Both cryptocurrency and ransomware are nothing new in the digital world; both have been there for a very long time, which was enough for them to find common pieces for starting their relationship.
Ransomware can be like a virtual car that works on all types of fuels, and crypto is the one that is currently most recommended. No one can argue that 2020 was the year of ransomware in the cyber world, but it wasn’t due to the fact that cybercriminals chose ransomware just because they knew how to attack properly. It’s because of the fact that crypto rose mostly this year, along with the new normal of the digital world. It gave them a new cause to stick to ransomware, thanks to the anonymous payments that can be made using a cryptocurrency.
How does ransomware work?
Ransomware is a malware type that encrypts the victim’s files, whether it’s a random user or an organization, leading to denying them access to those files on their personal devices.
And the key to gaining access is to pay the ransom to the attacker.
How is cryptocurrency helping spread ransomware?
Now we all know that all crypto transactions are untraceable for both receiver and sender, which we call a whole anonymous transaction. The increased demand for crypto in recent years made it easier to buy and sell those virtual coins and get actual money.
With that being said, cryptocurrency became the most preferred way (if not the best) for cybercriminals to get their ransom without being traced and give those organizations access to their files.
How to avoid participating in ransomware parties?
Most articles on the internet teach you the steps on how to give the ransom to the criminals with the minimum losses and without making mistakes to make sure you get your files back. But the question is, why do you need to learn how to make payments to a criminal when you can avoid meeting them and their viruses in the first place?
There are multiple ways where each gives you a generous percentage of protection.
Starting with taking cybersecurity awareness training courses which we call the ultimate layer of protection, followed by multilayers such as the first and most valuable layer that works on the DNS level, which is the first gate between you and the cybercriminal.
A Strong DNS protection would simply turn your wheel each time you try to run by a website that contains viruses. It would also block all crypto and mining websites at which most hackers party at.
Any examples?
Absolutely.
DarkSide ransomware. Its active operations took place in 2020. Its main feature was that it not only encrypted the victim’s data but also deleted it from the affected servers. This is one of the characteristic features of such threats.
In less than a year of work, about $ 100 million were paid in bitcoins. The extortionists received about $10 million by attacking only two companies.
The Brenntag company distributes chemicals. In this case, the DarkSide partners in crime said they had obtained access to the network after purchasing stolen information but didn’t know how the credentials were obtained to begin with. The company paid a $4.4 million ransom in cryptocurrency. Following the ransom payment, Brenntag obtained a decryptor for encrypted files and successfully stopped the cybercriminals from making the company’s stolen information public.
The second company is Colonial Pipeline. The Colonial Pipeline is the largest pipeline system for refined oil products in the U.S. After learning it was “the victim of a cybersecurity attack,” the pipeline operator took some systems offline, temporarily halting pipeline operations and several IT systems. It also contacted an outside cybersecurity firm to conduct an investigation. Finally, they paid the hackers nearly $5 million in cryptocurrency in return for a decryption key to restore its systems.
Conti Ransomware. The main victims of this extortion were healthcare institutions. Its usual methods use phishing attacks to gain remote access to a computer and further spread on the network while simultaneously stealing credentials and collecting unencrypted data. And the most renowned attack was the attack on Ireland’s Health Service Executive, during which the gang ransomed about $ 20 million in cryptocurrency for non-disclosure of the data received.
How to obtain protection?
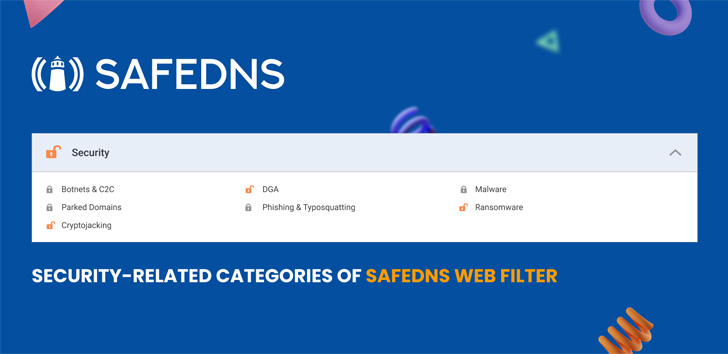
SafeDNS has updated categories having DGA, Cryptojacking and others as part of the Security group, and we definitely recommend trying out threat protection & giving a free 15-day trial of web filtering a go. Stay safe!