
The emphasis on espionage activity is intended to give Russia’s conventional forces a battlefield advantage.
“For example, one long-running APT44 campaign has assisted forward-deployed Russian ground forces to exfiltrate communications from captured mobile devices in order to collect and process relevant targeting data,” Mandiant added.
Sandworm’s Ties to a ‘Hacktivist’ Group Confirmed
In parallel to cyber-attacking Ukrainian victims, Sandworm has continued targeting victims in other countries.
The Mandiant report revealed that Sandworm has close ties with CyberArmyofRussia_Reborn, a ‘hacktivist’ persona that recently claimed to have targeted US and Polish water utilities as well as a French dam.
A local US official later publicly confirmed a “system malfunction” occurred, leading to a tank overflowing at one of the claimed victim facilities.
Finally, the Mandiant report revealed that Sandworm was also behind a campaign targeting Bellingcat and other investigative journalism entities between December 2023 and January 2024.
Mandiant warned that Sandworm will likely continue to be one of the most prominent Russian-aligned threat groups in the future.
