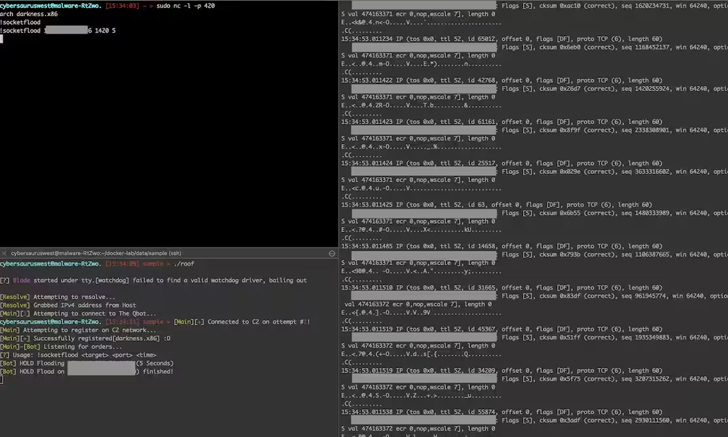
A new botnet called Dark Frost has been observed launching distributed denial-of-service (DDoS) attacks against the gaming industry.
“The Dark Frost botnet, modeled after Gafgyt, QBot, Mirai, and other malware strains, has expanded to encompass hundreds of compromised devices,” Akamai security researcher Allen West said in a new technical analysis shared with The Hacker News.
Targets include gaming companies, game server hosting
providers, online streamers, and even other gaming community members with whom the threat actor has interacted directly.
As of February 2023, the botnet comprises 414 machines running various instruction set architectures such as ARMv4, x86, MIPSEL, MIPS, and ARM7.
Botnets are usually made up of a vast network of compromised devices around the world. The operators tend to use the enslaved hosts to mine cryptocurrency, steal sensitive data, or harness the collective internet bandwidth from these bots to knock down other websites and internet servers by flooding the targets with junk traffic.
Dark Frost represents the latest iteration of a botnet that appears to have been stitched together by stealing source code from various botnet malware strains such as Mirai, Gafgyt, and QBot.
Akamai, which reverse-engineered the botnet after flagging it on February 28, 2023, pegged its attack potential at approximately 629.28 Gbps through a UDP flood attack. The threat actor is believed to be active since at least May 2022.
“What makes this particular case interesting is that the actor behind these attacks has published live recordings of their attacks for all to see,” the web infrastructure company said.
“The actor was observed boasting about their achievements on social media, utilizing the botnet for petty online disputes, and even leaving digital signatures on their binary file.”
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
The adversary has further set up a Discord channel to facilitate attacks in exchange for money, indicating their financial motivations and plans to flesh it out as a DDoS-for-hire service.
Dark Frost constitutes a modern example of how easy it is for novice cybercriminals with rudimentary coding skills to spring into action using already available malware to inflict significant damage on enterprises.
“The reach that these threat actors can have is staggering despite the lack of novelty in their techniques,” West said. “Although not the most advanced or mind-bending adversary, the Dark Frost botnet has still managed to accumulate hundreds of compromised devices to do its bidding.”