Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign.
“Deadglyph’s architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly,” ESET said in a new report shared with The Hacker News.
“This combination is unusual because malware typically uses only one programming language for its components. This difference might indicate separate development of those two components while also taking advantage of unique features of the distinct programming languages they utilize.”
It’s also suspected that the use of different programming languages is a deliberate tactic to hinder analysis, making it a lot more challenging to navigate and debug.
Unlike other traditional backdoors of its kind, the commands are received from an actor-controlled server in the form of additional modules that allow it to create new processes, read files, and collect information from the compromised systems.
Stealth Falcon (aka FruityArmor) was first exposed by the Citizen Lab in 2016, linking it to a set of targeted spyware attacks in the Middle East aimed at journalists, activists, and dissidents in the U.A.E. using spear-phishing lures embedding booby-trapped links pointing to macro-laced documents to deliver a custom implant capable of executing arbitrary commands.

A subsequent investigation undertaken by Reuters in 2019 revealed a clandestine operation called Project Raven that involved a group of former U.S. intelligence operatives who were recruited by a cybersecurity firm named DarkMatter to spy on targets critical of the Arab monarchy.
Stealth Falcon and Project Raven are believed to be the same group based on the overlaps in tactics and targeting.
The group has since been linked to the zero-day exploitation of Windows flaws such as CVE-2018-8611 and CVE-2019-0797, with Mandiant noting in April 2020 that the espionage actor “used more zero-days than any other group” from 2016 to 2019.
Around the same time, ESET detailed the adversary’s use of a backdoor named Win32/StealthFalcon that was found to use the Windows Background Intelligent Transfer Service (BITS) for command-and-control (C2) communications and to gain complete control of an endpoint.
Deadglyph is the latest addition to Stealth Falcon’s arsenal, according to the Slovak cybersecurity firm, which analyzed an intrusion at an unnamed governmental entity in the Middle East.
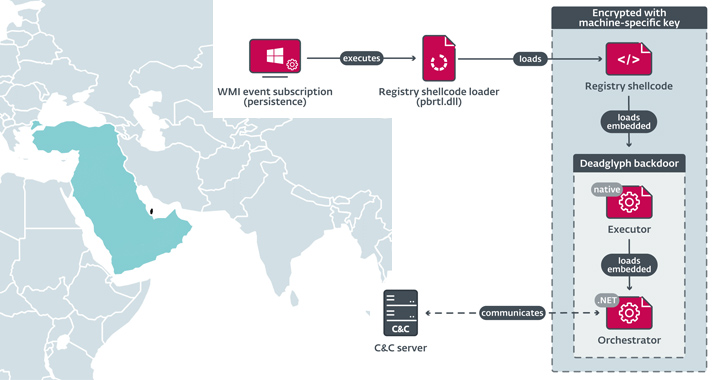
The exact method used to deliver the implant is currently unknown, but the initial component that activates its execution is a shellcode loader that extracts and loads shellcode from the Windows Registry, which subsequently launches Deadglyph’s native x64 module, referred to as the Executor.
The Executor then proceeds with loading a .NET component known as the Orchestrator that, in turn, communicates with the command-and-control (C2) server to await further instructions. The malware also engages in a series of evasive maneuvers to fly under the radar, counting the ability to uninstall itself.
The commands received from the server are queued for execution and can fall into one of three categories: Orchestrator tasks, Executor tasks, and Upload tasks.
“Executor tasks offer the ability to manage the backdoor and execute additional modules,” ESET said. “Orchestrator tasks offer the ability to manage the configuration of the Network and Timer modules, and also to cancel pending tasks.”
AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Ready to tackle new AI-driven cybersecurity challenges? Join our insightful webinar with Zscaler to address the growing threat of generative AI in cybersecurity.
Some of the identified Executor tasks comprise process creation, file access, and system metadata collection. The Timer module is used to poll the C2 server periodically in combination with the Network module, which implements the C2 communications using HTTPS POST requests.
Upload tasks, as the name implies, allow the backdoor to upload the output of commands and errors.
ESET said it also identified a control panel (CPL) file that was uploaded to VirusTotal from Qatar, which is said to have functioned as a starting point for a multi-stage chain that paves the way for a shellcode downloader that shares some code resemblances with Deadglyph.
While the nature of the shellcode retrieved from the C2 server remains unclear, it has been theorized that the content could potentially serve as the installer for the Deadglyph malware.
Deadglyph gets its name from artifacts found in the backdoor (hexadecimal IDs 0xDEADB001 and 0xDEADB101 for the Timer module and its configuration), coupled with the presence of a homoglyph attack impersonating Microsoft (“Ϻicrоsоft Corpоratiоn”) in the Registry shellcode loader’s VERSIONINFO resource.
“Deadglyph boasts a range of counter-detection mechanisms, including continuous monitoring of system processes and the implementation of randomized network patterns,” the company said. “Furthermore, the backdoor is capable of uninstalling itself to minimize the likelihood of its detection in certain cases.”