Entities in Armenia have come under a cyber attack using an updated version of a backdoor called OxtaRAT that allows remote access and desktop surveillance.
“The tool capabilities include searching for and exfiltrating files from the infected machine, recording the video from the web camera and desktop, remotely controlling the compromised machine with TightVNC, installing a web shell, performing port scanning, and more,” Check Point Research said in a report.
The latest campaign is said to have commenced in November 2022 and marks the first time the threat actors behind the activity have expanded their focus beyond Azerbaijan.
“The threat actors behind these attacks have been targeting human rights organizations, dissidents, and independent media in Azerbaijan for several years,” the cybersecurity firm noted, calling the campaign Operation Silent Watch.
The late 2022 intrusions are significant, not least because of the changes in the infection chain, the steps taken to improve operational security, and equip the backdoor with more ammunition.
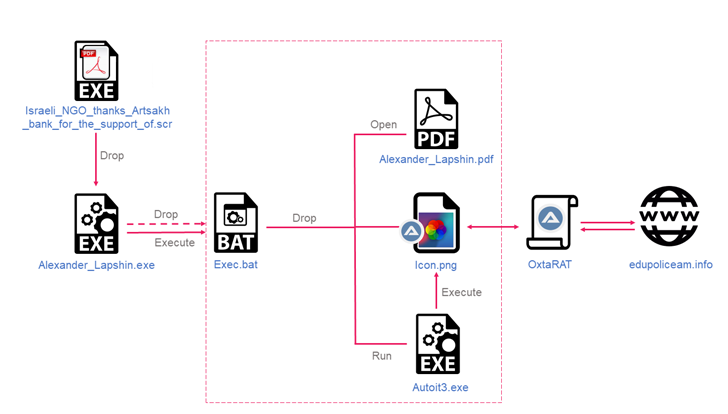
The starting point of the attack sequence is a self-extracting archive that mimics a PDF file and bears a PDF icon. Launching the purported “document” opens a decoy file while also stealthily executing malicious code hidden inside an image.
A polyglot file that combines compiled AutoIT script and an image, OxtaRAT features commands that permit the threat actor to run additional commands and files, harvest sensitive information, perform reconnaissance and surveillance via a web camera, and even pivot to other.
OxtaRAT has been put to use by the adversary as far back as June 2021, albeit with significantly reduced functionality, indicating an attempt to constantly update its toolset and fashion it into a Swiss Army knife malware.
The November 2022 attack also stands out for a number of reasons. The first is that the .SCR files that activate the kill chain already contain the OxtaRAT implant as opposed to acting as a downloader to fetch the malware.
“This saves the actors from needing to make additional requests for binaries to the C&C server and attracting unnecessary attention, as well as hides the main malware from being easily discovered on the infected machine, as it looks like a regular image and bypasses type-specific protections,” Check Point explained.
The second striking aspect is the geofencing of command-and-control (C2) domains that host the auxiliary tools to Armenian IP addresses.
Also of note is the ability of OxtaRAT to run commands for port scanning and to test the speed of an internet connection, that latter of which is likely used as a way to hide the “extensive” data exfiltration.
“OxtaRAT, which previously had mostly local recon and surveillance capabilities, can now be used as a pivot for active reconnaissance of other devices,” Check Point said.
“This may indicate that the threat actors are preparing to extend their main attack vector, which is currently social engineering, to infrastructure-based attacks. It also might be a sign that the actors are moving from targeting individuals to targeting more complex or corporate environments.”
“The underlying threat actors have been maintaining the development of Auto-IT based malware for the last seven years, and are using it in surveillance campaigns whose targets are consistent with Azerbaijani interests.”