Microsoft is warning that the BlackCat ransomware crew is leveraging exploits for unpatched Exchange server vulnerabilities to gain access to targeted networks.
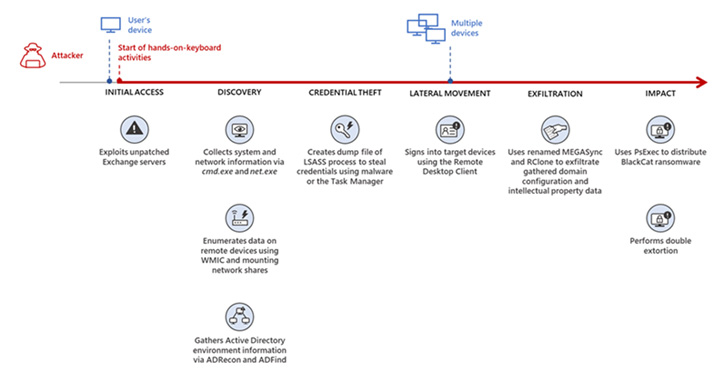
Upon gaining an entry point, the attackers swiftly moved to gather information about the compromised machines, followed by carrying out credential theft and lateral movement activities, before harvesting intellectual property and dropping the ransomware payload.
The entire sequence of events played out over the course of two full weeks, the Microsoft 365 Defender Threat Intelligence Team said in a report published this week.
“In another incident we observed, we found that a ransomware affiliate gained initial access to the environment via an internet-facing Remote Desktop server using compromised credentials to sign in,” the researchers said, pointing out how “no two BlackCat ‘lives’ or deployments might look the same.”
BlackCat, also known by the names ALPHV and Noberus, is a relatively new entrant to the hyperactive ransomware space. It’s also known to be one of the first cross-platform ransomware written in Rust, exemplifying a trend where threat actors are switching to uncommon programming languages in an attempt to evade detection.
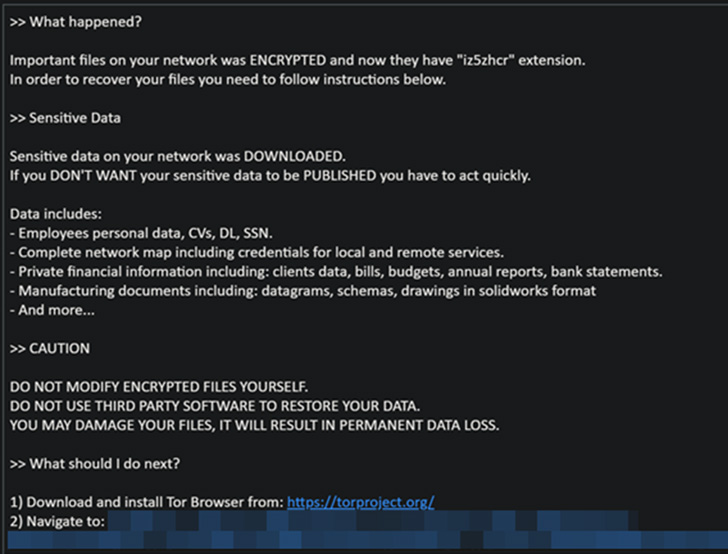
The ransomware-as-a-service (RaaS) scheme, irrespective of the varying initial access vectors employed, culminates in the exfiltration and encryption of target data that’s then held ransom as part of what’s called double extortion.
The RaaS model has proven to be a lucrative gig economy-style cybercriminal ecosystem consisting of three different key players: access brokers (IABs), who compromise networks and maintain persistence; operators, who develop and maintain the ransomware operations; and affiliates, who purchase the access from IABs to deploy the actual payload.
According to an alert released by the U.S. Federal Bureau of Investigation (FBI), BlackCat ransomware attacks have victimized at least 60 entities worldwide as of March 2022 since it was first spotted in November 2021.
Furthermore, Microsoft said that “two of the most prolific” affiliate threat groups, which have been associated with several ransomware families such as Hive, Conti, REvil, and LockBit 2.0, are now distributing BlackCat.
This includes DEV-0237 (aka FIN12), a financially motivated threat actor that was last seen targeting the healthcare sector in October 2021, and DEV-0504, which has been active since 2020 and has a pattern of shifting payloads when a RaaS program shuts down.
“DEV-0504 was responsible for deploying BlackCat ransomware in companies in the energy sector in January 2022,” Microsoft noted last month. “Around the same time, DEV-0504 also deployed BlackCat in attacks against companies in the fashion, tobacco, IT, and manufacturing industries, among others.”