The U.S. Treasury Department on Friday moved to sanction virtual currency mixer Blender.io, marking the first time a mixing service has been subjected to economic blockades.
The move signals continued efforts on the part of the government to prevent North Korea’s Lazarus Group from laundering the funds stolen from the unprecedented hack of Ronin Bridge in late March.
The newly imposed sanctions, issued by the U.S. Office of Foreign Assets Control (OFAC), target 45 Bitcoin addresses linked to Blender.io and four new wallets linked to Lazarus Group, an advanced persistent with ties to the Democratic People’s Republic of Korea (DPRK).
“Blender was used in processing over $20.5 million of the illicit proceeds,” the Treasury said, adding it was utilized by DPRK to “support its malicious cyber activities and money-laundering of stolen virtual currency.”
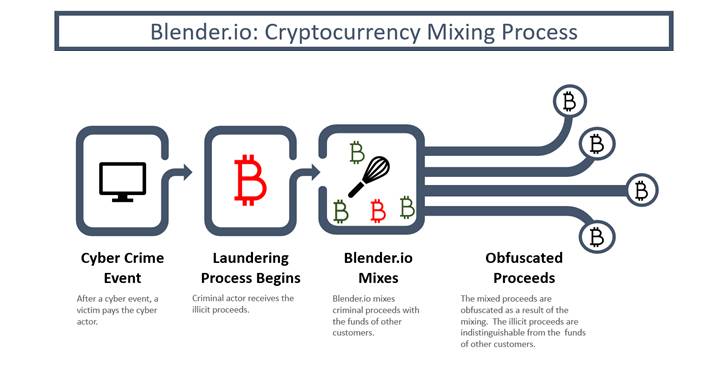
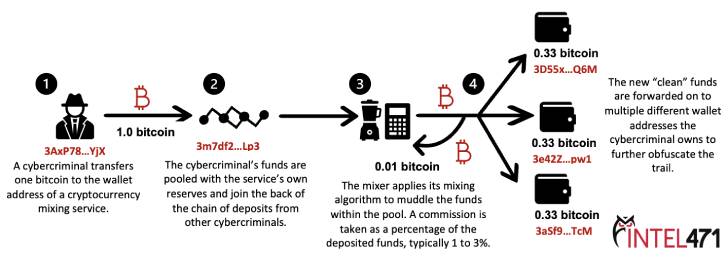
Cryptocurrency mixers, also called tumblers, are privacy-focused services that allow users to move cryptocurrency assets between accounts without leaving a transaction trail by obfuscating their origins.
Mixers like Blender are known to take a “dynamic” service fee that ranges anywhere between 0.6% and 2.5% every time money is transferred to a wallet address under its control. Since its launch in 2017, Blender is estimated to have transferred more than $500 million worth of Bitcoin.
“Through these services, threat actors can achieve their end goal of cashing out and keeping the criminal underground liquid through the trade of illicit goods and services,” Intel 471 noted in a report published in November 2021.
The Ronin Bridge hack saw the state-sponsored cyber hacking group stealing $540 million from a decentralized protocol that permits users to transfer their crypto between Ethereum and the popular blockchain game Axie Infinity.
On April 16, the Treasury Department blocklisted the Ethereum wallet address that received the stolen digital currency, although by then the Lazarus Group had managed to launder 18% of the siphoned funds (about $97 million) through centralized exchanges and an Ethereum mixing service called Tornado Cash.
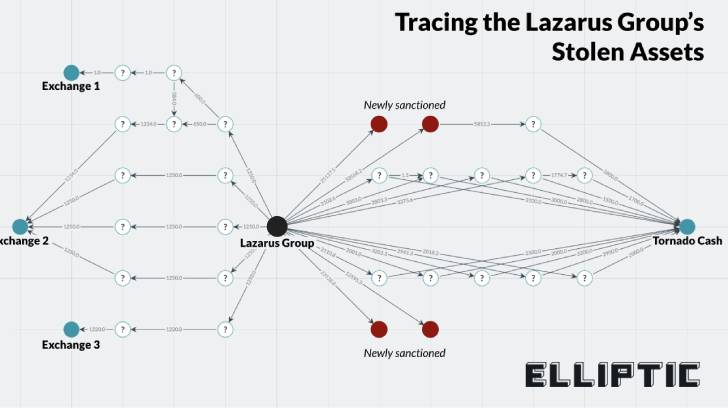
Over the past two weeks, around $273.9 million of Ether was sent to four of the newly-sanctioned addresses, according to blockchain analytics firm Elliptic, with one of those addresses already moving $37 million through Tornado Cash, leaving behind $236 million.
“The transactions involved amounts significantly larger than their previous laundering efforts,” the company said. “The ramping up of laundering efforts in this manner potentially reflects a growing desperation by the hackers.”
Furthermore, the sanctioning of Blender is evidence that the “Lazarus Group had moved some of the stolen funds into Bitcoin,” Elliptic pointed out.
On top of that, Blender is also said to have helped a number of the Russia-aligned ransomware gangs launder their money, including TrickBot, Conti (formerly Ryuk), Sodinokibi (aka REvil), and Gandcrab.
In the midst of all this, crypto exchange Binance on April 22 revealed that it had managed to recover $5.8 million worth of the Axie Infinity stolen funds that were spread across 86 accounts.
The development comes a month after the Treasury sanctioned virtual currency exchange Garantex for assisting criminal actors in laundering over $100 million in ill-gotten funds.
Last year, the department penalized two cryptocurrency exchanges SUEX and CHATEX for facilitating financial transactions for ransomware actors and cashing out the money extorted from victims.
In recent years, North Korea has been attached to a string of cyber-enabled heists from cryptocurrency exchanges and financial entities as a way of getting around international sanctions and generating revenue for its nuclear weapons program.
Last month, U.S. cybersecurity and intelligence agencies warned of a new set of cyberattacks carried out by the Lazarus Group targeting blockchain companies with rogue cryptocurrency apps.
“Virtual currency mixers that assist illicit transactions pose a threat to U.S. national security interests,” said Brian E. Nelson, undersecretary of the Treasury for Terrorism and Financial Intelligence.
“We are taking action against illicit financial activity by the DPRK and will not allow state-sponsored thievery and its money-laundering enablers to go unanswered.”