Researchers have issued a warning about an emerging and advanced form of voice phishing (vishing) known as “Letscall.” This technique is currently targeting individuals in South Korea.
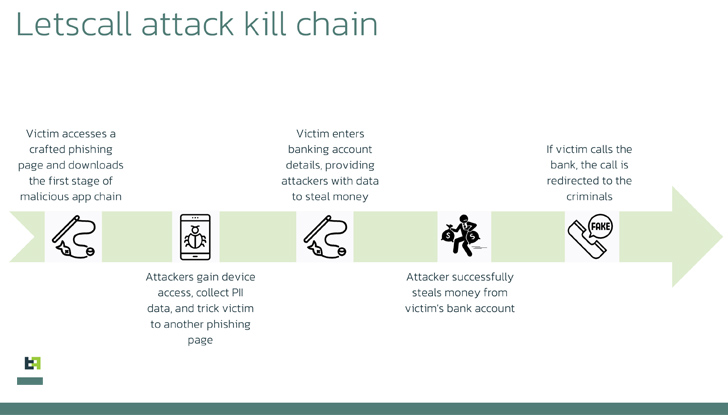
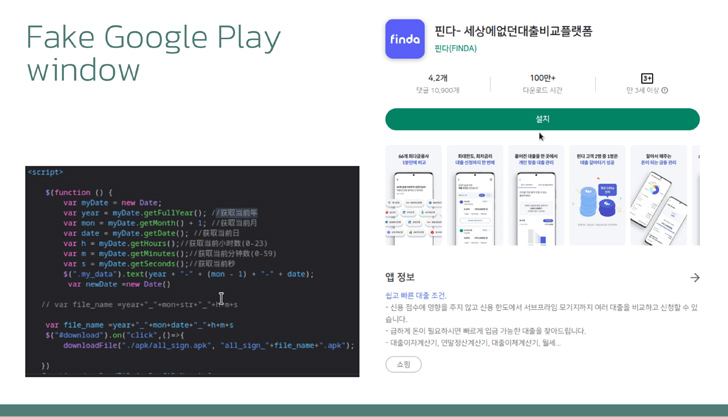
The criminals behind “Letscall” employ a multi-step attack to deceive victims into downloading malicious apps from a counterfeit Google Play Store website.
Once the malicious software is installed, it redirects incoming calls to a call center under the control of the criminals. Trained operators posing as bank employees then extract sensitive information from unsuspecting victims.
To facilitate the routing of voice traffic, “Letscall” utilizes cutting-edge technologies such as voice over IP (VOIP) and WebRTC. It also makes use of Session Traversal Utilities for NAT (STUN) and Traversal Using Relays around NAT (TURN) protocols, including Google STUN servers, to ensure high-quality phone or video calls and bypass NAT and firewall restrictions.
The “Letscall” group consists of Android developers, designers, frontend and backend developers, as well as call operators specializing in voice social engineering attacks.
The malware operates in three stages: first, a downloader app prepares the victim’s device, paving the way for the installation of powerful spyware. This spyware then triggers the final stage, which allows the rerouting of incoming calls to the attackers’ call center.
“The third stage has its own set of commands, which also includes Web socket commands. Some of these commands relate to the manipulation of the address book, such as creating and removing contacts. Other commands relate to creating, modifying, and removing the filters that determine which calls should be intercepted and which should be ignored,” Dutch mobile security firm ThreatFabric said in its report.
What sets “Letscall” apart is its utilization of advanced evasion techniques. The malware incorporates Tencent Legu and Bangcle (SecShell) obfuscation during the initial download. In later stages, it employs complex naming structures in ZIP file directories and intentionally corrupts the manifest to confuse and bypass security systems.
Criminals have developed systems that automatically call victims and play pre-recorded messages to further deceive them. By combining mobile phone infections with vishing techniques, these fraudsters can request micro-loans in the victims’ names while assuring them of suspicious activities and redirecting calls to their centers.
🔐 Privileged Access Management: Learn How to Conquer Key Challenges
Discover different approaches to conquer Privileged Account Management (PAM) challenges and level up your privileged access security strategy.
The consequences of such attacks can be significant, leaving victims burdened with substantial loans to repay. Financial institutions often underestimate the severity of these invasions and fail to investigate potential fraud.
Although this threat is currently limited to South Korea, researchers caution that there are no technical barriers preventing these attackers from expanding to other regions, including the European Union.
This new form of vishing attack underscores the constant evolution of criminal tactics and their ability to exploit technology for malicious purposes. The group responsible for the “Letscall” malware demonstrates intricate knowledge of Android security and voice routing technologies.