Researchers have disclosed details about a now-patched critical flaw in the Move virtual machine that powers the Aptos blockchain network.
The vulnerability “can cause Aptos nodes to crash and cause denial of service,” Singapore-based Numen Cyber Labs said in a technical write-up published earlier this month.
Aptos is a new entrant to the blockchain space, which launched its mainnet on October 17, 2022. It has its roots in the Diem stablecoin payment system proposed by Meta (née Facebook), which also introduced a short-lived digital wallet called Novi.
The network is built using a platform-agnostic programming language known as Move, a Rust-based system that’s designed to implement and execute smart contracts in a secure runtime environment, also known as the Move Virtual Machine (aka MoveVM).
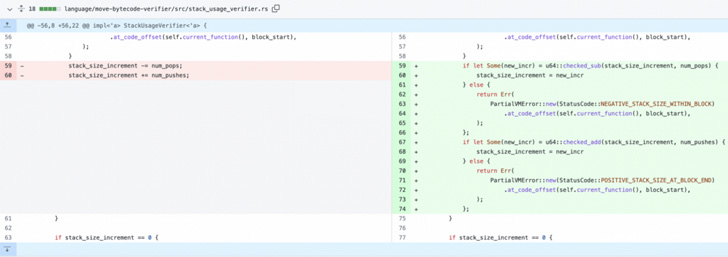
The vulnerability identified by Numen Cyber Labs is rooted in the Move language’s verification module (“stack_usage_verifier.rs“), a component that validates the bytecode instructions prior to its execution in MoveVM.
Specifically, it relates to an integer overflow vulnerability in the stack-based Web3 programming language that could result in undefined behavior and therefore crashes.
“Since this vulnerability occurs in the Move execution module, for nodes on the chain, if the bytecode code is executed, it will cause a [Denial-of-Service] attack,” the cybersecurity firm explained.
“In severe cases, the Aptos network can be completely stopped, which will cause incalculable damage, and have a serious impact on the stability of the node.”