ESET Research, Threat Reports
An overview of the activities of selected APT groups investigated and analyzed by ESET Research in Q4 2023 and Q1 2024
14 May 2024
•
,
2 min. read

ESET APT Activity Report Q4 2023–Q1 2024 summarizes notable activities of selected advanced persistent threat (APT) groups that were documented by ESET researchers from October 2023 until the end of March 2024. The highlighted operations are representative of the broader landscape of threats we investigated during this period, illustrating the key trends and developments, and contain only a fraction of the cybersecurity intelligence data provided to customers of ESET’s private APT reports.
In the monitored timeframe, several China-aligned threat actors exploited vulnerabilities in public-facing appliances, such as VPNs and firewalls, and software, such as Confluence and Microsoft Exchange Server, for initial access to targets in multiple verticals. Based on the data leak from I-SOON (Anxun), we can confirm that this Chinese contractor is indeed engaged in cyberespionage. We track a part of the company’s activities under the FishMonger group. In this report, we also introduce a new China-aligned APT group, CeranaKeeper, distinguished by unique traits yet possibly sharing a digital quartermaster with the Mustang Panda group.
Following the Hamas-led attack on Israel in October 2023, we detected a significant increase in activity from Iran-aligned threat groups. Specifically, MuddyWater and Agrius transitioned from their previous focus on cyberespionage and ransomware, respectively, to more aggressive strategies involving access brokering and impact attacks. Meanwhile, OilRig and Ballistic Bobcat activities saw a downturn, suggesting a strategic shift toward more noticeable, “louder” operations aimed at Israel. North Korea-aligned groups continued to target aerospace and defense companies, and the cryptocurrency industry, improving their tradecraft by conducting supply-chain attacks, developing trojanized software installers and new malware strains, and exploiting software vulnerabilities.
Russia-aligned groups have focused their activities on espionage within the European Union and attacks on Ukraine. Furthermore, the Operation Texonto campaign, a disinformation and psychological operation (PSYOP) uncovered by ESET researchers, has been spreading false information about Russian-election-related protests and the situation in Ukrainian Kharkiv, fostering uncertainty among Ukrainians domestically and abroad.
Additionally, we spotlight a campaign in the Middle East carried out by SturgeonPhisher, a group we believe to be aligned with the interests of Kazakhstan. We also discuss a watering-hole attack on a regional news website about Gilgit-Baltistan, a disputed region administered by Pakistan, and lastly, we describe the exploitation of a zero-day vulnerability in Roundcube by Winter Vivern, a group we assess to be aligned with the interests of Belarus.
Malicious activities described in ESET APT Activity Report Q4 2023–Q1 2024 are detected by ESET products; shared intelligence is based mostly on proprietary ESET telemetry data and has been verified by ESET researchers.
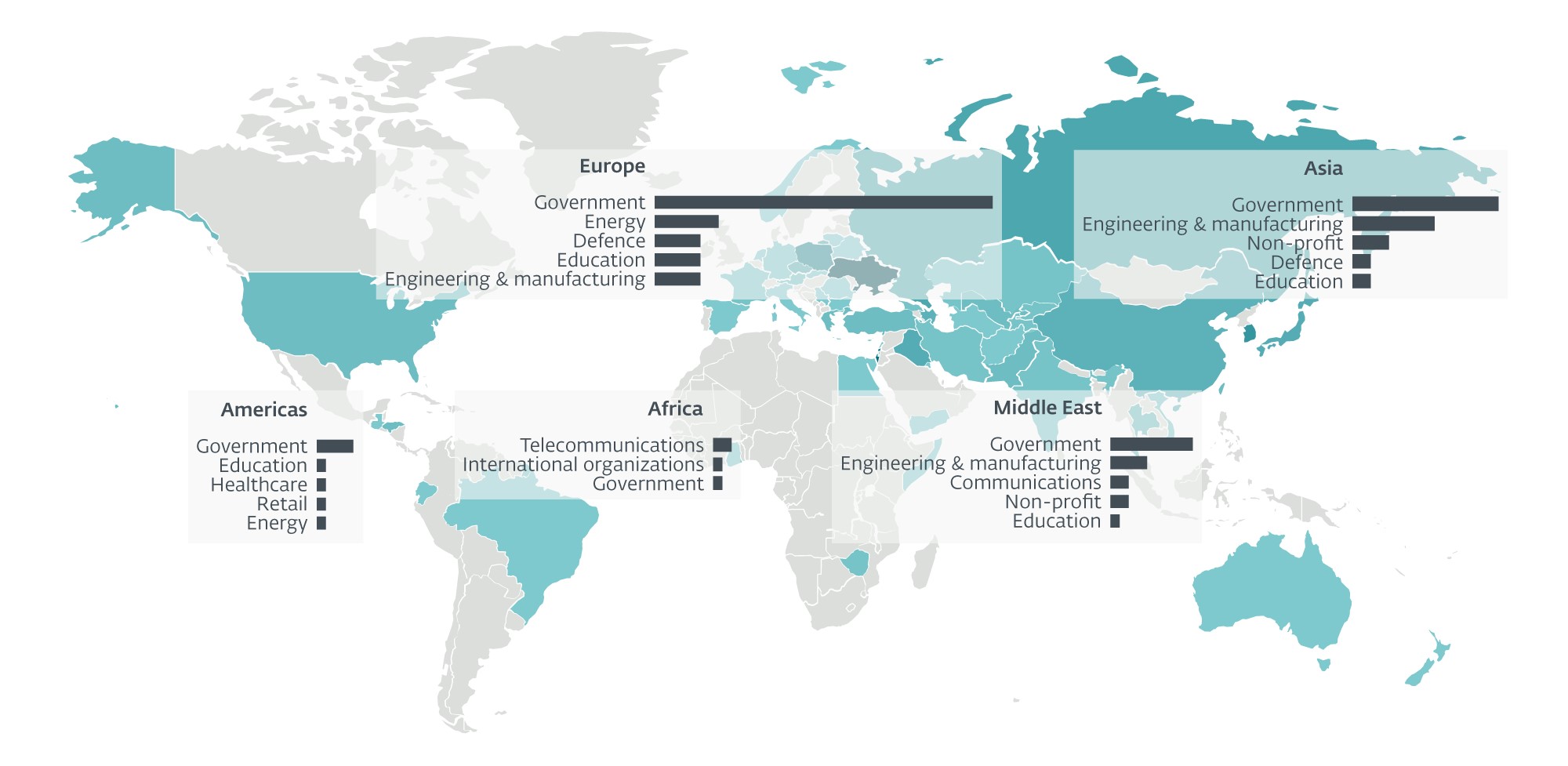
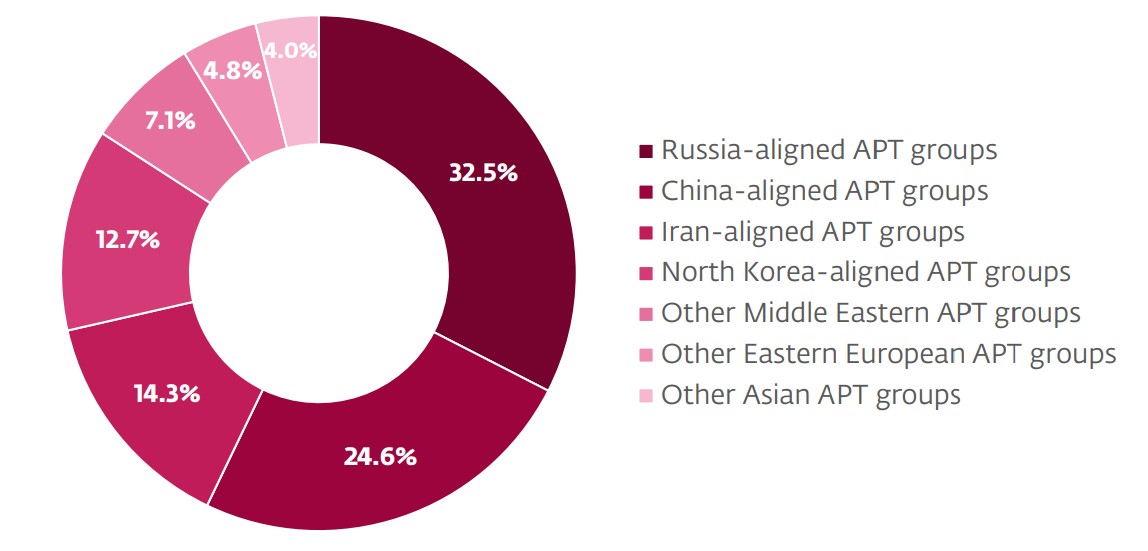
ESET APT Activity Reports contain only a fraction of the cybersecurity intelligence data provided in ESET APT Reports PREMIUM. For more information, visit the ESET Threat Intelligence website.
Follow ESET research on X for regular updates on key trends and top threats.

