A “staggering” 120,000 computers infected by stealer malware have credentials associated with cybercrime forums, many of them belonging to malicious actors.
The findings come from Hudson Rock, which analyzed data collected from computers compromised between 2018 to 2023.
“Hackers around the world infect computers opportunistically by promoting results for fake software or through YouTube tutorials directing victims to download infected software,” Hudson Rock CTO Alon Gal told The Hacker News.
“It is not a case of the threat actor infecting his own computer, it is that out of the 14,500,000 computers we have in our cybercrime database, some of them happen to be hackers that accidentally got infected.”
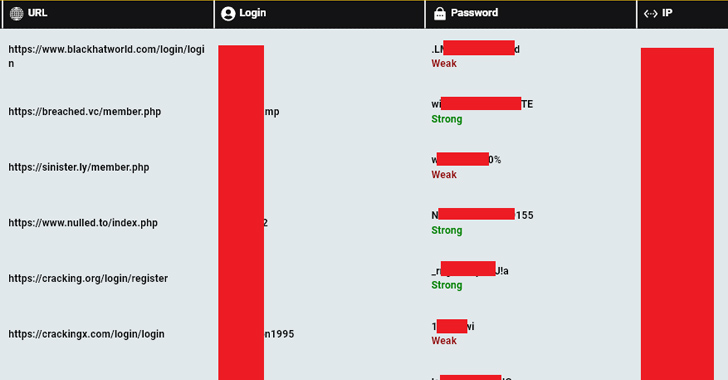
Data retrieved from machines compromised by stealer malware is often expansive and wide-ranging, enabling the real-world identities of hackers to be discovered based on indicators such as credentials, addresses, phone numbers, computer names, and IP addresses.

Information stealers have also fueled the malware-as-a-service (MaaS) ecosystem, positioning them as one of the most lucrative initial attack vectors used by threat actors to infiltrate organizations and execute a variety of attacks, ranging from espionage to ransomware.
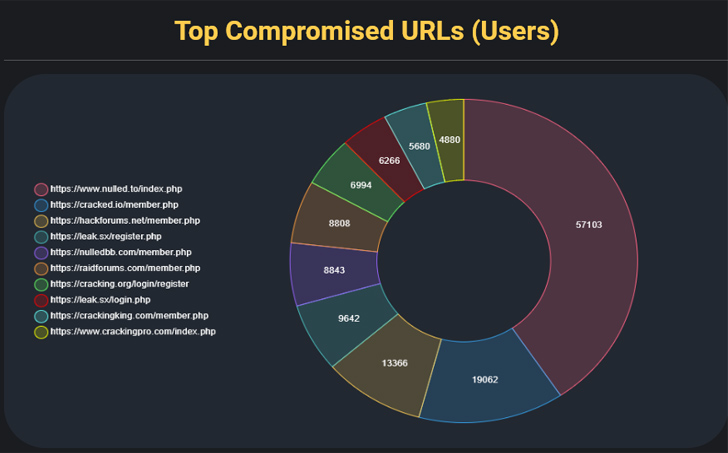
An examination of the pilfered information reveals that the cybercrime forum with the highest number of infected users is Nulled.to with an excess of 57,000 users, followed by Cracked.io (19,062) and Hackforums.net (13,366).
“The forum with the strongest user passwords is ‘Breached.to,’ while the one with the weakest user passwords is the Russian site ‘Rf-cheats.ru,'” the company said, with over 41% of the credentials featuring at least 10 characters and containing four types of characters.
“Overall, passwords from cybercrime forums are stronger than passwords used for government websites, and exhibit fewer ‘very weak’ passwords than industries like the military.”
A vast majority of the infections have been attributed to RedLine, Raccoon, and AZORult. The top countries from which hackers were infected and had at least one credential to a cybercrime forum include Tunisia, Malaysia, Belgium, the Netherlands, and Israel.
“The main takeaways from this finding is that although info stealer infections typically cause harm to companies due to hackers taking advantage of credentials to infiltrate employee and user accounts, they can also be useful for attribution against cyber criminals by law enforcement,” Gal said.

The development comes as Flare’s analysis of more than 19.6 million stealer logs found that 376,107 of them provide access to corporate SaaS applications and that logs containing financial services logins were listed at $112.27, in comparison to $14.31 for the rest.
It also follows the temporary shutdown of Discord.io after it suffered a data breach in which the details pertaining to no less than 760,000 users were leaked on the new Breach hacking forum, which officially resurfaced in June 2023 under the leadership of ShinyHunters.