SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert’s head spin. If you’re embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance.
What is cybersecurity compliance?
Cybersecurity compliance means you have met a set of agreed rules regarding the way you protect sensitive information and customer data. These rules can be set by law, regulatory authorities, trade associations or industry groups.
For example, the GDPR is set by the EU with a wide range of cybersecurity requirements that every organization within its scope must comply with, while ISO 27001 is a voluntary (but internationally recognized) set of best practices for information security management. Customers increasingly expect the assurance that compliance brings, because breaches and data disclosure will impact their operations, revenue and reputation too.
Which cybersecurity compliance standard is right for you?
Every business in every industry is operationally different and has different cybersecurity needs. The safeguards used to keep hospital patient records confidential are not the same as the regulations for keeping customers’ financial information secure.
For certain industries, compliance is the law. Industries that deal with sensitive personal information such as healthcare and finance are highly regulated. In some cases, cybersecurity regulations overlap across industries. For example, if you’re a business in the EU that handles credit card payments, then you’ll need to be compliant with both credit and banking card regulations (PCI DSS) and GDPR.
Security basics like risk assessments, encrypted data storage, vulnerability management and incident response plans are fairly common across standards, but what systems and operations must be secured, and how, are specific to each standard. The standards we explore below are far from exhaustive, but they are the most common compliance for start-ups and SaaS businesses that handle digital data. Let’s dive in.
GDPR
The General Data Protection Regulation (GDPR) is a far-reaching piece of legislation that governs how businesses – including those in the US – collect and store the private data of European Union citizens. Fines for non-compliance are high and the EU is not shy about enforcing them.
Who needs to comply with GDPR?
Buckle up because it’s anyone that collects or processes the personal data of anyone in the EU, wherever they go or shop online. Personal information or “personal data” includes just about anything from the name and date of birth to geographic information, IP address, cookie identifiers, health data and payment information. So, if you do business with EU residents, you’re required to comply with GDPR.
How vulnerability scanning can aid compliance with GDPR
Your IT security policy for GDPR doesn’t have to be a complicated document – it just needs to lay out in easy-to-understand terms, the security protocols your business and employees should follow. You can also use free templates from SANS as models.
You can start taking simple steps right away. There are automated platforms that make it easier to work out which requirements you already meet, and which ones you need to correct. For example, you’re required to “develop and implement appropriate safeguards to limit or contain the impact of a potential cybersecurity event” which vulnerability scanning using a tool like Intruder can help you achieve.
SOC 2
SaaS and born-in-the-cloud businesses that provide digital services and systems will be most familiar with SOC 2 as it covers the storage, handling and transmission of digital data, although certification is becoming increasingly popular with all service providers.
There are two reports: Type 1 is a point-in-time assessment of your cyber security posture; Type 2 is an ongoing audit by an external assessor to check you’re meeting these commitments, reviewed and renewed every 12 months. SOC 2 gives you some wiggle room on how to meet its criteria, whereas PCI DSS, HIPAA and other security frameworks have very explicit requirements.
Who needs SOC 2 compliance?
While SOC 2 isn’t a legal requirement, it’s the most sought-after security framework for growing SaaS providers. It’s quicker and cheaper to achieve than most of the other standards in this list, while still demonstrating a concrete commitment to cyber security.
How do you comply with SOC 2?
SOC 2 compliance requires you to put in place controls or safeguards on system monitoring, data alert breaches, audit procedures and digital forensics. The subsequent SOC 2 report is the auditor’s opinion on how these controls fit the requirements of five ‘trust principles’: security, confidentiality, processing integrity, availability and privacy.
ISO 27001
ISO produces a set of voluntary standards for a variety of industries – ISO 27001 is the standard for best practice in an ISMS (information security management system) to manage the security of financial information, intellectual property, personnel information, and other third-party information. ISO 27001 is not a legal requirement by default, but many large enterprises or government agencies will only work with you if you’re ISO certified. It’s recognised as one of the most rigorous frameworks but it’s notoriously difficult, expensive and time consuming to complete.
Who needs it?
Like SOC 2, ISO 27001 is a good way to demonstrate publicly that your business is committed and diligent when it comes to information security, and that you’ve taken steps to keep the data you share with them secure.
How do you comply with ISO 27001?
Third-party auditors validate that you’ve implemented all of the relevant best practices in accordance with the ISO standard. There isn’t a universal ISO 27001 checklist that guarantees certification. It’s up to you to decide how to decide what’s in scope and implement the framework, and auditors will use their discretion to evaluate each case.
Remember that ISO 27001 is largely about risk management. Risks are not static and evolve as new cyber threats emerge, so you should build automated vulnerability management with a tool like Intruder into your security controls to evaluate and analyze new risks as they emerge. Automated compliance platforms such as Drata can help speed up the process.
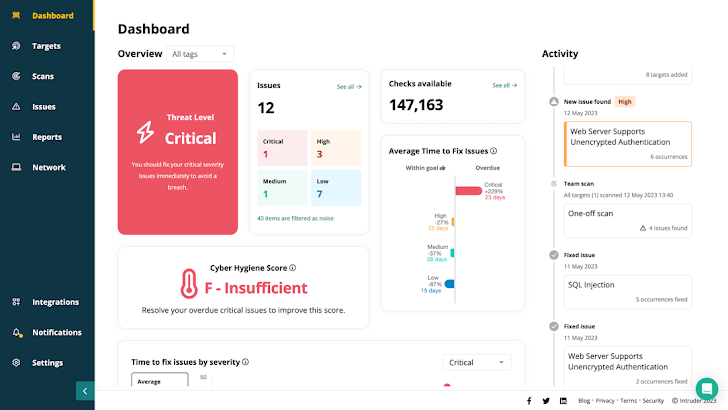 |
| Intruder provides actionable, audit ready reports, so you can easily show your security posture to auditors, stakeholders and customers |
PCI DSS
The PCI DSS (Data Security Standard) was developed by the PCI Security Standards Council and the major card brands (American Express, Mastercard and Visa) to regulate anyone that stores, processes, and/or transmits cardholder data.
Who needs it?
In theory, anyone that processes card payment transactions, but there are different rules depending on the number and type of payments you take. If you use a third-party card payment provider like Stripe or Sage, they should manage the process and provide validation for you.
How to comply with PCI DSS
Unlike ISO 27001 and SOC 2, PCI DSS requires a strict vulnerability management program but accreditation is complex. Third-party payment providers will usually populate the PCI form automatically, providing validation at the click of a button. For smaller businesses, this can save hours of work.
HIPAA
HIPAA (the Health Insurance Portability and Accountability Act) regulates the transfer and storage of patient data in the US healthcare industry, where compliance is a legal requirement.
Who needs it?
HIPAA compliance is mandatory for any business that handles patient information in the US, or anyone doing business in the US with companies that are also HIPAA compliant.
How to comply with HIPAA
HIPAA can be difficult to navigate. It requires a risk management plan with security measures sufficient to reduce risk to a reasonable and appropriate level. Although HIPAA doesn’t specify the methodology, vulnerability scans or penetration tests with a tool like Intruder should be integral components of any risk analysis and management process.
Cyber Essentials
Cyber Essentials is a UK government-backed scheme designed to check businesses are adequately protected against common cyberattacks. Similar to SOC 2, think of it as good cyber hygiene – like washing your hands or brushing your teeth. Designed for the smaller business without dedicated security expertise, it should be just the starting point of a more robust security program
Who needs Cyber Essentials compliance?
Any business bidding for a UK government or public sector contract which involves sensitive and personal information or providing certain technical products and services.
How to comply with Cyber Essentials
The basic certificate is a self-assessment of basic security controls. Cyber Essentials Plus is a more advanced, comprehensive, hands-on technical certification that includes a series of vulnerability tests that can be provided by an automated tool like Intruder. The internal test is an authenticated internal scan and a test of the security and anti-malware configuration of each device.
Compliance doesn’t have to mean complexity
Compliance can seem like a labour-intensive and expensive exercise, but it can pale in comparison to the cost of fixing a breach, paying settlements to customers, losing your reputation, or paying fines. You can also miss out on potential business if you don’t have the certifications customers expect.
But cybersecurity compliance doesn’t need to be difficult with today’s automated tools. If you use Intruder’s vulnerability management that already integrates with automated compliance platforms like Drata then auditing, reporting and documentation for compliance becomes a whole lot quicker and easier. Whether you’re just starting your compliance journey or looking to improve your security, Intruder can help you get there faster. Get started today with a free trial.