Digital Security
Keep your cool, arm yourself with the right knowledge, and other tips for staying unshaken by fraudsters’ scare tactics
25 Sep 2024
•
,
5 min. read

We live in fast-paced and often worrying times, and fraudsters are primed to take advantage. Fear can be a powerful weapon and scammers know how to instill it in people and coerce them into taking specific and hasty actions. In cyberspace, one common way of doing so is via something called scareware.
Scareware is a classic bluff that trades on our anxieties about cybersecurity problems that might affect our devices and data. The scheme typically dupes victims into thinking they fell victim to what is popularly known as a “computer virus” (but is better called “malware”, anyway). The goal is to lead us down a path where those fears are ultimately realized. Fortunately, calm heads and forewarning are a potent defense.
What is scareware?
Has your computer or device screen ever been bombarded with pop-ups warning you about a malware compromise? Then you’ve probably encountered scareware. At its heart, it’s a scam where the victim is persuaded into believing their machine is infested with malware, and tricked into either paying for “AV software” they don’t need, handing over their personal/financial details, and/or installing real malware.
Scareware can be delivered several ways:
- Pop-ups: These open automatically when you click on a link, visit a web page or open a specific app. They might say your computer has been infected with dangerous malware that could cause it to crash at any moment. The only way to remediate the situation is to click on the pop-up to download a non-existent AV tool.
- Emails and social media messages: Unsolicited emails might try the same trick, persuading you to act fast to clean up a recent malware infection detected on your machine/device. These might even come from legitimate looking but spoofed email addresses. However, if you follow the link or click on the embedded button, it will lead you to a genuinely malicious site or download.
- Malvertising: Malicious ads on legitimate sites or social media platforms might do the same, urging the user to click through to download ‘AV software’ and remove the non-existent ‘malware’ on their computer or mobile device.
- Tech support calls: Sometimes the pop-ups or messages may have a tech support number to call which will take you to a fraud call center. The team there will be primed to spin you a line about your PC or device being compromised. They may ask you to download remote access software so they can ‘fix’ the problem. In reality, they’ll be looking to harvest your personal data and/or con you into paying for software that is little more than bloatware.
On other occasions, the tech support scammers might call out of the blue with a similar lie. These scams have been going for over a decade, and in 2023 were the third highest-grossing cybercrime type – netting fraudsters over $924 million, according to the FBI.
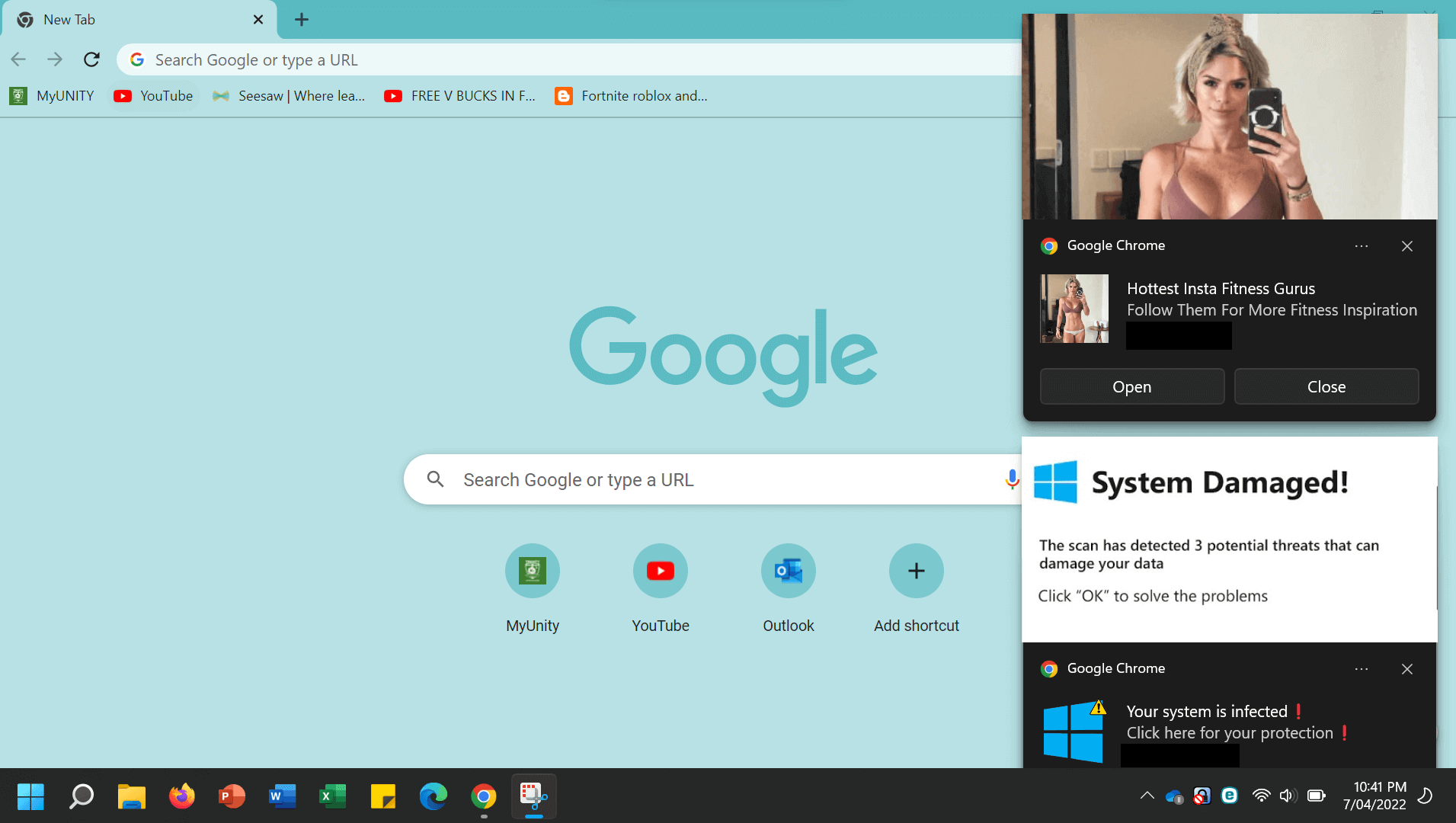
It’s all in the mind
Scareware works by using classic social engineering techniques of the sort we often observe in phishing messages. They try to rush the victim into making a decision they’ll regret by giving them no time to think. The warning is palpable and intended to create a sense of urgency: eg, “Take action NOW or your files and photos could be corrupted FOREVER.”
The scammers will enhance this urgency by showing flashing red images, text in caps and possibly even by showing fictitious screenshots of the supposed infected files. They might also display a progress bar of the machine being scanned.
Finally, social engineering relies on persuading the victim that the message itself comes from a legitimate source. So the fraudsters will do their best to mimic the branding and names of legitimate security vendors, using names such as “DriveCleaner,” “Antivirus360,” “PC Protector” and “Mac Defender.”
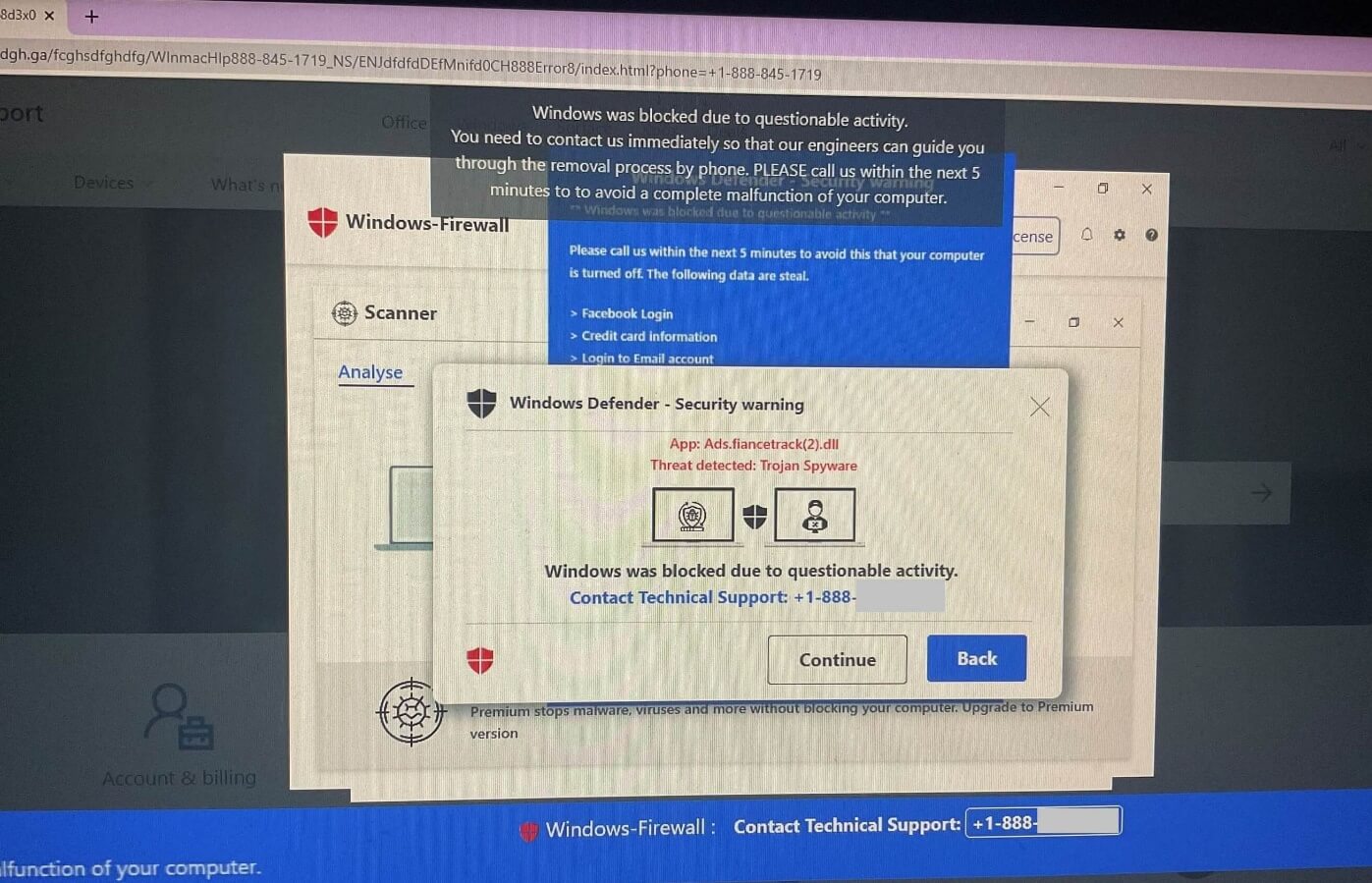
What could scareware do?
At best, you might spend money on useless bloatware. You don’t get anything in return but at least that’s where the scam ends. At worst, the bad guys also harvest your personal and financial details to use in follow-on identity fraud. Or, by clicking through on the link or ad, you unwittingly install malware designed to steal your information or lock your computer with ransomware—in which case you’ll be forced to pay a charge in order to have it unlocked (which may or may not work).
How to stay clear of scareware
The good news is that it isn’t hard to stay safe from scareware. Here are some best practices to bear in mind once you spot an “alert”:
- Don’t let fear get the better of you and never click on the pop-up. If you don’t recognize the name of the “AV tool”, research its name through a trusted source like Google to verify its legitimacy.
- Close your web browser down and/or disconnect from the internet, rather than click on the alert. On Windows, the former can be done by pressing Control-Alt-Delete, choosing Task Manager and killing the browser task. On a Mac, hit Command-Option-Escape to open the Force Quit window. Alternatively, simply turn the device off. Either way, avoid clicking on the fake “X” or “Close” button on the pop-up as this could actually install malware instead of closing the window.
- Use reputable pop-up/ad blockers to reduce the chances of scareware appearing on your screen in the first place. Many of these blockers will stop malicious pop-ups before they reach you.
- Keep your browsers and computer software updated and on the latest and most secure version. Older versions of your favorite programs are more susceptible to being exploited by bad actors.
- Install legitimate security software from a trusted provider to block scareware from your devices. Remember to keep these tools up to date with the latest version.
- Educate yourself on what the legitimate alerts of your security software of choice look like so you can easily distinguish them from those coming from scareware.
- Remember that legitimate security software vendors won’t flood your screen with a flurry of pop-ups warning you about malware.
How to remove scareware
If your computer or mobile device does get compromised with scareware, removing it shouldn’t be too much of a challenge. Remember, it’s not real malware. Simply run your legitimate security tool to scan for it manually, and follow the prompts for removal.
Failing that, you could look for the scareware manually. On Windows 10: Search for “add or remove programs” and uninstall from the list that comes up. On Macs, find the scareware program in the Applications category of the Finder window. Right-click and drag it to the Trash, then empty Trash. You should also change the passwords to any email and financial services accounts. Stay calm, and don’t be scared.
