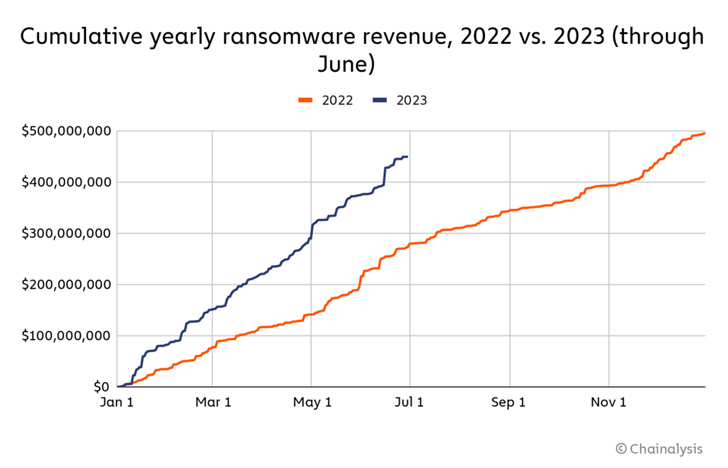
Ransomware has emerged as the only cryptocurrency-based crime to grow in 2023, with cybercriminals extorting nearly $175.8 million more than they did a year ago, according to findings from Chainalysis.
“Ransomware attackers are on pace for their second-biggest year ever, having extorted at least $449.1 million through June,” the blockchain analytics firm said in a midyear crypto crime report shared with The Hacker News. “If this pace continues, ransomware attackers will extort $898.6 million from victims in 2023, trailing only 2021’s $939.9 million.”
In contrast, crypto scams have pulled in 77% less revenue than they did through June of 2022, largely driven by the abrupt exit of VidiLook, which pays users VDL tokens in return for watching digital ads that then can be exchanged for large rewards. So have the inflows to illicit addresses associated with malware, darknet markets, child abuse material, and fraud shops.
The development, following a decline in ransomware revenues in 2022, marks a reversal of sorts, with Chainalysis attributing it to the return of big game hunting after a downturn last year and the increasing number of successful small attacks carried by groups like Dharma and Phobos.
On the other end of the spectrum lie advanced groups like Cl0p (or Clop), BlackCat, and Black Basta, which tend to be more selective in their targeting, while also striking bigger organizations to demand higher ransoms. Cl0p’s average payment size for the first half of 2023 stands at $1,730,486, in contrast to Dharma’s $275.
Cl0p, in particular, has been on a rampage in recent months, exploiting security flaws in MOVEit Transfer application to breach 257 organizations across the world to date, per Emsisoft researcher Brett Callow. More than 17.7 million individuals are said to be impacted as a result of the ransomware attacks.
“Clop’s preference for targeting larger companies (>$5 million/year revenue) and capitalizing on newer-but-disclosed vulnerabilities has been the primary driver of its success in the first half of 2023,” Sophos researcher David Wallace said in a report earlier this week, calling the group a “loud, adaptable, persistent player.”
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
While law enforcement efforts to actively pursue ransomware groups and sanction services offering cashout services, coupled with the availability of decryptors, have emboldened victims to not pay up, it’s suspected that the trend “may be prompting ransomware attackers to increase the size of their ransom demands” to extract funds from companies who are still willing to settle.
Last but not least, the Russia-Ukraine War is also said to have been a contributing factor to the decline in ransomware attacks in 2022, causing the Conti operation to shut shop after declaring support for Russia.
“The conflict likely displaced ransomware operators and diverted them away from financially inspired cyber intrusions,” Chainalysis said. “It stands to reason that the conflict disrupted ransomware operators’ ability to conduct attacks or perhaps even their mandate for such attacks,” especially considering that a majority of ransomware actors are tied to Russia.