The growing popularity of online marketplaces has attracted fraudsters preying on unsuspecting buyers and sellers, looking to score payment card information rather than to strike a bargain. ESET researchers have found that one such organized scammer network – which uses Telekopye, a toolkit discovered by ESET Research in 2023 – has expanded its operations to target users of popular accommodation booking platforms.
Last year, we published a two-part blogpost series on Telekopye, a Telegram-based toolkit cybercriminals use to scam people on online marketplaces. The first part focused on Telekopye’s key features, while the second part examined the inner workings of the affiliated scam groups. In this blogpost, we follow up on what has changed in Telekopye operations since our last publication, based on our continued tracking. We look into how these scammer groups have branched out to targeting Booking.com and Airbnb, as well as their various other efforts to optimize their operations and maximize financial gain. Last but not least, we provide guidance on how to stay protected from these scams.
We presented our updated findings on Telekopye at the Virus Bulletin conference on October 2nd, 2024, and in our white paper, which you can read in full here. The paper was also published on the Virus Bulletin website.
Key points of this blogpost:
- ESET Research shares updated findings on Telekopye, a scam toolkit designed to help cybercriminals defraud people on online marketplaces.
- While our previous research explored the technical and organizational background of Telekopye scams, our latest research describes the scammers’ various efforts to maximize their financial gains – expanding their victim pool, taking advantage of seasonal opportunities, and improving their tools and operations.
- Most notably, Telekopye groups have expanded their targeting to popular accommodation booking platforms, such as Booking.com and Airbnb.
- This new scam scenario comes with a targeting twist, utilizing compromised accounts of legitimate hotels and accommodation providers.
- These scams were especially prevalent in the summer holiday season in the targeted regions, surpassing Telekopye marketplace scams, according to ESET telemetry.
Telekopye overview
Telekopye is a toolkit that operates as a Telegram bot, primarily serving as a Swiss Army knife for turning online marketplace scams into an organized illicit business. It is used by dozens of scam groups, with up to thousands of members, to steal millions from Mammoths, as they call the targeted buyers and sellers. Neanderthals, as we call the scammers, require little to no technical knowledge – Telekopye takes care of everything in a matter of seconds.
Discovered by ESET Research in 2023, Telekopye has been in use since at least 2016, with victims all over the world. Multiple leads point to Russia as the country of origin of the bot’s author(s) and also the scammers using it. Telekopye is designed to target a large variety of online services in Europe and North America, such as OLX, Vinted, eBay, Wallapop, and others. At the time of writing, we have counted approximately 90 different services being targeted by the scams.
Neanderthals – members of any Telegram group utilizing Telekopye – gain access to the bot’s UI, which enables simple generation of phishing emails, SMS messages, web pages, and other features.
Telekopye groups have a business-like operation, with a clear hierarchy, defined roles, internal practices – including admission and mentoring processes for newcomers – fixed working hours, and commission payouts for Telekopye administrators. The Workers performing the scams must turn over any sensitive information stolen, and do not actually steal any money – that is managed by other roles in the organization. Each group keeps a transparent chat of all transactions, visible to all members.
Neanderthals utilize two main scenarios for targeting online marketplaces – one where they pose as sellers and another, much more common, where they pose as buyers. Both scenarios end with the victim/Mammoth entering payment card information or online banking credentials into a phishing web page mimicking a payment gateway.
Recently, Telekopye groups have expanded their targeting by adding support for scamming users of popular online platforms for booking accommodation, which we cover in the following section.
Branching out to accommodation booking platforms
In 2024, Telekopye groups have expanded their scamming playbook with schemes targeting users of popular online platforms for hotel and apartment reservations, such as Booking.com and Airbnb. They have also increased the sophistication of their victim selection and targeting.
Targeting with a twist
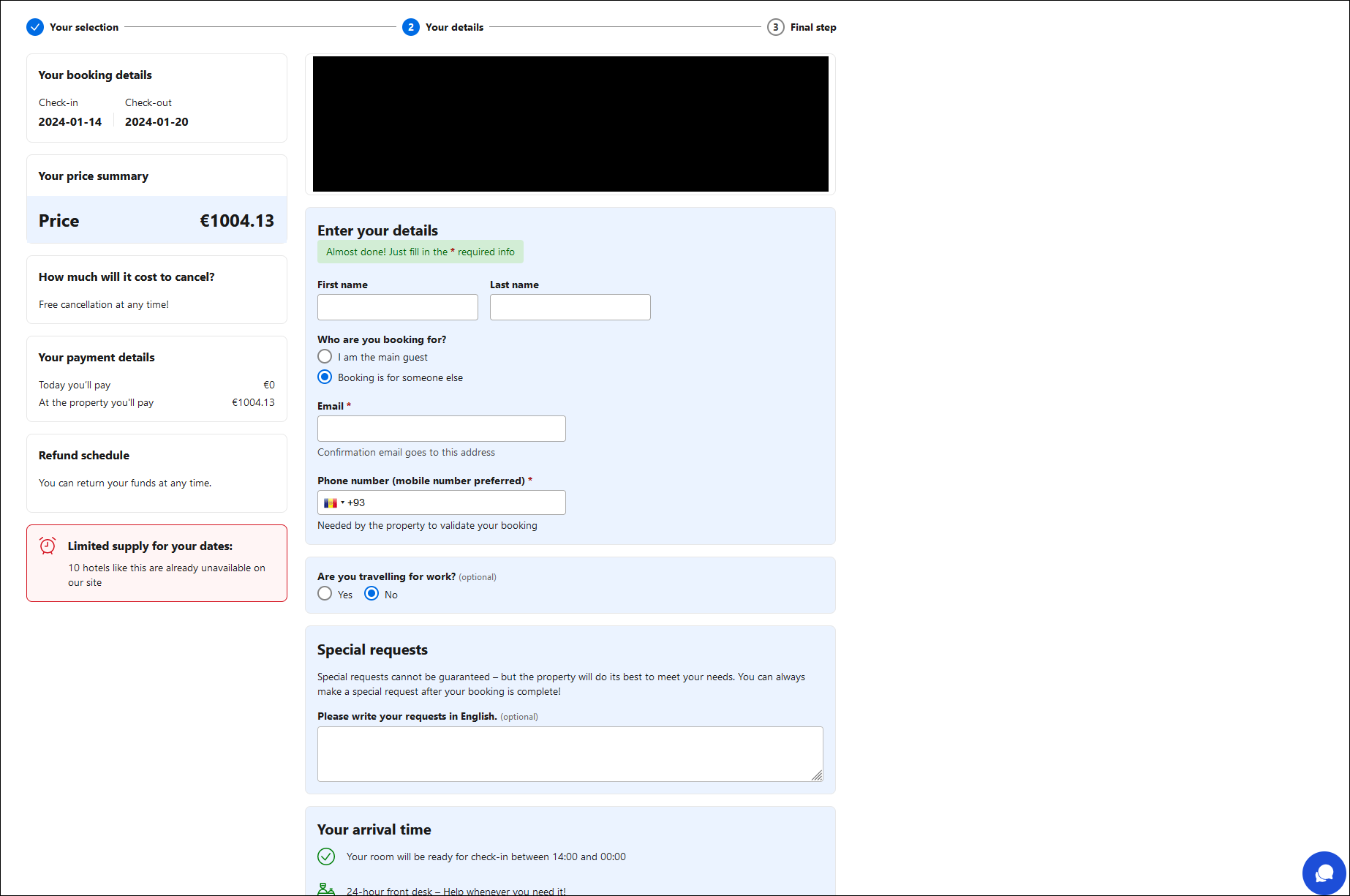
In this new scam scenario, Neanderthals contact a targeted user of one of these platforms, claiming that there is an issue with the user’s booking payment. The message contains a link to a well-crafted, legitimate-looking web page mimicking the abused platform.
The page contains prefilled information about a booking, such as the check-in and checkout dates, price, and location. This comes with a troubling twist: the info provided on the fraudulent pages matches real bookings made by the targeted users.
The Neanderthals achieve this by utilizing compromised accounts of legitimate hotels and accommodation providers on the platforms, which they most likely access via stolen credentials purchased on cybercriminal forums. Using their access to these accounts, scammers single out users who recently booked a stay and haven’t paid yet – or paid very recently – and contact them via in-platform chat. Depending on the platform and the Mammoth’s settings, this leads to the Mammoth receiving an email or SMS from the booking platform.
This makes the scam much harder to spot, as the information provided is personally relevant to the victims, arrives via the expected communication channel, and the linked, fake websites look as expected. The only visible sign of something being amiss are the websites’ URLs, which do not match those of the impersonated, legitimate websites. Neanderthals may also use their own email addresses for the initial communication (rather than the compromised accounts), in which case the emails might be more easily recognized as malicious.
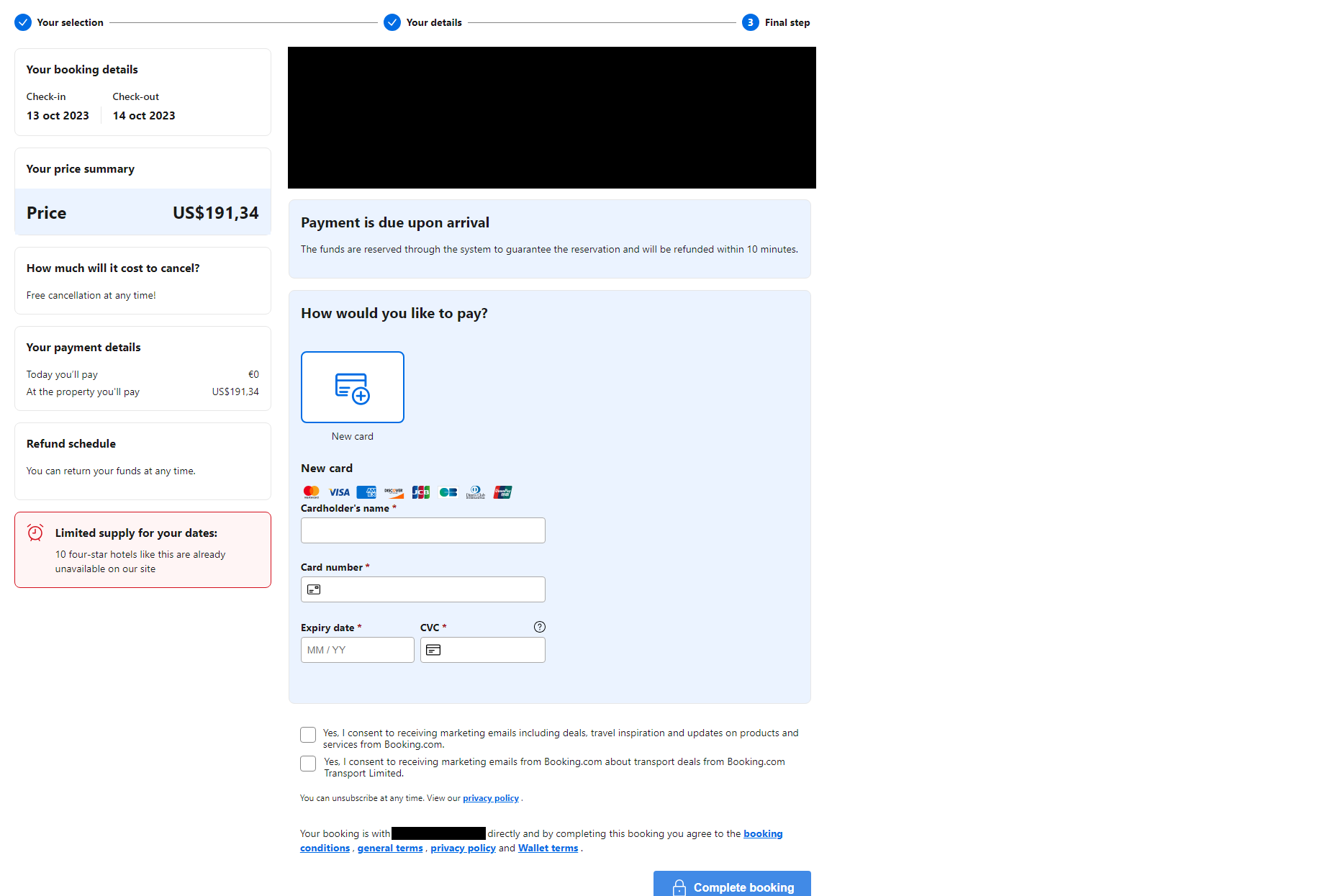
Once the target fills out the form on the phishing page (Figure 1), they are brought to the final step of the “booking” – a form requesting payment card information (Figure 2). As in the marketplace scams, card details entered into the form are harvested by the Neanderthals and used to steal money from the Mammoth’s card.
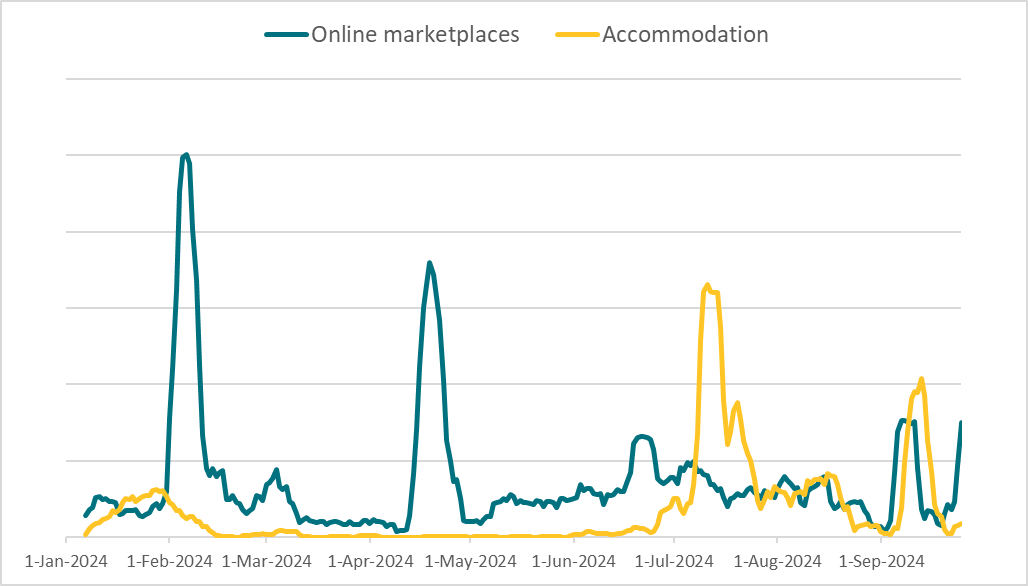
According to ESET telemetry, this type of scam started gaining traction in 2024. As seen in Figure 3, the accommodation-themed scams saw a sharp uptick in July, surpassing the original Telekopye marketplace scams for the first time, with more than double the detections during that month. In August and September, the detection levels for the two categories evened out.
As this increase coincides with the summer holiday season in the targeted regions – prime time for taking advantage of people booking stays – it remains to be seen whether this trend will continue. Looking at the overall 2024 data, we can see that these newer scams have amassed approximately half of the detection numbers of the marketplace variants. This is noteworthy considering that the newer scams focus on two platforms only, compared to the wide variety of online marketplaces targeted by Telekopye.
Advanced Telekopye features
Besides diversifying their target portfolio, Neanderthals have also improved their tools and operations to increase their financial returns.
Throughout our tracking of Telekopye, we’ve observed that different Telegram groups implement their own advanced features into the toolkit, aimed at speeding up the scam process, improving communication with targets, protecting phishing websites against disruption by competitors, and other goals.
Automated phishing page generation
To speed up the process of creating scam materials for posing as buyers on marketplaces, Neanderthals implemented web scrapers for popular targeted platforms. With these, only the URL to the product is required, instead of having to manually fill out a questionnaire about the targeted Mammoth and product in question. Telekopye parses the web page and extracts all necessary information automatically, providing a significant speedup for the scammers.
Interactive chatbot with on-the-fly translation
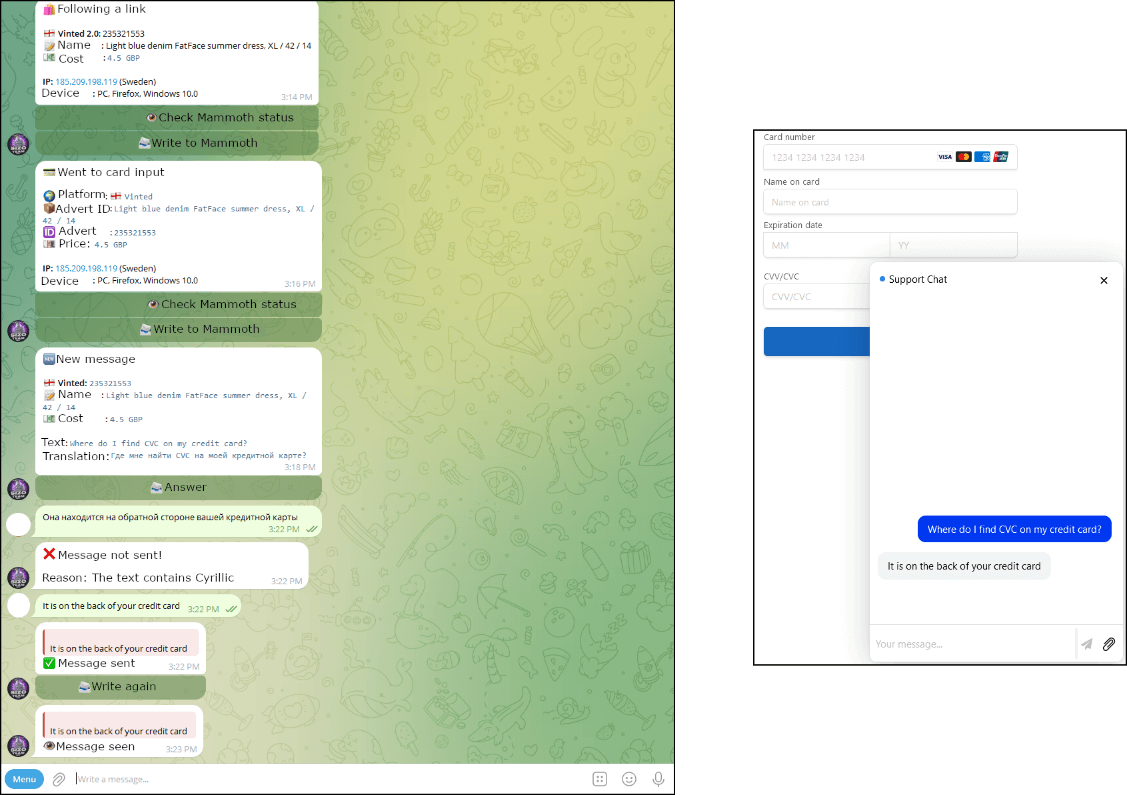
Neanderthals maintain a large collection of predefined answers to questions commonly asked by Mammoths. These are translated into various languages and kept as part of internal documentation, with the translations perfected over the years.
Neanderthals typically use these predefined phrases to try to direct the Mammoth to the phishing website, which comes with a chatbot in the lower right corner. Any message the Mammoth enters into the chat is forwarded to the Neanderthal’s Telegram chat, where it is automatically translated. Automatic translation of Neanderthals’ messages is not supported – Neanderthals translate their messages manually, usually using DeepL. Figure 3 shows how such an interaction looks from the Neanderthal’s and Mammoth’s points of view.
Anti-DDoS measures
The vast majority of the phishing websites are serviced by Cloudflare, relying on that service’s added protection, mainly against crawlers and automatic analysis. Interestingly, some of the Telekopye phishing websites also come with DDoS protection included. According to the Neanderthals’ knowledge base, which we obtained by infiltrating their ranks, this feature aims to protect against attacks by rival groups. These are sometimes launched as a means to disrupt a competitor’s operations for a short period.
Law enforcement operations
In late 2023, after ESET Research had published its two-part series on Telekopye, Czech and Ukrainian police arrested tens of cybercriminals utilizing Telekopye, including the key players, in two joint operations. Both operations were aimed against an unspecified number of Telekopye groups, which had accumulated at least €5 million (approximately US$5.5 million) since 2021, based on police estimates.
Besides the obvious success in disrupting such criminal activities, the arrests provided new insights into the groups’ workings, most notably recruitment and employment practices. The groups in question were managed, from dedicated workspaces, by middle-aged men from Eastern Europe and West and Central Asia. They recruited people in difficult life situations, through job portal postings promising “easy money”, as well as by targeting technically skilled foreign students at universities.
Some perpetrators confessed that they also participated in another scam group, similar to the Telekopye ones, that utilized call centers. The police learned that the recruits in that operation were often stripped of their passports and personal IDs to make quitting very difficult. Further, the managers sometimes went so far as to threaten the staff and their family members. This chilling development puts these operations into a completely different light.
Recommendations
The best way to stay protected against scams driven by Telekopye is being aware of Neanderthals’ tactics and exercising caution on the affected platforms. Besides knowing what red flags to pay attention to, we strongly recommend using a reputable antimalware solution on your device to step in if you do end up being lured to a phishing website.
Online marketplace scams
- Always verify the person you are talking with, mainly their history on the platform, age of their account, rating, and location – a location too far away, a fresh account with no history, or a bad rating might be indicators of a scammer.
- With the improvements in machine translation, messages from a scammer might not raise any red flags in terms of grammar. Rather than focusing on the language, focus on the conversation itself – overly eager or assertive communication should raise some concerns.
- Keep the communication on the platform, even if the person you’re talking to suggests otherwise. Their unwillingness to stay on the platform should be a major red flag.
- If you are a buyer, use secure interfaces within the platform throughout the whole buying process, whenever available. Otherwise, insist on in-person exchange of goods and money, or arrange for your choice of reliable delivery services with the option to pay on delivery.
- If you are a seller, use secure interfaces within the platform throughout the whole selling process, whenever available. Otherwise, manage delivery options yourself and don’t agree to those offered by the buyer.
- If you get to a point where you do visit a link sent by the person you are talking to, be sure to carefully check the URL, content, and certificate properties of the website before engaging with it.
Accommodation booking scams
- Before filling out any forms related to your booking, always make sure you haven’t left the official website or app of the platform in question. Being directed to an external URL to proceed with your booking and payment is an indicator of a possible scam.
- Because this scam uses compromised accounts of accommodation providers, contacting the providers directly is not a reliable way of verifying the legitimacy of payment requests. When in doubt, contact the official customer support of the platform (Booking.com, Airbnb) or report a security issue (Booking.com, Airbnb).
- To protect your account from compromise, whether you’re booking accommodation or renting one out, use a strong password and enable two-factor authentication wherever available.
Conclusion
Our research into Telekopye activities has given us unique insights into these scams: we were able to understand the technical means behind the scope of the operations, the business side of Telekopye groups, and even learn about Neanderthals themselves.
We have described the groups’ various efforts to maximize their financial gains, including expanding their victim pool, taking advantage of seasonal opportunities, and improving their tools and operations. Most notably, we have detailed the Neanderthals’ newest approach of targeting accommodation booking platforms, which also comes with more sophisticated targeting.
It is worth noting that we have communicated with several platforms targeted by Telekopye throughout our research; they are fully aware of these scams and confirmed they have employed several tactics to combat them. However, caution is still advised for users due to the number of the scams and their continuous evolution.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
| SHA-1 | Filename | Detection | Description |
| E815A879F7F30FB492D4 |
scam.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| 378699D285325E905375 |
scam.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| 242CE4AF01E24DB05407 |
123.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| 9D1EE6043A8B6D81C328 |
mell.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| B0189F20983A891D0B9B |
neddoss.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| E39A30AD22C327BBBD2B |
nscode.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| 285E0573EF667C6FB7AE |
tinkoff.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| N/A | 3-dsecurepay[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing domain. |
| N/A | approveine[.]com | Cloudflare, Inc. | 2024-06-28 | Telekopye phishing domain. |
| N/A | audittravelerbookdetails[.]com | Cloudflare, Inc. | 2024-06-01 | Telekopye phishing domain. |
| N/A | btsdostavka-uz[.]ru | TIMEWEB-RU | 2024-01-02 | Telekopye phishing domain. |
| N/A | burdchoureserdoc[.]com | Cloudflare, Inc. | 2024-05-31 | Telekopye phishing domain. |
| N/A | check-629807-id[.]top | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing domain. |
| N/A | contact-click2399[.]com | Cloudflare, Inc. | 2024-05-26 | Telekopye phishing domain. |
| N/A | contact-click7773[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing domain. |
| N/A | get3ds-safe[.]info | Cloudflare, Inc. | 2024-05-31 | Telekopye phishing domain. |
| N/A | hostelguest[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing domain. |
| N/A | order-9362[.]click | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing domain. |
| N/A | shiptakes[.]info | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing domain. |
| N/A | quickroombook[.]com | Cloudflare, Inc. | 2024-06-02 | Telekopye phishing domain. |
| N/A | validation-confi[.]info | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing domain. |
MITRE ATT&CK techniques
This table was built using version 15 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Reconnaissance | T1589 | Gather Victim Identity Information | Telekopye is used to gather payment card details, phone numbers, email addresses, etc. via phishing web pages. |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | Telekopye operators register their own domains. |
| T1585 | Establish Accounts | Telekopye operators establish accounts at online marketplaces. | |
| T1585.002 | Establish Accounts: Email Accounts | Telekopye operators set up email addresses associated with the domains they register. | |
| T1586.002 | Compromise Accounts: Email Accounts | Telekopye operators use compromised email accounts to increase their stealthiness. | |
| T1587.001 | Develop Capabilities: Malware | Telekopye is custom malware. | |
| T1588.002 | Obtain Capabilities: Tool | Telekopye operators use additional bots to launder money, scrape market research, and implement DDoS protection. | |
| Initial Access | T1566.002 | Phishing: Spearphishing Link | Telekopye sends email or SMS messages that contain links to phishing websites. |
| Collection | T1056.003 | Input Capture: Web Portal Capture | Web pages created by Telekopye capture sensitive information and report it to the operators. |

