Read more about the international crackdown on spyware
US Moves to Ban “Anti-Democratic” Spyware
US Cracks Down on Spyware with Visa Restrictions
Governments and Tech Giants Unite Against Commercial Spyware
Global scrutiny on hack-for-hire services and spyware tools has heightened over the past few months, with many countries strengthening their legal response to human rights and security violations leveraging these tools and services.
However, while the most infamous spyware products, like NSO Group’s Pegasus and Intellexa’s Predator, are now non-grata in several jurisdictions, many others still thrive.
According to a September 4 report by the Atlantic Council’s Cyber Statecraft Initiative and researchers at American University, spyware vendors’ ability to evade sanctions is in part due to a complex network of interrelated entities based in various locations and dependent on different jurisdictions.
Read more: NSO Group’s Recent Difficulties Could Shape the Future of the Spyware Industry
Purposefully Confusing Spyware Landscape
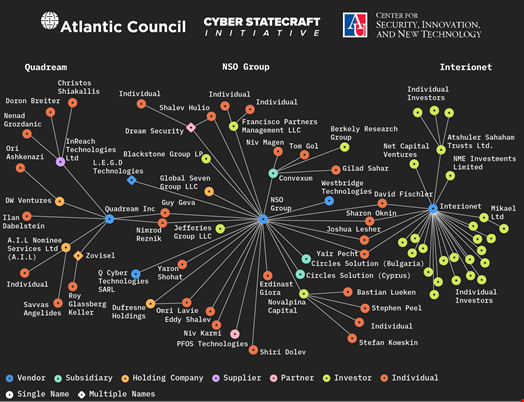
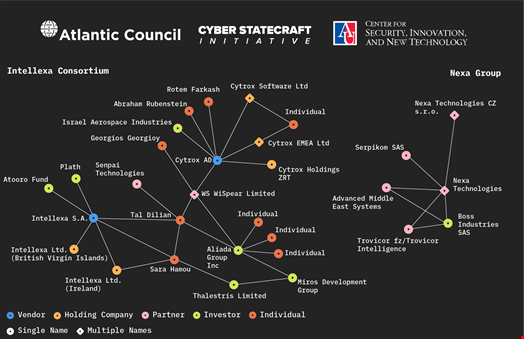
After an investigation led between 2019 and 2023, the think tank’s Digital Response Forensics Laboratory (DFRLab) found a staggering 435 entities across 42 countries involved in spyware development.
This “detailed but even still incomplete sample” includes 49 vendors along with 36 subsidiaries, 24 partner firms, 20 suppliers and a mix of 32 holding companies, 95 investors and 179 individuals, including many named investors. Many times, the relationships between these entities are not made public and they regularly change names, making it harder to track.
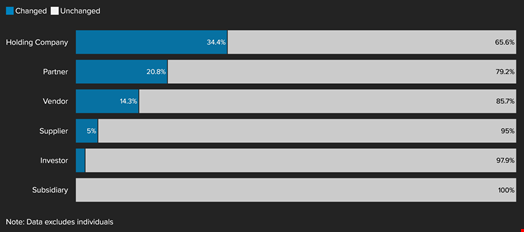
“This market is a significant vector for facilitating the human rights harms and national security risks posed more broadly by spyware,” noted the report.
While countries like the US and the UK have started cracking down on some of the vendors, many sanctions, including export regulations “are reliant on self-reporting,” Trey Herr, senior director of the Cyber Statecraft Initiative, told The Washington Post.
“We have got to get the policy side cooperating internationally, or this market is going to expand out of control,” he added.
Primary Trends in the Spyware Landscape
Upon analyzing the DRFLab-collected dataset, the Cyber Statecraft Initiative researchers found four primary trends that characterize the spyware ecosystem:
- Concentration of entities in three major jurisdictions: Israel, Italy and India
- Serial entrepreneurship across multiple vendors
- Partnerships between spyware and hardware surveillance vendors
- Regularly shifting vendor identities
- Strategic jurisdiction hopping
- Cross-border capital flows fueling this market
Atlantic Council’s Anti-Spyware Policy Recommendations
From these trends, the researchers provided a set of policy recommendations to “produce greater transparency across the market, limit the jurisdictional arbitrage of vendors seeking to evade limits on their behavior and more effectively scrutinize supplier and investor relationships.”
These include:
- Mandating “know your vendor” requirements: the Atlantic Council recommended that the US and its partners require spyware vendors to disclose supplier and investor relationships
- Improving government-run corporate registries: the researchers urged for government-run corporate registries to be more detailed, openly accessible to the public and use systematically verified data
- Enriching, auditing and publishing export licenses to collect records of key spyware vendors personnel and activities
- Limiting jurisdictional arbitrage by spyware vendors: the think tank recommended that governments require vendors to self-report violations, make it harder for spyware vendors to exit a jurisdiction and implement automatic review after transactions impacting ownership
- Providing greater protection against Strategic Lawsuits Against Public Participation (SLAPP): the Atlantic Council advised governments to encourage open reporting and restrict the ability of spyware vendors to sue researchers, journalists and activists who report violations
Infrastructure of Predator Spyware Resurfaces
One day after the Atlantic Council published the report, cybersecurity firm Recorded Future shared new findings showing evidence of Intellexa’s Predator spyware resurgence.
While the spyware’s activity had declined following sanctions, a September 5 report by Insikt Group, Recorded Future’s threat intelligence arm, showed that the infrastructure that Predator relies on has recently reappeared.
“The new infrastructure includes an additional tier in its multi-tiered delivery system, which anonymizes customer operations, making it even harder to identify which countries are using the spyware. This change makes it more difficult for researchers and cybersecurity defenders to track the spread of Predator,” noted the Insikt Group researchers.
Read more: Spyware: A Threat to Civil Society and a Threat to Business
Conclusion
The Atlantic Council’s report sheds light on the intricate web of entities involved in the spyware industry, highlighting the challenges in regulating and preventing the misuse of these powerful tools.
The resurgence of Predator spyware infrastructure, despite sanctions, underscores the need for continued vigilance and international cooperation to combat the proliferation of spyware and protect human rights and national security.
Read more: How to Mitigate Spyware Risks and Secure Your Business Secrets
