Five imposter extensions for the Google Chrome web browser masquerading as Netflix viewers and others have been found to track users’ browsing activity and profit of retail affiliate programs.
“The extensions offer various functions such as enabling users to watch Netflix shows together, website coupons, and taking screenshots of a website,” McAfee researchers Oliver Devane and Vallabh Chole said. “The latter borrows several phrases from another popular extension called GoFullPage.”
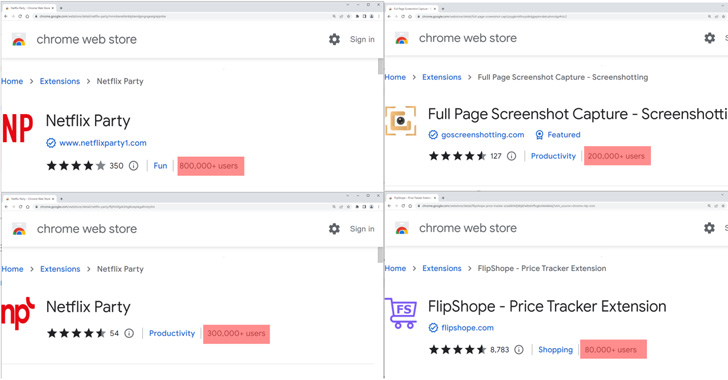
The browser add-ons in question – available via the Chrome Web Store and downloaded 1.4 million times – are as follows –
- Netflix Party (mmnbenehknklpbendgmgngeaignppnbe) – 800,000 downloads
- Netflix Party (flijfnhifgdcbhglkneplegafminjnhn) – 300,000 downloads
- FlipShope – Price Tracker Extension (adikhbfjdbjkhelbdnffogkobkekkkej) – 80,000 downloads
- Full Page Screenshot Capture – Screenshotting (pojgkmkfincpdkdgjepkmdekcahmckjp) – 200,000 downloads
- AutoBuy Flash Sales (gbnahglfafmhaehbdmjedfhdmimjcbed) – 20,000 downloads
The extensions are designed to load a piece of JavaScript that’s responsible for keeping tabs on the websites visited and inject malicious code into e-commerce portals, letting the attackers make money through affiliate programs for purchases made by the victims.
“Every website visited is sent to servers owned by the extension creator,” the researchers noted. “They do this so that they can insert code into eCommerce websites being visited. This action modifies the cookies on the site so that the extension authors receive affiliate payment for any items purchased.”
Also incorporated is a technique that delays the malicious activity by 15 days from the time of installation of the extension to avoid raising red flags.
The findings follow the discovery of 13 Chrome browser extensions in March 2022 that were caught redirecting users in the U.S., Europe, and India to phishing sites and exfiltrate sensitive information.
As of writing, three of the four extensions are still available on the web store, with Netflix Party (mmnbenehknklpbendgmgngeaignppnbe) being the only add-on to be purged. Users of the installed extensions are recommended to manually remove them from their Chrome browser to mitigate further risks.