Cybersecurity researchers have shared more details about a now-patched security flaw in Azure Service Fabric Explorer (SFX) that could potentially enable an attacker to gain administrator privileges on the cluster.
The vulnerability, tracked as CVE-2022-35829, carries a CVSS severity rating of 6.2 and was addressed by Microsoft as part of its Patch Tuesday updates last week.
Orca Security, which discovered and reported the flaw to the tech giant on August 11, 2022, dubbed the vulnerability FabriXss (pronounced “fabrics”). It impacts Azure Fabric Explorer version 8.1.316 and prior.
SFX is described by Microsoft as an open-source tool for inspecting and managing Azure Service Fabric clusters, a distributed systems platform that’s used to build and deploy microservices-based cloud applications.
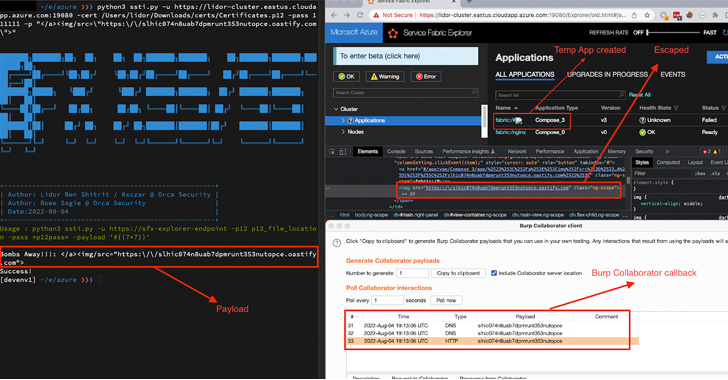
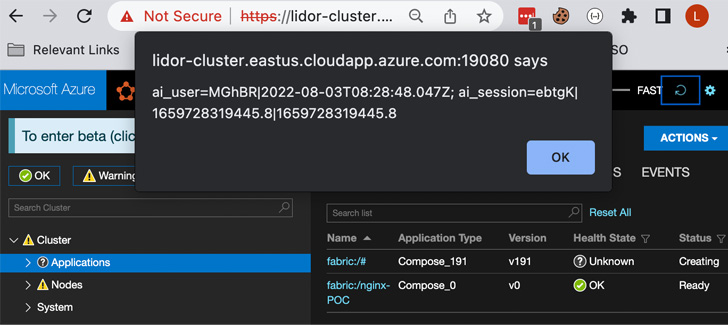
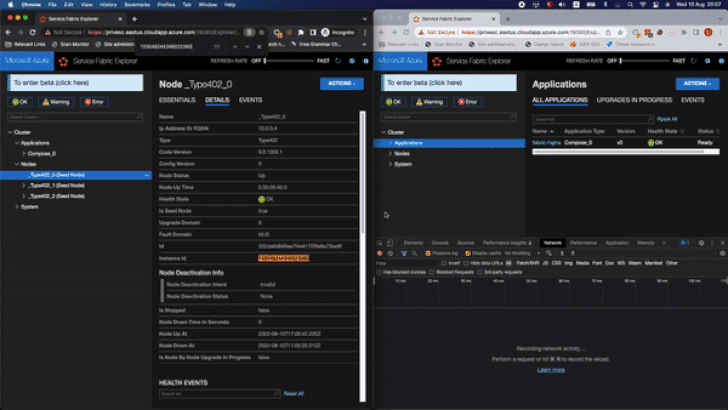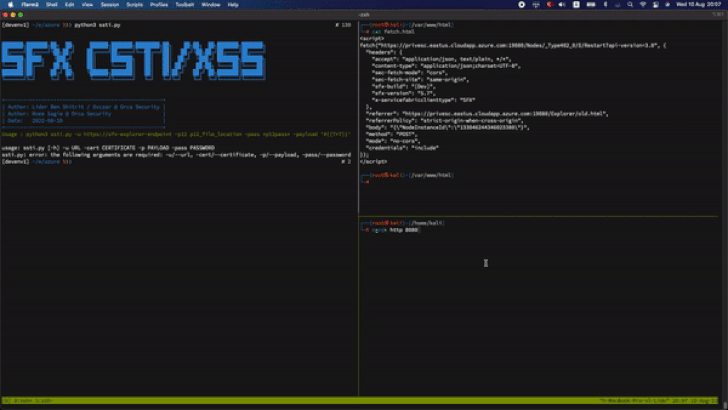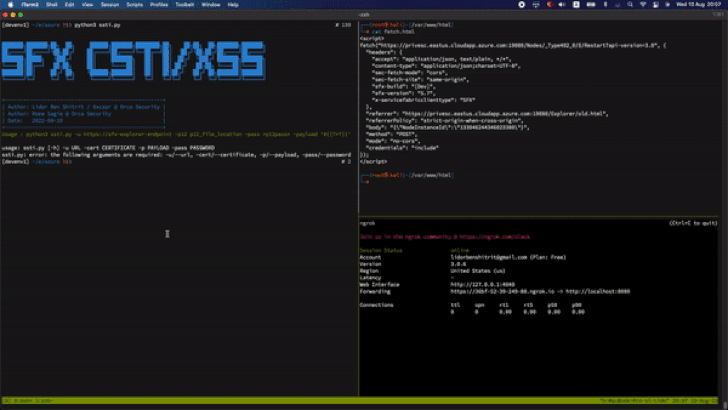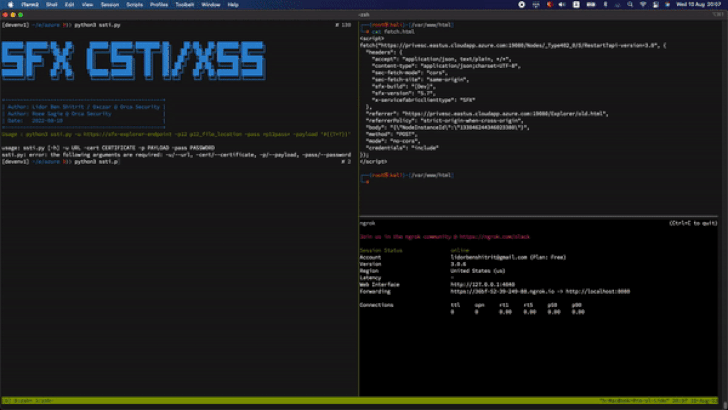
The vulnerability is rooted in the fact that a user with permissions to “Create Compose Application” through the SFX client can leverage the privileges to create a rogue app and abuse a stored cross-site scripting (XSS) flaw in the “Application name” field to slip the payload.
Armed with this exploit, an adversary can send the specially crafted input during the application creation step, eventually leading to its execution.
“This includes performing a Cluster Node reset, which erases all customized settings such as passwords and security configurations, allowing an attacker to create new passwords and gain full Administrator permissions,” Orca Security researchers Lidor Ben Shitrit and Roee Sagi said.