This new product offers SaaS discovery and risk assessment coupled with a free user access review in a unique “freemium” model
Securing employees’ SaaS usage is becoming increasingly crucial for most cloud-based organizations. While numerous tools are available to address this need, they often employ different approaches and technologies, leading to unnecessary confusion and complexity. Enter Wing Security’s new “Essential SSPM” (SaaS Security Posture Management) tool, which aims to simplify the process of securing SaaS usage across the organization. Its business approach is simple: self-onboard, try the product, and if impressed, upgrade to unlock more vital security capabilities.
What’s essential SaaS security?
According to Wing, three basic yet fundamental capabilities are necessary for organizations aiming to secure their SaaS: discovery, assessment, and control. These align with regulatory security standards such as ISO 27001 and SOC, which emphasize vendor and third-party risk assessment programs, as well as controlling user access to critical business tools.
1. Discover: You can’t secure what you can’t see
Shadow IT is not a novel issue but rather an evolving one. With the continuous increase in SaaS usage and the ability for users to bypass security policies like MFA and SSO when onboarding SaaS applications, the new face of shadow IT is SaaS-based. The process is simple: employees need to complete a business task and often require a tool to facilitate it. They search for a solution online, using company credentials to log in, particularly when most services don’t require credit card information to get started. SaaS, being the modern supply chain, clearly requires a security solution due to its decentralized and ungoverned nature.
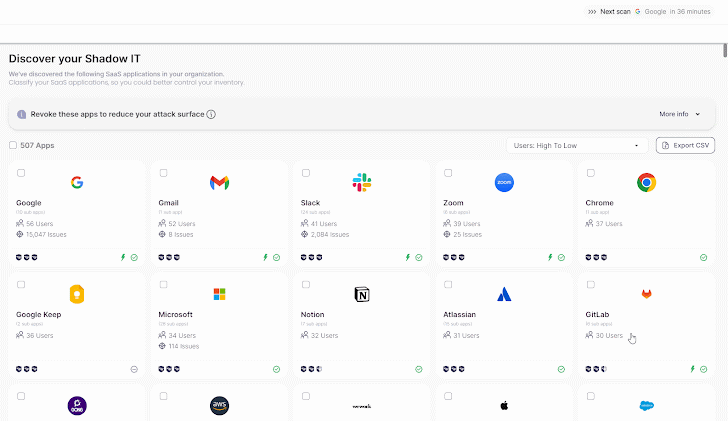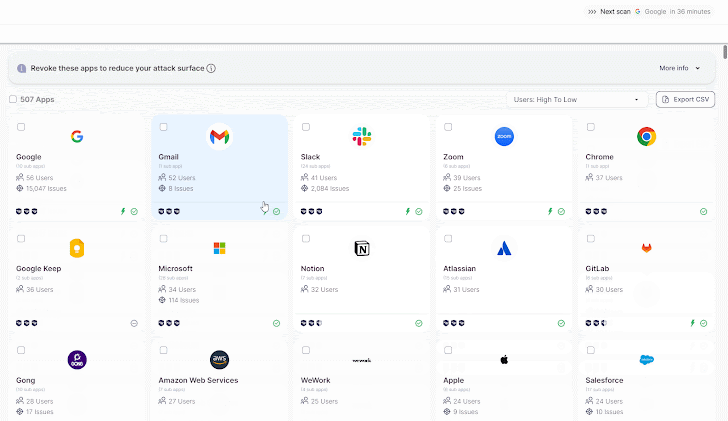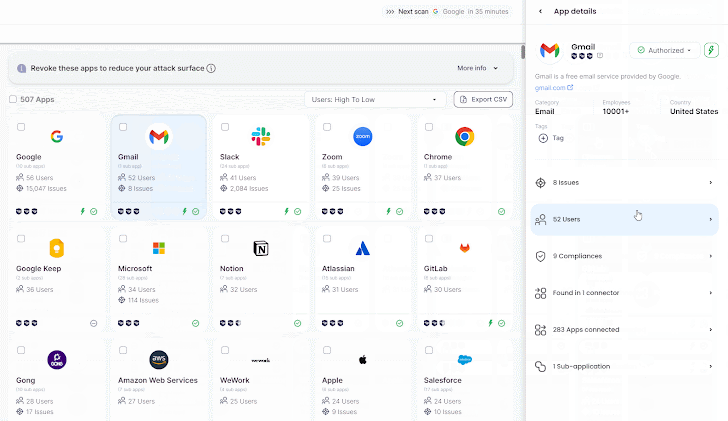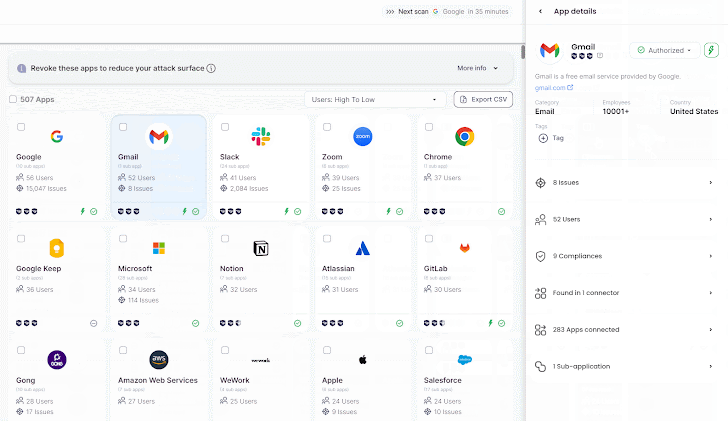 |
| Wing’s SaaS discovery |
2. Assess risk: Not all risks are equal, save valuable time
Once the shadow element is resolved, organizations are left with an extensive list of applications, often numbering in the thousands. This begs the question: what now? Without an automated method for evaluating the risks associated with all the SaaS applications linked to the organization, uncovering shadow SaaS can be more confusing and burdensome than helpful. This highlights the importance of assessing the security status of these applications and determining a threshold that requires attention.
SaaS discovery must go hand in hand with some degree of vendor or third-party risk assessment. Wing’s new product tier combines SaaS discovery with an automated processes for determining an application’s SaaS security score. This risk information is extracted from a vast SaaS database of over 280,000 SaaS on record, cross-checked with the data from hundreds of Wing’s users and their SaaS environments. Paying customers benefit from broader and deeper SaaS risk assessments, including near-real-time threat intelligence alerts.
3. Control: Ensure users only have necessary access
Discovering all SaaS in use (and not in use) and understanding their risks is only half the battle; the other half involves SaaS users. They grant applications access and permissions to company data, making choices regarding read/write permissions for the numerous applications they use. On average, each employee uses 28 SaaS applications at any given time, which translates to hundreds, if not thousands, of SaaS applications with access to company data.
Conducting periodic user access reviews across essential business applications is not just a regulatory requirement but also highly recommended for maintaining a secure posture. Controlling who has access to which application can prevent sensitive data from falling into the wrong hands and significantly reduce the potential attack surface, as employees are often the first targets for malicious actors. A long list of users and their permissions and roles across various applications can be overwhelming, which is why Wing aids in prioritizing users based on their permissions, their roles and by encouraging the least privilege concept. This ensures that all users, except approved admins, have only basic access to SaaS applications.
 |
| Wing’s User Access Review |
In summary – These three capabilities are essential for starting a proper SaaS security program, but they don’t guarantee full coverage or control. Mature security organizations will require more. Data security features, automated remediation paths and more control over user privileges and behaviors are only possible with Wing’s full solution. That said, these are an important starting point for those organizations who don’t yet have SaaS security in place or are contemplating which tools and approaches to get started with.
How is this different from a POC or interactive demo?
This new “try first, pay later” approach differs from the average POC primarily in its completely no-touch nature. Users can self-onboard the product by agreeing to Wing’s legal conditions, without the need to interact with a human representative or sales personnel, unless they choose to. While the free product is intentionally limited in features and capabilities, it provides a starting point for those curious about or seeking SaaS security. Unlike online demos, this process involves the actual processing of your data and can genuinely enhance your security posture by providing visibility into your company’s real SaaS usage and by allowing you to evaluate the magnitude of your SaaS attack surface. A freemium approach in security-related products is uncommon, making this an opportunity for those who wish to test the product before committing.
