Scams
Here’s how cybercriminals target cryptocurrencies and how you can keep your bitcoin or other crypto safe
15 Apr 2024
•
,
6 min. read

Bitcoin is on a tear. The world’s largest digital currency by market cap passed its previous record value of nearly $69,000 in early March. It’s now worth an estimated $1.3 trillion. Yet the fluctuating value of cryptocurrency doesn’t necessarily correspond to the level of cybercrime activity we can observe. In fact, crypto-threats have been thriving for years.
Right now, the world of crypto is bracing itself for a bitcoin halving due later this month. These events attract not only significant media attention and public interest in cryptocurrencies, but also attract malicious actors seeking to exploit the hype surrounding them to launch phishing scams or fraudulent investment schemes targeting unsuspecting individuals.
Let’s look at what you need to know and do to keep your digital currency safe.
Cryptocurrency risk take various forms
Owning crypto can be attractive to many, for its (pseudo)anonymity, low transaction costs, and as an alternative investment option. But the crypto space is also something of an unregulated Wild West. Threat actors are primed and ready to ruthlessly exploit any users lacking digital savvy – via scams and sophisticated malware. In some cases, they might bypass you altogether and go after crypto-exchanges and other third parties.
We can divide the main threats into three types: malware, scams and third-party breaches.
1. Malware and malicious apps
Detections of malware specifically designed to steal cryptocurrency from users’ wallets (cryptostealers) surged 68% from H1 to H2 2023, according to the latest ESET Threat Report. One of the most popular is Lumma Stealer, aka LummaC2 Stealer, which targets digital wallets, user credentials and even two-factor authentication (2FA) browser extensions. It also exfiltrates information from compromised machines. Detections of this particular cryptostealer – delivered as a service to cybercriminals – tripled between H1 and H2 2023.
Other crypto-stealing malware threats include:
- Crypto drainers: a malware type designed to identify the value of assets in your wallet(s), use malicious smart contracts to siphon off funds quickly, and then use mixers or multiple transfers to hide its tracks. One variant, MS Drainer, stole an estimated $59m over a nine-month period
- Common info-stealers like RedLine Stealer, Agent Tesla, and Racoon Stealer all have cryptostealing capabilities
- ClipBanker Trojans – another type of general info-stealer – also exfiltrate cryptocurrency wallet account addresses
- Crypto-stealing malware is often found hidden in fake apps. Recently, for example, ESET researchers found dozens of ClipBanker malware variants in trojanized WhatsApp and Telegram apps designed to lift crypto wallet addresses sent by users in their chat messages
- Botnet malware such as Amadey, DanaBot and LaplasBanker can also contain functionality to steal crypto-wallet information
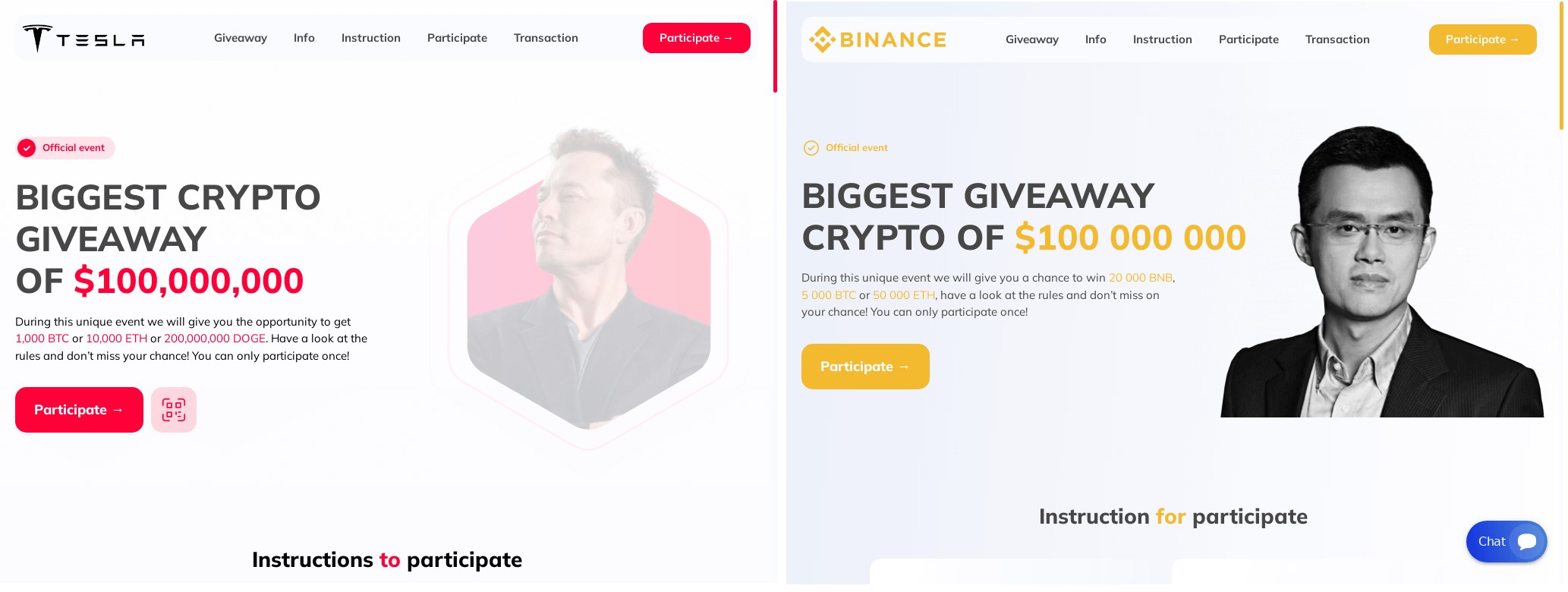
2. Scams and social engineering
Sometimes the bad guys dispense with malware altogether, and/or combine it with carefully crafted attacks designed to capitalize on our credulity. Watch out for the following common scams targeting cryptocurrency:
- Phishing techniques are frequently used to lure victims into clicking on malicious links designed to steal crypto-wallet information/funds. In the case of crypto drainers, the first contact is often ads on spoofed social media accounts faked to look like legitimate high-profile accounts. Users are then directed to a phishing website spoofed to look like a genuine token distribution platform, and then asked to connect their wallets to the site. The victim will then be presented with a (malicious) transaction to sign, which will automatically drain their wallet of funds. Victims lost $47m in February from this kind of scam.
- Celebrity impersonation is a common trick for scammers. They’ll create a spoof social media account and impersonate popular figures like Elon Musk to launch bogus crypto giveaways or publicize fake investment opportunities. These accounts will contain malicious links and/or request outright crypto deposits from victims.
- Romance fraud made scammers over $652m last year, according to the FBI. Fraudsters build up a rapport with their victims on dating sites and then invent a story, asking them for funds – possibly via hard-to-trace crypto.
- Investment scams are the highest-grossing cybercrime type of all, making the bad guys over $4.5bn in 2023, according to the FBI. Unsolicited emails or social media ads lure victims with the promise of big returns on their crypto investments. They’ll usually link to a legitimate-looking investment app or website. However, it’s all fake, and your money will never be invested.
- Pig butchering is a combination of romance and investment fraud. Victims are lured into a false sense of security by scammers they meet on dating sites, who then try to persuade them to invest in fictitious crypto schemes. Some may even pretend the user is making money on their ‘investment’ – until they try and withdraw funds. The US Department of Justice seized over $112m from pig butchering operators in one swoop last year.
- Pump-and-dump schemes work when scammers invest in and then heavily promote a token/stock in order to drive up the price, before selling at a profit and leaving genuine investors with near-worthless assets. Market manipulators of this sort may have made over $240m last year by artificially inflating the value of Ethereum tokens.

3. Third-party hacks
Think your crypto is safe in an exchange or other legitimate third-party organization? Think again. Cybercrime groups and even nation states are targeting such entities with increasing frequency and success. North Korean hackers are estimated by the UN to have stolen at least $3bn in crypto since 2017, including $750m last year alone. A lack of regulatory oversight means it’s difficult to hold crypto exchanges accountable in the event of a serious breach, while the decentralized nature of digital currency makes recovering funds challenging.
It’s not just exchanges that could be targeted. Credentials stolen from password manager firm LastPass in 2022 may have been used to steal as much as $35m from security-conscious customers.
Crypto defense 101
Fortunately, best practice security rules still apply in the crypto world. Consider the following to keep your virtual assets under lock and key.
- Only download apps from official app stores and never download pirated software
- Ensure your device is loaded with anti-malware software from as trusted provider
- Use a password manager for long, unique passwords on all accounts
- Use 2FA for your wallet and device
- Be skeptical: don’t click on links in unsolicited attachments or on social media ads/posts – even if they appear to be from legitimate sources
- Store your crypto in a “cold wallet” (that is, one not connected to the internet) such as Trezor, as this will insulate it from online threats
- Always do your research before making any crypto investments
- Always keep devices and software updated
- Avoid logging on to public Wi-Fi without a virtual private network (VPN)
- Never send strangers crypto – even if you’ve ‘met’ them online
- Before choosing an exchange, do some research to check their security credentials
- Separate your crypto trading from your personal and work devices and accounts. That means using a dedicated email address for your wallet
- Don’t brag online about the size of your crypto wallet/portfolio
Obviously cybercriminals have taken notice of the widespread fascination with cryptocurrencies and their staggering rise in value. After all, they tend to gravitate towards opportunities where significant financial gains are involved. Therefore, it’s crucial for you to stay sharp and take other precautions to make sure your crypto stays out of the clutches of cybercriminals.

