In an ideal world, security and development teams would be working together in perfect harmony. But we live in a world of competing priorities, where DevOps and security departments often butt heads with each other.
Agility and security are often at odds with each other— if a new feature is delivered quickly but contains security vulnerabilities, the SecOps team will need to scramble the release and patch the vulnerabilities, which can take days or weeks. On the other hand, if the SecOps team takes too long to review and approve a new feature, the development team will get frustrated with the slow pace of delivery.
Security needs to move slowly and cautiously, while development wants to “move fast and break things” and release new features quickly. DevOps teams can view security as an impediment to their work instead of an important part of the process. With each team pulling in opposite directions, there is often tension and conflict between the two teams, slowing development and leaving organizations open to security risks.
It’s Time to Automate Security Testing
One way to resolve this conflict is to automate testing with every release. Instead of running a one-time pen test when the web application is launched, security teams should ensure vulnerabilities are not being reintroduced with every new release and update in an approach known as “continuous security.”
In continuous security, the SecOps team is involved early and often in the development process. They work with developers to understand the risks associated with new features and help them find ways to mitigate them. By being involved early on, the SecOps team can help to ensure that new features are developed with security in mind from the very beginning.
Advantages of Continuous Pen Testing
Penetration testing is a critical component of web application security. As attack surfaces expand and applications become more complex, regular pen tests become a crucial component of a strong web application security posture.
However, pen testing is often conducted periodically, which results in a “security sprint” every time a new test is scheduled. When conducted late in the release cycle, pen testing can be disruptive to the development process. Discovering vulnerabilities only at certain flagpole points in development often requires extensive and costly rework for Dev and DevOps teams.
As part and parcel of shifting left and improving the workflows between DevOps and Security teams, web application security testing needs to be built into the development process. This way, vulnerabilities can be discovered and fixed before the code is even deployed to production.
A continuous testing approach is an effective way to integrate security testing into the development process so that organizations can identify vulnerabilities without disrupting release cycles. However, despite its advantages, regular and ongoing pen testing can be challenging to implement. It is a resource-intensive process and requires tools and expertise that may not be readily available.
Pen-Testing-as-a-Service: Aligning DevOps and SecOps Priorities
One solution is to partner with a provider that specializes in continuous pen testing and can help implement it in your organization. With Pen-Testing-as-a-Service (PTaaS), you can get started with continuous pen testing quickly and easily without investing in additional resources or expanding your team.
PTaaS solutions build a shared understanding of security issues and their impact. When development team members are given the opportunity to test their code for vulnerabilities and fix them before they reach production, they become more engaged in the security of the applications they are building. Some PTaaS solutions go one step further by offering features that make it easy for developers to fix vulnerabilities, such as providing one-click fixes for common issues.
Outpost24’s Pen Testing as a Service (PTaaS) provides continuous pen tests for web applications throughout a contract period, typically a year or longer. It includes the tools and the expertise you need to implement continuous pen testing in your organization.
Outpost24’s PTaaS solution offers several advantages, including:
- Increased web application security: By integrating security testing into the development process, you can find and fix vulnerabilities early on before they have a chance to cause problems.
- Continuous coverage: PTaaS provides continuous coverage of your applications so you can be confident that they are always secure, even after development updates and vulnerability remediation.
- Expertise on demand: With PTaaS, you have access to the expertise you need when you need it, including 24/7 Portal communications.
- Improved efficiency: PTaaS can help your SecOps communication with DevOps thanks to clear remediation steps and re-testing that allow for continuous development throughout the pen testing period.
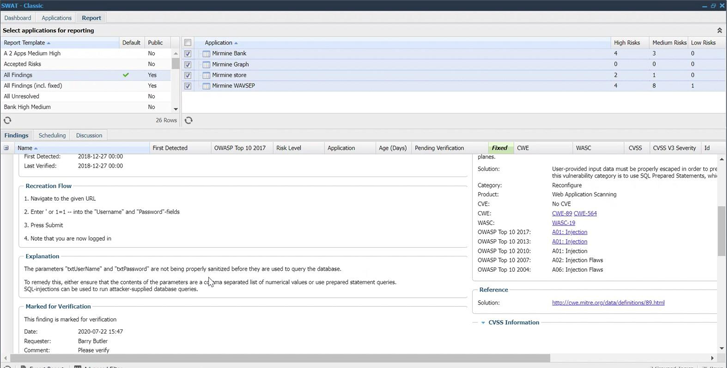 |
| Here’s an example of the remediation process for one of the vulnerabilities found by Outpost24’s continuous pen testing. |
PTaaS is a cost-effective solution that merges application development and security processes into DevSecOps — a continuous, automated, and secure software development lifecycle. By aligning the priorities of development, security, and operations teams, PTaaS enables organizations to deliver secure software faster.
Learn more about how Outpost24 can help you implement continuous penetration testing in your organization by getting in touch, here.
