Cyber threat intelligence giant Mandiant has shared the results of its investigation on its recent X account hijacking following a wave of crypto-related X account hacks.
On January 3, 2024, the X (formerly Twitter) account of Mandiant, a subsidiary of Google Cloud, was taken over and began sending its 123,5000 followers links to a cryptocurrency drainer phishing page.
The firm recovered its account the next day and announced it on social media with the following post: “As you likely noticed, yesterday, Mandiant lost control of this X account, which had 2FA enabled. Currently, there are no indications of malicious activity beyond the impacted X account, which is back under our control. We’ll share our investigation findings once concluded.”
On January 11, the firm published the result of this investigation, which determined the hijack was likely due to a brute-force password attack and was limited to the company’s primary X account, @Mandiant.
We have finished our investigation into last week’s Mandiant X account takeover and determined it was likely a brute force password attack, limited to this single account.
— Mandiant (@Mandiant) January 10, 2024
The investigation found “no evidence of malicious activity on, or compromise of, any Mandiant or Google Cloud systems that led to the compromise of this account.”
Mandiant Blames X’s 2FA Changes
In its communication, Mandiant pointed to misconfigurations in its account’s two-factor authentication (2FA), for which the firm took some responsibility but also laid the blame partly on X.
“Normally, 2FA would have mitigated this, but due to some team transitions and a change in X’s 2FA policy, we were not adequately protected. We’ve made changes to our process to ensure this doesn’t happen again,” the firm’s social media post said.
Although the cybersecurity provider did not specify which X changes it was referring to, 2FA recently became an exclusive feature for X Premium subscribers.
Previously, all users could enable 2FA for added security, but now, only those paying for the subscription service can access elements of this feature.
Specifically, the text message/SMS method of 2FA was disabled for non-Twitter Blue users in February 2023. Authentication app and security key methods remain available.
This decision sparked considerable controversy among the user base, as 2FA is considered a crucial security measure and limiting its availability raises concerns about potential vulnerabilities.
The @Mandiant account has no Gold checkmark on X, which could mean the company has not subscribed to the social media’s premium plan.
Read more: Is MFA Enough to Protect You Against Cyber-Attacks?
CLINKSINK Drainer-as-a-Service Threat Actors Behind the Hack
Mandiant has identified 35 IDs associated with a drainer-as-a-service (DaaS) group using the CLINKSINK crypto wallet drainer, a type of malware exploiting vulnerabilities in smart contracts or user errors to steal funds.
CLINKSINK users specifically targets Solana (SOL) wallets.
These digital grifters use hijacked X and Discord accounts to share cryptocurrency-themed phishing pages impersonating Phantom, DappRadar, and BONK with fake token airdrop themes.
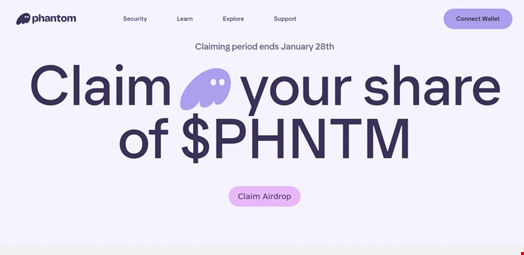
Using these compromised accounts, they lure their victims with promises of free tokens, deploying convincing phishing pages disguised as popular crypto platforms.
Instead of enriching their targets, they’re siphoning funds directly into their own pockets, keeping 20% for themselves and leaving the rest for the shadowy figures who run the drainer service.
Mandiant estimates that this nefarious scheme has drained at least $900,000 from unsuspecting crypto enthusiasts.
The same 35 affiliate IDs have used CLINKSINK since December 2023 to steal funds and tokens from Solana users in different campaigns.
A Wave of Crypto-Related X Account Hijacks
Several companies, including Netgear, Hyundai and Certik, have also recently had their X social media accounts hijacked and used for cryptocurrency scams by threat actors.
On January 10, the X account for the US Securities and Exchange Commission, @SECGov, was compromised and posted a fake announcement regarding the approval of Bitcoin exchange-traded funds (ETFs ) on security exchanges, leading to Bitcoin prices briefly spiking.
X’s safety team later said the takeover was due to the hijack of a phone number associated with the @SECGov account in a SIM-swapping attack. X also noted that the SEC’s account did not have two-factor authentication (2FA) enabled at the time the account was hacked.
