Operation Cronos, the global law enforcement operation that took down LockBit, one of the world’s most harmful ransomware groups, is a major breakthrough in the fight against cybercrime.
The operation, announced on February 20, was led by the UK’s National Crime Agency (NCA) and the FBI.
Key Takeaways from the Biggest Ransomware Takedown
The results of the operation were unprecedented: on top of seizing LockBit’s data leak site and affiliate panel, law enforcement agencies seized 34 servers operated by LockBit, closed 14,000 “rogue accounts” involved with data exfiltration or the group’s infrastructure” and froze 200 cryptocurrency accounts linked to LockBit and its affiliates.
LockBit’s bespoke data exfiltration tool, known as Stealbit, was also seized.

Security researchers Vx-underground also claimed that at least 22 Tor sites associated with LockBit had been seized and/or taken down by law enforcement.
In addition, two LockBit actors have been arrested in Poland and Ukraine at the request of the French judicial authorities.
Three international arrest warrants and five indictments have also been issued by the French and US judicial authorities.
Some of the key elements of the operation were displayed on the LockBit data leak site homepage, in a display mimicking how the ransomware group would announce new victims.

Operation Cronos was the result of a task force involving Europol and law enforcement agencies in the UK, the US, and eight other countries, as well as additional support from police forces and national agencies in four other countries.
This makes it one of history’s most significant law enforcement operations against cybercrime.
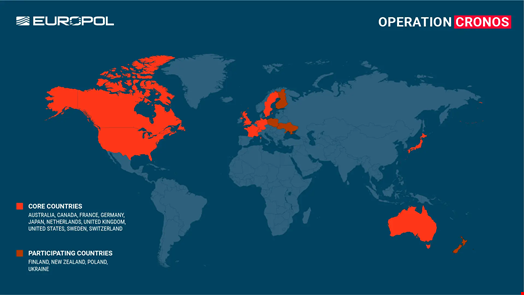
The private sector also played a significant role, with partners such as Trend Micro, Prodraft and Secureworks.
How Operation Cronos Took Down LockBit Ransomware Gang
According to Vx-underground, law enforcement agencies managed to compromise LockBit’s infrastructure by exploiting a software vulnerability (CVE-2023-3824).
This is a critical PHP vulnerability that could lead to a stack buffer overflow and potentially memory corruption or remote code execution.
In its public statement, Europol gave further information about its role in the operation.
The case was opened at Eurojust in April 2022 at the request of the French authorities. The Agency hosted five coordination meetings to facilitate judicial cooperation and prepare for the joint action.
Subsequently, Europol’s European Cybercrime Centre (EC3) organized 27 operational meetings and four technical one-week sprints to develop the investigative leads in preparation for the final phase of the investigation.
During the final phase, three Europol experts were deployed to the command post in London during the action phase.
The agency also provided analytical, crypto-tracing, and forensic support to the investigation and facilitated the information exchange in the framework of the Joint Cybercrime Action Taskforce (J-CAT) hosted at its headquarters.
“In total, over 1000 operational messages have been exchanged on this case via Europol’s secure information channel SIENA, making it one of EC3’s most active investigations,” Europol added.
LockBit Warns Its Affiliates and Suggests a Future Come-Back
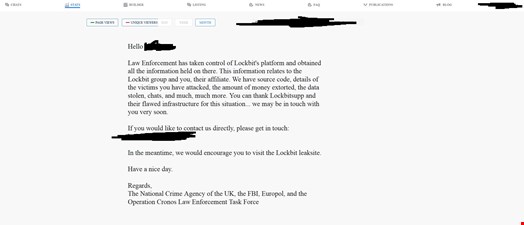
Since Operation Cronos took down LockBit’s infrastructure, the group affiliates who want to connect to its affiliate panel are faced with a message warning them of the takedown and encouraging them to contact law enforcement and check LockBit’s data leak site.
When asked by Vx-underground to confirm the takedown before it was made public, LockBitSupp, the persona allegedly running the ransomware group, responded that “FBI pawned me.”
Since then, LockBit has sent a letter to its affiliates recommending they change their passwords, enable multifactor authentication (MFA), and monitor any abnormal activity. Essentially practicing good cyber hygiene.

LockBitSupp also claimed some of its servers were unaffected by the takedown, suggesting a possible future come-back.
According to a dark web monitoring analysis led by Searchlight Cyber, the LockBit takedown sparked astonishment, with many on the Russian cybercrime forum XSS expressing their surprise that such a prominent group was taken down. Others were even blaming LockBit for having bad operation security (OpSec).
Speaking to Infosecurity, a Searchlight Cyber spokesperson commented: “The general consensus is that LockBit is unlikely to be taken offline forever, and many speculate that a ‘reincarnation’ is likely to happen.
“However, as there wasn’t much official information available up until this point in time, even notorious actors known for their history of selling initial access to corporate networks – possibly even affiliates of the ransomware gang – were unsure if they should be concerned or not, not knowing to what extent the infrastructure of LockBit has been compromised.
Is Ransomware Over? What the LockBit Takedown Means for Your Business
Decryptor and Recovery Tools Available to LockBit Victims
One significant result of Operation Cronos was that law enforcement agencies were able to get hold of LockBit’s decryption keys.
This has allowed the NCA, the FBI and the Japanese Police, with the support of Europol. to develop new decryption tools designed to recover files encrypted by the LockBit ransomware.
Many voices in the cybersecurity community described this as a significant success for law enforcement operations.
“Law enforcement may be able to assist you to decrypt your LockBit encrypted files,” reads a message displayed on LockBit’s data leak site.
The NCA said it had over 1000 decryption keys and would contact UK-based victims in the coming days and weeks to help them recover encrypted data.
In a public statement, the DoJ commented: “Beginning today, victims targeted by this malware are encouraged to contact the FBI at https://lockbitvictims.ic3.gov/ to enable law enforcement to determine whether affected systems can be successfully decrypted.”
These solutions have also been made available for free on the ‘No More Ransom’ portal, available in 37 languages.
“So far, more than 6 million victims across the globe have benefitted from No More Ransom, which contains over 120 solutions capable of decrypting more than 150 different types of ransomware,” Europol said in a public statement.
Cyber Experts Express Cautious Optimism on LockBit Takedown
Generally, the cybersecurity community praised the takedown operation for its many successes.
Jamie Akthar, co-founder and CEO of CyberSmart, called it “a major victory,” while Javvad Malik, lead security awareness advocate at KnowBe4, said that the operation “marks a decisive blow to LockBit’s operations.”
Tim West, director of threat intelligence and outreach at WithSecure, said: “Of all the ransomware brands to disrupt, LockBit is almost certainly the preferred choice. Responsible for approximately a fifth of all ransomware breach site posts in 2023, and 25% so far in 2024, LockBit is by far considered the most prolific, resourced, professional, and capable.”
The NCA reveals details of an international disruption campaign targeting the world’s most harmful cyber crime group, Lockbit.
Watch our video and read on to learn more about Lockbit and why this is a huge step in our collective fight against cyber crime. pic.twitter.com/m00VFWkR9Z
— National Crime Agency (NCA) (@NCA_UK) February 20, 2024
Huseyin Can Yuceel, a security researcher at Picus Security, was enthused that “Operation Cronos gave LockBit operators a taste of their own medicine.”
He added that he was dubitative about the possibility of a LockBit return anytime soon.
“Although the LockBit group claims to have untouched backup servers, it is unclear whether they will be back online. Currently, LockBit associates are not able to login to LockBit services. In a Tox message, adversaries told their associates that they would publish a new leak site after the rebuild.”
However, cybersecurity professionals are more nuanced about the operation’s impact in the longer term.
“Takedowns are short-lived if no one is arrested,” said Yuceel
West agreed: “Lockbit has proven itself in the past to be a resilient ransomware variant, surviving major leaks and rebrands; we do not yet know the impact that these takedowns will have on operations.”
Akthar, also warned of a possible return of LockBit actors in the long term but insisted that even such a come-back does not mean the operation was not helpful.
“If we know anything about cybercriminals, it’s that those groups who remain at large are likely to study this closely and evolve. What makes cybercrime so pernicious is its hydra-like ability for more groups to spring up each time one is taken out. As such, we expect them to redouble their efforts following this setback.
“Despite this, this story should serve as a welcome morale boost for anyone involved in the battle against cybercrime. It proves that even the most sophisticated cybercriminals can be beaten and stopped.”
