Chinese threat actors are positioning themselves to deploy major cyber-attacks against US critical national infrastructure (CNI) in the event of an escalation of hostilities between the two nations.
Microsoft’s latest Digital Defense Report (MDDR) observed a rise in Chinese state-affiliated actors, such as Circle Typhoon and Volt Typhoon, targeting sectors like transportation, utilities, medical infrastructure and telecommunications.
These campaigns may be intended to enable China to disrupt critical infrastructure and communication between the US and Asia during a geopolitical crisis, the tech giant believes.
Speaking ahead of the report’s release, Tom Burt, corporate vice president, customer security & trust at Microsoft, explained that many of these targets have little to no espionage or intelligence gathering benefit.
“The apparent motivation for this series of cyber-attacks is to preposition access so that they would have the opportunity to disrupt the provision of critical infrastructure services in the event of escalation of hostilities,” he said.
The report noted that these attacks often use unobtrusive techniques and originate from compromised Fortinet devices.
Burt added that Chinese and Russian-linked actors are utilizing sophisticated ‘living off the land’ techniques once they have infiltrated networks, making detection challenging even for experienced incident responders and security operation center (SOC) teams.
“Once they gain access to a network, rather than dropping malware down into that network which is easier to detect and potentially exclude from a network, they utilize the capabilities of the network itself to conduct their pivoting, investigations and exfiltration of data,” he explained.
Microsoft’s analysis follows claims from the US Department of Defense (DoD) in September 2023 that China’s malicious cyber activity informs its preparations for a potential military conflict with the US.
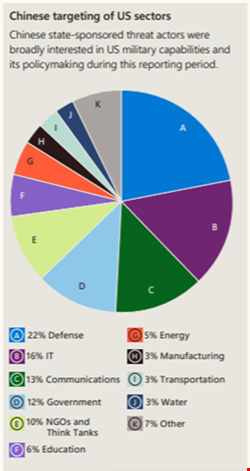
The MDDR also found a significant growth in Chinese intelligence gathering operations in cyberspace in the past year, with Taiwan particularly targeted amid growing regional tensions. There has also been a rise in intelligence gathering across targets in the US and the Pacific Island of Guam, a US territory containing military bases.
Russia Shifts Focus to Espionage After Malware Attacks on Ukraine
Russia has had a renewed emphasis on espionage and intelligence gathering campaigns, following an emphasis on destructive malware campaigns against Ukraine in the previous year, according to the report.
“We’ve seen that largely in support of their war effort, but also more broadly and globally gathering information, much like Russian actors have done for many years,” Burt commented.
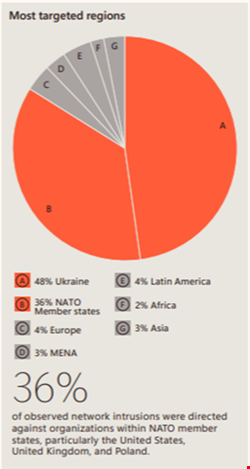
These campaigns have primarily targeted Ukraine, NATO member states, and other countries supportive of Ukraine. Microsoft reported that around half (48%) of state-affiliated network intrusions were directed against Ukrainian organizations from July 2022 to June 2023, with over a third (36%) targeting organizations in NATO member countries.
Russian threat groups engaging in these campaigns include Midnight Blizzard, Star Blizzard and Forest Blizzard. Phishing was the main technique used to launch these attacks, with attackers frequently posing as Western diplomats and Ukrainian officials to gain access to accounts potentially containing information on Western foreign policy on Ukraine, defense plans and intentions.
A prominent tactic used by the GRU-affiliated group Forest Blizzard was exploiting zero-day vulnerabilities to access military and political agencies in Ukraine and NATO member states.
Disinformation Spread by Russian Actors
Additionally, the MDDR highlighted continued efforts by Russian-affiliated threat groups to engage in influence campaigns to sow distrust between populations in Ukraine and countries supporting their war efforts. This includes a campaign leveraging email dissemination and inauthentic documents to spread a narrative in nearby states like Poland, Latvia and Lithuania that government officials may seek forced repatriation of Ukrainians or conscript European citizens for the war in Ukraine.
These state-sponsored actors have also helped amplify and support campaigns encouraging European citizens to demonstrate against their governments providing military assistance to Ukraine.
Burt said these campaigns “are trying to take advantage of a bit of ‘Ukraine fatigue’ among NATO countries and other allies of Ukraine as the war goes on.”
How Partnerships can Build Cyber Resilience
The Microsoft’s report strongly advocated a collective global effort to fight rising cyber threats, urging more organizations to become involved in partnerships between governments, industry and academia.
Microsoft is playing a major role in such global initiatives, including:
- The Cybercrime Atlas. This initiative has been launched by the World Economic Forum (WEF) bringing together over 40 private and public sector members to centralize knowledge sharing, collaboration and research on cybercrime.
- Community of threat intelligence partnerships. The report detailed Microsoft’s partnerships with security industry and government research organizations globally to enable a collective response to emerging threats. This was utilized to rapidly understand the real and potential impact of Volt Typhoon attacks in Guam and the US, which Microsoft said resulted in better protections across the security ecosystem.
- Collective legal action. The MDDR highlighted the collaborative “ground-breaking” lawsuit, which ended the illicit use of Cobalt strike – a popular, legitimate penetration testing tool – in connection with malware and ransomware attacks.
- Advancing open-source security. Leading tech firms, such as Microsoft, Google, Amazon and IBM are collaborating to advance open-source security. This includes projects to develop supply chain security tools.
- Addressing the skills shortage. Microsoft is engaged in strategic partnerships with educational institutions, non-profits, governments and businesses to develop localized cybersecurity and AI skills programs that address market needs. It has also expanded its cybersecurity skills initiative to 28 countries.
- Working with law enforcement. Burt highlighted the need for companies like Microsoft who hold vast amounts actionable threat intelligence, to work with law enforcement agencies in tackling cybercrime. In particular to disrupt cyber-criminals’ technological infrastructure and the way they are paid.
