The Russia-linked threat actor known as Gamaredon has been observed conducting data exfiltration activities within an hour of the initial compromise.
“As a vector of primary compromise, for the most part, emails and messages in messengers (Telegram, WhatsApp, Signal) are used, in most cases, using previously compromised accounts,” the Computer Emergency Response Team of Ukraine (CERT-UA) said in an analysis of the group published last week.
Gamaredon, also called Aqua Blizzard, Armageddon, Shuckworm, or UAC-0010, is a state-sponsored actor with ties to the SBU Main Office in the Autonomous Republic of Crimea, which was annexed by Russia in 2014. The group is estimated to have infected thousands of government computers.
It is also one of the many Russian hacking crews that have maintained an active presence since the start of the Russo-Ukrainian war in February 2022, leveraging phishing campaigns to deliver PowerShell backdoors such as GammaSteel to conduct reconnaissance and execute additional commands.
The messages typically come bearing an archive containing an HTM or HTA file that, when opened, activates the attack sequence.
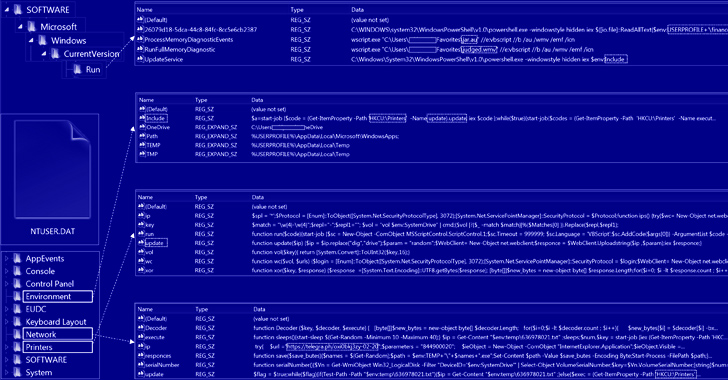
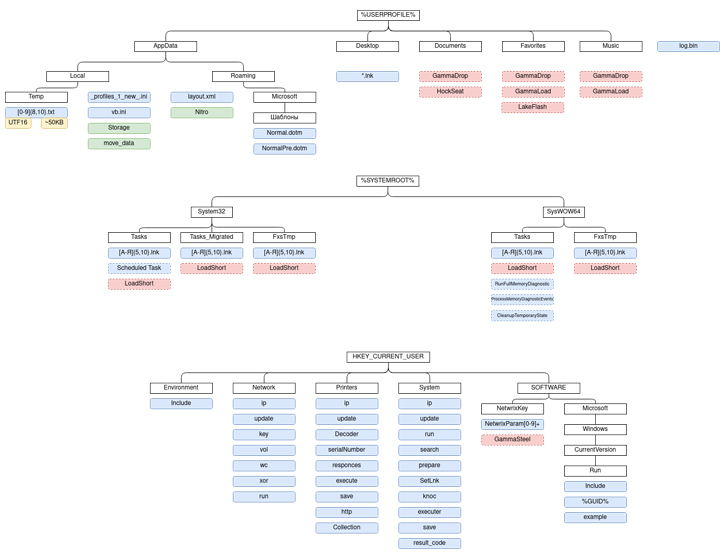
According to CERT-UA, GammaSteel is used to exfiltrate files matching a specific set of extensions – .doc, .docx, .xls, .xlsx, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z, and .mdb – within a time period of 30 to 50 minutes.
The group has also been observed consistently evolving its tactics, making use of USB infection techniques for propagation. A host operating in a compromised state for a week could have anywhere between 80 to 120 malicious files, the agency noted.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
Also significant is the threat actor’s use of AnyDesk software for interactive remote access, PowerShell scripts for session hijacking to bypass two-factor authentication (2FA), and Telegram and Telegraph for fetching the command-and-control (C2) server information.
“Attackers take separate measures to ensure fault tolerance of their network infrastructure and avoid detection at the network level,” CERT-UA said. “During the day, the IP addresses of intermediate control nodes can change from 3 to 6 or more times, which, among other things, indicates the appropriate automation of the process.”