Read more about LockBit Ransomware:
LockBit Takedown: What You Need to Know about Operation Cronos
LockBit Infrastructure Disrupted by Global Law Enforcers
LockBit and Royal Mail Ransomware Negotiation Leaked
LockBit Remains Top Global Ransomware Threat
“We know who he is. We know where he lives. We know how much he is worth. LockbitSupp has engaged with law enforcement.”
This message was released on LockBit ransomware group’s former data leak site at 12pm GMT on February 23.
However, for the 30,000 curious people who visited the page this was not the news they had anticipated.
They were expecting law enforcement agencies behind Operation Cronos, which took down LockBit’s infrastructure on February 19, to reveal the identity of the group’s kingpin, known on the dark web by the moniker LockbitSupp.
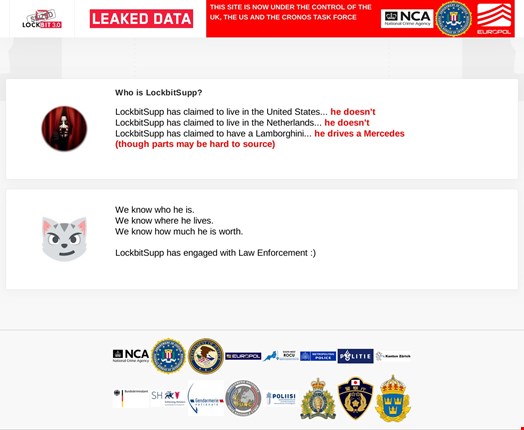
However, the message taught us that law enforcement agents do know who the individual behind the LockbitSupp persona is and are talking with him.
Additionally, the law enforcement message unveiled some revelations about the individual, namely that many of his previous claims relating to location and the vehicle he drives are false (see above).
These LockbitSupp claims were cited by Jon DiMaggio, chief security strategist at Analyst1, in his Ransomware Diaries series, for which he maintained frequent contacts with LockbitSupp and some of LockBit’s affiliates.
DiMaggio found inconsistencies across different interactions with LockbitSupp and assessed that three other individuals, including the group’s current leader, had run the persona.
LockBit’s Origins
LockBit is a notorious ransomware variant and, at times, has been the most deployed worldwide, indiscriminately targeting organizations from all industry verticals.
Here’s a graphic from our upcoming Active Adversary Report , showing precisely how, as seen by the Sophos X-Ops Incident Response team, Conti in 2021 and LockBit in 2023 represented literally double the volume of infections of the nearest “competitors .” 2/11 pic.twitter.com/LDFv5qJ0i3
— Sophos X-Ops (@SophosXOps) February 21, 2024
The group emerged in 2019 and the LockBit named ransomware was first seen on a Russian-language based cybercrime forums in January 2020 and it listed its first victim to its leak site in September 2020.
Because of its links with Russian-language forums, many security analysts believe the gang was based in, or at least heavily connected with, Russia.
As part of Operation Cronos, the US imposed sanctions on the group’s affiliates responsible for ransomware attacks, including two Russian nationals. One, Ivan Gennadievich Kondratiev, was commonly known in the cybercriminal world as “Bassterlord” and “Fisheye.”
The group operates a ransomware-as-a-service (RaaS) model, with a network of affiliates that leverage LockBit’s malware to conduct cyber-attacks.
Following Operation Cronos, the UK’s National Crime Agency (NCA) said it gained a wealth of data on the group’s affiliates, revealing 187 distinct entities.
This number could be higher or lower as some affiliates might use several accounts and others might have been inactive or only active for a short period of time.
The US government offers a $15m bounty for anyone providing critical information on the group and its administrators.
LockBit’s Tactics and Operations
LockBit ransomware has evolved since its inception in 2019. Security experts believe the group has been running the following ransomware versions:
- LockBit 1.0 was released in January 2020 as “ABCD” ransomware
- LockBit 2.0 (LockBit Red) was released in June 2021 together with StealBit, the group’s data exfiltration tool
- LockBit Linux was released in October 2021 to infect Linux and VMWare ESXi systems
- LockBit 3.0 (LockBit Black) was released in March 2022 and leaked six months later by the group’s disgruntled developer, leading to disruptions within the RaaS structure
- LockBit Green was released in January 2023 and promoted by LockbitSupp as being a major new version – a fact that was later denied by many security professionals, who found it was a rebranded version of a Conti encryptor
The newest ‘real’ version of the ransomware, LockBit 3.0, aimed to be a more modular and evasive than previous versions.
LockBit 3.0 proved challenging for security analysts and automated defense systems due to its encrypted executables, random passwords and undocumented Windows functions.
Overall, LockBit kept its offering simple with a point-and-click interface, which would appeal to a wide range of affiliates with varying degrees of technical knowledge.
Typical tactics included double extortion, where data from a victim organization would be encrypted and stolen.
However, because of LockBit’s affiliate operating model the tactics, techniques and procedures (TTPs) of the ransomware gang have varied widely.
A cybersecurity advisory by the US Cybersecurity and Infrastructure Security Agency published in June 2023 details the technical information behind LockBits operations.
Interestingly, the RaaS gang also engaged in publicity-generating activities and stunts, such as paying people to get LockBit tattoos, which, since Operation Cronos, has become a viral meme in the cybersecurity world.
How LockBit Leveraged Cryptocurrency
Law enforcement agencies behind Operation Cronos partnered with cryptocurrency transaction analysis firm Chainalysis to understand the groups finances.
They found 30,000 Bitcoin addresses linked to LockBit, with over 500 Bitcoin addresses active, which have received over $120m. The analysis also shows over $114m remains unspent.

It is likely that the LockBit ransomware group is responsible for multi-billion dollars’ worth of theft internationally.
LockBit has Hacked Hundreds of Victim Organizations
LockBit used its leak site to publish the details of its victims and the ransom demands associated with the hack. The vast number of organizations the group hacked made it the most notorious ransomware gang of 2023. LockBit listed 275 victims on data leak sites between October and December 2023.
In a webinar broadcast on February 21, Recorded Future estimated the total number of LockBit victims was 2300, with around 57% based in the US.
“This estimate is based on our data; the reality is likely much higher,” said Alexander Leslie, a threat intelligence analyst at Recorded Future.
High-profile victims include the UK’s Royal Mail, from which LockBit demanded a £66m ransom.
The LockBit hacking group also claimed responsibility for a cyber-attack against the multinational automotive group Continental in November 2022.
Affiliates of the group also targeted Toronto’s Hospital for Sick Children (SickKids) on the evening of December 18, 2022. This attack supposedly contravened the group’s policy on targets and a decryption key was handed over free of charge.
The Housing Authority of the City of Los Angeles (HACLA) issued a public notice outlining the impact of a ransomware breach that took place in early 2023. The suspected culprits were LockBit.
Is There a Decryptor for LockBit?
Yes. As part of the February 19 Operation Cronos, law enforcement confirmed they have access to around 1000 of LockBit’s decryption keys.
This has allowed the law enforcement organizations involved in Operation Cronos to develop new decryption tools designed to recover files encrypted by the LockBit ransomware.
“Law enforcement may be able to assist you to decrypt your LockBit encrypted files,” reads a message displayed on LockBit’s data leak site.
In a public statement, the US Department of Justice (DoJ) commented: “Beginning today, victims targeted by this malware are encouraged to contact the FBI at https://lockbitvictims.ic3.gov/ to enable law enforcement to determine whether affected systems can be successfully decrypted.”
These solutions have also been made available for free on the ‘No More Ransom’ portal, available in 37 languages.
It is Probably the End of LockBit…As We Know It
Many cybersecurity experts believe that, despite Operation Cronos’ success, individuals behind LockBit will come back in one form or another if they are not all arrested.
Some think they will develop another toolset, while others believe they will reorganize under a new name, just like Conti members have done before them.
However, Yelisey Bohuslavskiy, co-founder of threat intelligence firm RedSense, believes this is the end of LockBit as we know it.
In a three-year investigation conducted by RedSense, researchers observed that LockBit was functioning in a three-layered structure:
- Surface Level: LockBit is a large and established RaaS comprised of dozens of affiliates, which chaotically attack random networks in a “spray and pray” fashion and fail around 99% of the time
- LockbitSupp Level: LockBit is relying on a low-capability core group, with fake claims, constant affiliate scams and LockbitSupp serving as a mere distraction for actual operations
- Big Game Level: “Ghost groups” – i.e., groups of skilled affiliates with high capabilities but who transfer them to another brand
“The ‘Ghost Group’ model is something between a corporate ransomware structure like Conti and a classic RaaS like Maze,” said the RedSense report.
One of LockBit’s most reliable ‘Ghost groups’ was named Zeon and it was comprised of former Conti hackers. The same members were also previously involved with the Ryuk ransomware group, Zeon has also outsourced its skills to the Akira ransomware group.
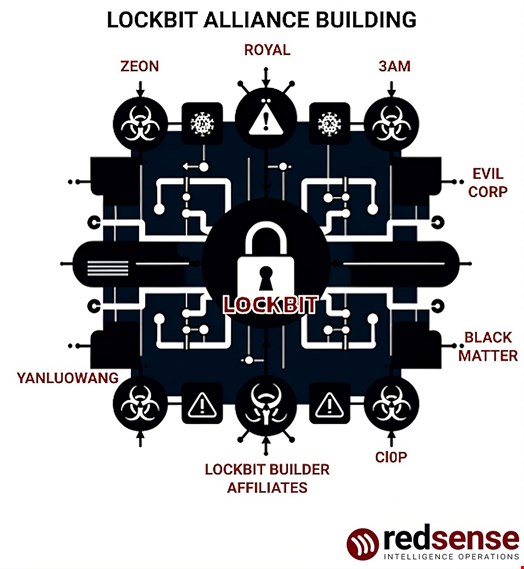
According to RedSense, LockBit was heavily reliant on the high-tier professionals like Zeon. It is assumed that they will grow tired of the amateurism of the LockBit admins and will move on. They could perhaps have more substantial involvement with Akira or BlackSuit, a rebrand of the Royal ransomware group.
Some of the RedSense findings, namely that an ex-Conti member was involved in LockBit’s high-end operations, correlate with a report published by another threat intelligence firm, Prodaft, on February 22.
Prodaft took part in Operation Cronos.
During its LockBit takedown webinar, Recorded Future estimated three possible scenarios for the future of LockBit:
- The ‘Retire’ scenario, in which the LockBit core operational group would cease to get involved in illegal cyber activities
- The ‘Return’ scenario, in which LockBit admins would build new infrastructure and try to develop a new version of their toolset, similar to what the REvil ransomware group has done in the past
- The ‘Little LockBits’ scenario, in which LockBit members would join other existing ransomware groups or form new ones, just like Conti members did
Recorded Future’s Leslie and his colleagues Allan Liska and Dmitry Smilyanets said they believe the last scenario to be the most likely.
However, Japanese cybersecurity firm Trend Micro, which also took part in Operation Cronos, released a report on February 22 showing that the LockBit group was already trying to develop a new ransomware version.
Conclusion
Operation Cronos and the law enforcement takedown of the LockBit ransomware gang has been hailed as a success for the cybersecurity world.
LockBit ransomware has indeed been one of the most prolific and destructive means of cyber-attack globally.
While the future remains uncertain for members of the gang, and many in the cybersecurity community are hoping for more arrests, it is clear that this sophisticated network of cybercriminals has been stopped in their tracks. For now.
